POWER SHELL: A shell is special user program which provide an interface to user to use operating system services. Shell accept human readable commands from user and convert them into something which kernel can understand. It is a command language interpreter that execute commands read from input devices such as keyboards or from files. The shell gets started when the user logs in or start the terminal.
It is classified into 2 types
1)command line shell: Shell can be accessed by user using a command line interface. A special program called Terminal in linux/macOS or Command Prompt in Windows OS is provided to type in the human readable commands such as “cat”, “ls” etc. and then it is being execute.
2) graphical shell: Graphical shells provide means for manipulating programs based on graphical user interface (GUI), by allowing for operations such as opening, closing, moving and resizing windows, as well as switching focus between windows.
There are several shells are available for Linux systems like –
BASH (Bourne Again Shell)– It is most widely used shell in Linux systems. It is used as default login shell in Linux systems and in macOS. It can also be installed on Windows OS.
CSH (C Shell)– The C shell syntax and usage are very similar to the C programming language.
KSH (Korn Shell)– The Korn Shell also was the base for the
POSIX (portable operating system interface) Shell standard specifications etc.
Each shell does the same job but understand different commands and provide different built in functions.
Why do we need shell scripts?
1)To avoid repetitive work and automation
2)System admins use shell scripting for routine backups
3)System monitoring
4)Adding new functionality to the shell.
-
Advantages of shell scripts
1)The command and syntax are exactly the same as those
directly entered in command line, so programmer do not need
to switch to entirely different syntax
2)Writing shell scripts are much quicker
3)Quick start
4)Interactive debugging etc.
-Disadvantages of shell scripts
1)Prone to costly errors, a single mistake can change the
command which might be harmful
2)Slow execution speed
3)Design flaws within the language syntax or implementation
Not well suited for large and complex task
Provide minimal data structure unlike other scripting
languages. etc
Shell commands:
1)cat: It is generally used to concatenate the files. It gives the output on the standard input. It creates the file with content.
syntax: $ cat employee name
2)more: It is a filter for paging through text one screenful at a time.
syntax: $ more employee name
3) less: It is used to viewing the files instead of opening the file. Similar to more command but it allows backward as well as forward movement.
syntax: $ less employee.txt
4) head: It is used to print the first N lines of a file. It accepts N as input and the default value of N is 10.
syntax: $ head employee. txt
We can give N value so that it prints the number of lines given.
5) tail: Used to print the last N-1 lines of a file. It accepts N as input and the default value of N is 10.
syntax: $ tail N-1 employee.txt
File and directory manipulation commands:
6) mkdir: mkdir function used to create directory in the current directory or using mkdir-p, it creates directory at the specified path.
7) cp: This command will copy the files and directories from the source path to the destination path. It can copy a file/directory with the new name to the destination path. It accepts the source file/directory and destination file/directory.
8) mv : Used to move the files or directories. This command’s working is almost similar to cp command but it deletes a copy of the file or directory from the source path.
9) rm : Used to remove files or directories.
10) touch: It is used to create a file without any content. The file created using touch command is empty. This command can be used when the user doesn’t have data to store at the time of file creation.
$ touch employeename
touch -a: This command is used to change access time only. To change or update the last access or modification times of a file touch -a command is used.
touch -c : This command is used to check whether a file is created or not. If not created then don’t create it. This command avoids creating files
touch -c employee.txt
touch -c-d: This is used to update access and modification time.
touch -c-d employee.txt
touch -m : This is used to change the modification time only. It only updates last modification time.
touch -m employeename
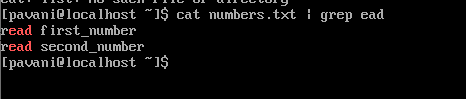
11) grep: The grep filter searches a file for a particular pattern of characters, and displays all lines that contain that pattern.
-c: This prints only a count of the lines that match a
pattern
-h: Display the matched lines, but do not display the
filenames.
-i: Ignores, case for matching
-l: Displays list of a filenames only.
-n: Display the matched lines and their line numbers.
-v: This prints out all the lines that do not matches the
pattern
-e exp: Specifies expression with this option. Can use
multiple times.
-f file: Takes patterns from file, one per line.
-E: Treats pattern as an extended regular expression (ERE)
-w: Match whole word
-o: Print only the matched parts of a matching line,
with each such part on a separate output line.
12) sort: SORT command is used to sort a file, arranging the records in a particular order. By default, the sort command sorts file assuming the contents are ASCII. Using options in the sort command can also be used to sort numerically.
-r Option: Sorting In Reverse Order: You can perform a reverse-order sort using the -r flag. the -r flag is an option of the sort command which sorts the input file in reverse order i.e. descending order by default.
-n Option: To sort a file numerically used –n option. -n option is also predefined in Unix as the above options are. This option is used to sort the file with numeric data present inside.
-nr option: To sort a file with numeric data in reverse order we can use the combination of two options as stated below.
-k Option: Unix provides the feature of sorting a table on the basis of any column number by using -k option.
-c option: This option is used to check if the file given is already sorted or not & checks if a file is already sorted pass the -c option to sort. This will write to standard output if there are lines that are out of order. The sort of tool can be used to understand if this file is sorted, and which lines are out of order
13) Wc: It is used to find out number of lines, word count, byte and characters count in the files specified in the file arguments.
By default, it displays four-columnar output. First column shows number of lines present in a file specified, second column shows number of words present in the file, third column shows number of characters present in file and fourth column itself is the file name which are given as argument.
syntax: $ wc file name
-c: This option displays count of bytes present in a file. With this option it displays two-columnar output, 1st column shows number of bytes present in a file and 2nd is the file name.
-m: Using -m option ‘wc’ command displays count of characters from a file.
-L: The ‘wc’ command allow an argument -L, it can be used to print out the length of longest (number of characters) line in a file.
14) cut: It can be used to cut parts of a line by byte position, character and field. Basically, the cut command slices a line and extracts the text. It is necessary to specify option with command otherwise it gives error. If more than one file name is provided, then data from each file is not precedes by its file name.
syntax: cut filename
-b(byte): To extract the specific bytes, you need to follow -b option with the list of byte numbers separated by comma.
-c (column): To cut by character use the -c option. This selects the characters given to the -c option.
-f (field): -c option is useful for fixed-length lines. Most unix files doesn’t have fixed-length lines
15) echo: Echo is a command in shell scripting which is a built-in command used to display a variable, result of an expression, string, number, text, any useful information in the programming, etc. can be displayed using echo command in shell scripting. It is available in most of the programming languages and most commonly used in shell scripting where bash and c shells are mostly used. This command can also be used to display the commands or arguments sent to a shell program also.
syntax echo string name
a) To display a text or string on the console
echo hello world
b) To display a variable value on the console
x=5 echo $x
c) To remove spaces from a given string and display on the
console
echo -e " this/ is/ my/ world"
d) To print all files or folders in the current directory
echo *
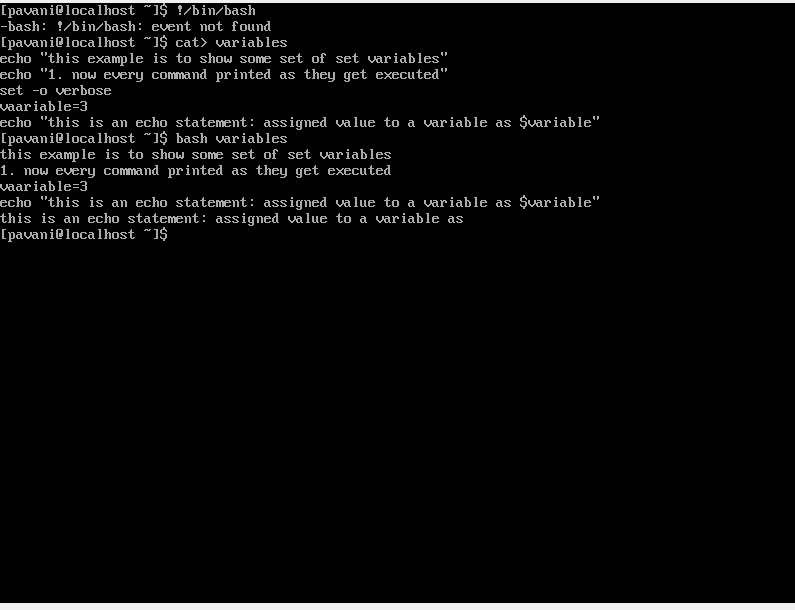
16) Variables: The variables which are a type of parameter are generally managed by the users or the system. We can take an example of $var which is a variable parameter. The system sets $var, but this variable parameter can be written by the user.
17) special parameters: The special parameters are read-only which are maintained by the shell. The special parameters are with a predefined meaning. Below are the various special parameters:
a) $#: Its parameter represents the total number of
arguments passed to the script.
b) $0: This parameter represents the script name.
c) $n: This parameter represents the arguments
corresponding to a script when a script is invoked
such $1 $2…etc. $1, $2…etc are called positional
parameters.
d) $: This parameter describes the positional parameters
to be distinct by space. For example, if there are
two arguments passed to the script, this parameter
will describe them as $1 $2.
e) $$: This parameter represents the process ID of a
shell in which the execution is taking place.
f) $!: This parameter represents the process number of
the background that was executed last.
g) $@: This parameter is similar to the parameter $.
h) $?: This parameter represents exit status of the last
command that was executed. Here 0 represents
success and 1 represents failure.
i) $_: This parameter represents the command which is
being executed previously.
j) $-: This parameter will print the current options
flags where the set command can be used to modify
the options flag.
syntax: $ cat program.sh
echo "The File Name is: $0"
echo "The First argument is: $1"
echo "The Second argument is: $2"
$ sh program.sh ab cd
The File Name: program.sh
The First argument is: ab
The Second argument is: cd
18) pwd: pwd‘ stands for ‘Print Working Directory ‘. As the name states, command ‘pwd‘ prints the current working directory or simply the directory user is, at present. It prints the current directory name with the complete path starting from root (/). This command is built in shell command and is available on most of the shell – bash, Bourne shell, ksh, zsh, etc.
syntax: pwd filename
19) Ifconfig: It is used to know the kernel-based interface for networks. This command is mainly used at the boot time to know and set up interfaces as and when necessary. Otherwise, ifconfig command only comes into a role when some system tuning, or some debugging is needed.
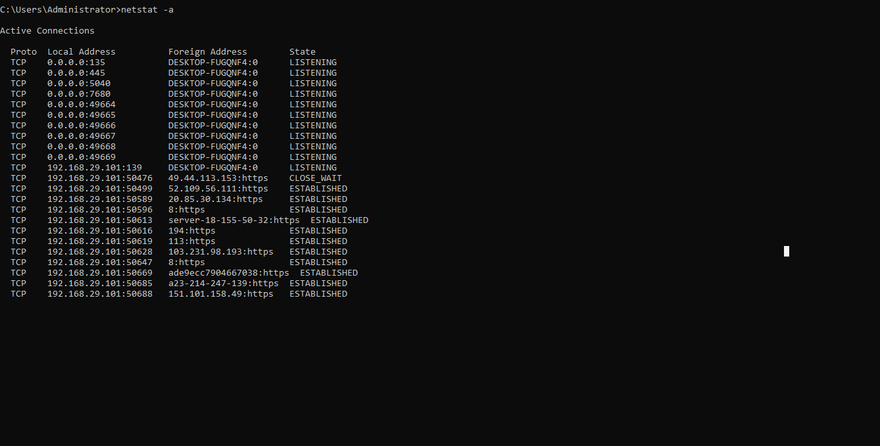
20) Netstat: This is one major command which tops the list of shell scripting commands. Netstat is used to display the network-related information like those of routing tables, network connections, masquerade connections, interface statistics, multicast memberships, etc. the suffix –a is used to list all network ports.
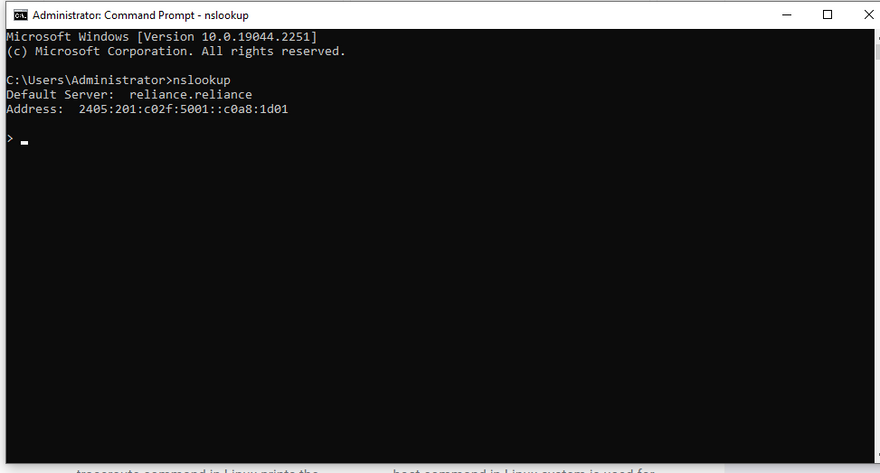
21) nslookup: his shell scripting command is mainly used by infra management and techOps/DevOps team as they are required to deal with a deep level of networking. It is a network utility-based command which displays the information of internet servers. It queries Domain Name Server and thereby fetches the result related to server name information.
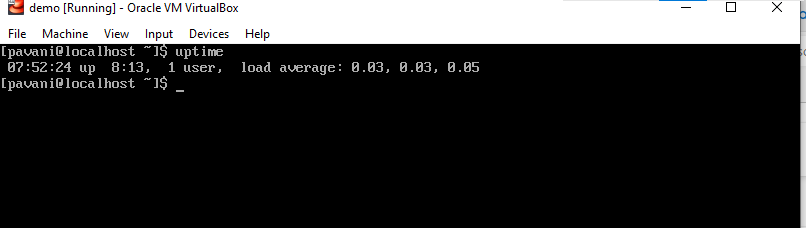
22) Uptime: This is a command which is used to keep a track of any malicious or any unusual activity that might be affecting your system. Uptime is used to know what actually happened when the server was left unattended.
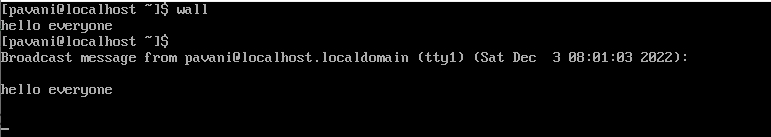
23) Wall: This is one of the most essential shell scripting commands, especially for an administrator as this can be used to broadcast a message to n number of people, to all those who have their mesg permission set to yes. The message is then provided as the argument to a wall or it is also sent as standard input for a wall.
24) Mesg: This command lets you take the control that whether the people can make use of the “write” by providing an option of y|n.
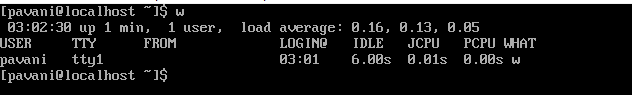
25) w: This command is though just a one-letter command can make wonders possible as it is a combination of who and uptime commands which are given in a sequence immediately after the other.
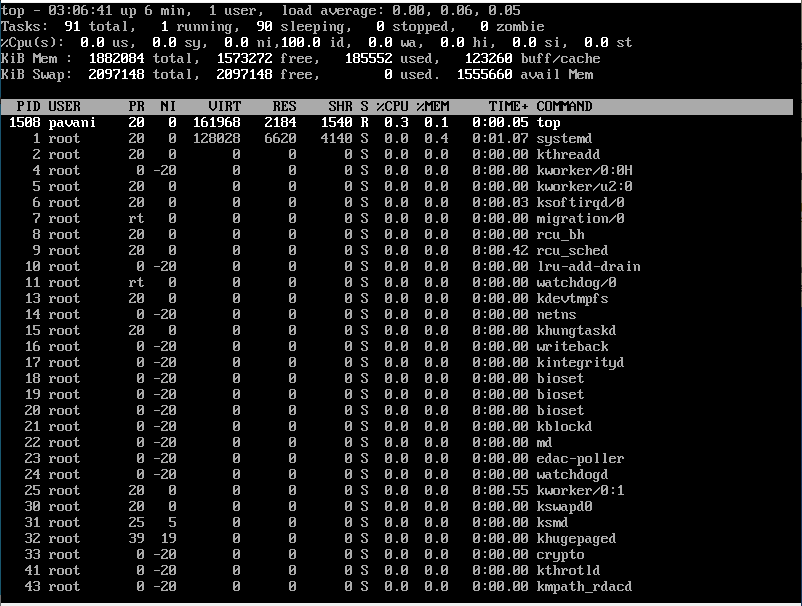
26) top: It is used to display all the processes of a CPU. This command is best known as it refreshes itself and continuously displays all the CPU processes which are up and running at one point of time until and unless an interrupt command is given.
27) Arithmetic operator
At the very first type of operator, we have an arithmetic operator. This is assumed to be an extension of the operators we use in mathematics as well. We are already well aware of these operators, but just for the sake of listing the different operators we have:
a) Addition operator (+): This operator is for the addition
of
2 operands.
Subtraction operator (-): This operator is for the
subtraction of 2 operands
Multiplication operator (*): This operator is for
multiplication of 2 operands
The division operator (/): This operator is for the division
of 2 operands. It gives only the
quotient.
The modulus operator (%): This operator is for estimating
the remainder when one operand is
divided by the other.
Increment Operator (++): This operator is for incrementing the
operand’s value by 1.
Decrement Operator (–): This operator is for decrementing the operand’s value by 1.
28) Relational operator
As the name suggests these operators work on determining the relation between 2 operands. In the case of the relational operator, the output is either true or false, irrespective of the type of operator we would be using. Some of these relational operators are:
a) ‘==’ Operator: This operator evaluates the two operands by equating them and process the output as true if they are equal and false if they are not. These operators may be used for integers as well as strings. For strings, one would use it with [[ for pattern matching.
b) ‘!=’ Operator: This operator evaluates the two operands by checking the inequality and process the output as true if they are equal and false if they are not. Again, for this operator, one can use it for integer as well as on strings. Essentially for string, this operator would return true if the strings don’t match.
c) ‘< ‘Operator: This operator checks for the value of the first operand’s to be less than the second one and return true if that’s the case and for vice versa, it would return false. This is not so widely used in strings!
d) ‘<=’ Operator: This operator checks for the value of the first operand’s to be less than or equal to the second one and return true if that’s the case and for vice versa, it would return false. This is not present for strings.
e) ‘>’ Operator: This operator checks for the value of the first operand’s to be greater than the second one and returns true if that’s the case and false for vice versa. Not quite widely used for strings.
f) ‘>=’ Operator: This operator checks for the value of the first operand’s to be greater than or equal to the second one and return true if that’s the case and false for vice versa. This option is not available for strings.
29) Logical Operator: This set of operators are for analyzing 2 or more set of conditions and return true based on some conditions for each of them.
a) Logical AND operator: Only in case of both the set of conditions be true, this operator will process true, else false.
Logical OR operator: In any case of either of the conditions in any one of the sides be true, this operator will output out TRUE as well.
b) NOT operator: This operator reverses the output coming out of the condition and shows that as the output.
30) Bitwise Operators
These operators are pretty much similar to the logical operators except the difference that these operators work on bit patterns. One essential thing to keep in mind is the << or >> are not for less than or greater than, but something explained below.
- AND (&)
- OR (|)
- XOR (^)
- Compliment
- Shift left (<<)
- Shift right (>>) 31) File operators: The final piece of the puzzle is the file operator, essentially used for testing the file properties:
- -b: Checks if the file is a block special file or not.
- -c: Checks if the file is a character special file or not.
- -d: Checks if the name of the directory exists or not.
- -e: Checks if the file exists or not
- -r: Checks if the file has “read” access or not.
- -w: Checks if the file has “write” access or not.
- -x: Checks if the file has “execute” access or not.
- -s: Checks for the file size and returns if the size is greater than 0.
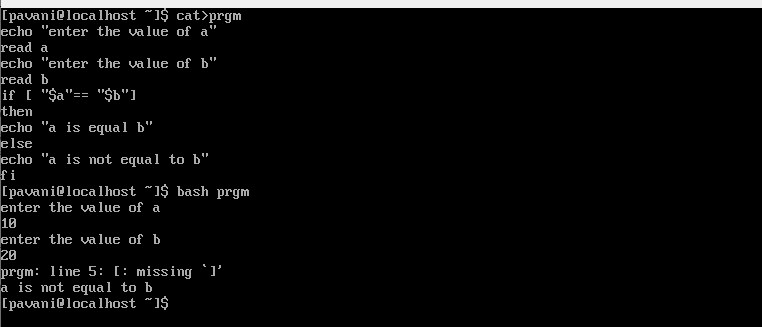
32) if else: "If else” is a conditional or control statement in the programming language. This plays a different action or computation depending on whether the condition is true or false.
“if-else” is dealing with two-part of the executions. If the “if-else “condition is “true” then the first group of statements will execute. If the condition is “false” then the second group of statements will execute.
syntax:
if [ condition ]
then
Statement 1 (first Group)
else
Statement 2 (second Group)
fi
33) while loop: While loop provides a way to execute the same program by checking a condition when the condition satisfies the program will execute otherwise it won’t execute and the process repeats until the condition fails to meet.
syntax:
while [condition]
do
command1
command2
done
34) Local variables: These types of variables are present only within the running instance of the shell. In case there are child processes that are started by the shell script, the local variables might not be accessible to the child processes.
35) Environment variables: These types of variables are the ones that are accessible to any child process the shell script has run, unlike the local variables.
36) Shell variables: In certain cases, the shell might be required to set some variables in order to smooth the execution of the script and these variables are known as shell variables.
a) allexport: This variable is used for marking those variables and functions which are to be exported to the environment. Until and unless we specify this variable, all variables are local and when this is turned on all variables and functions will be transported to the subshell.
b) braceexpand: This variable performs brace expansion. This is a method used for generating strings at the command line. Mainly used for reusing a file path which is quite long to be written again in bash.
c) emacs: Using this variable one can use emacs styled editing interface in the command line.
d) errext: This variable is to allow shell scripts to immediately exit if there is a non-zero status out of the script.
e) errtrace: Traps are cool techniques for implementing error handling when using bash. In this any errors which can be trapped is inherited by shell functions or substitutions in command.
f) functrace: Like the previous variable, this variable helps traps on DEBUG and RETURN to be inherited by shell functions or substitutions in command.
g) hashall: This variable helps in remembering the location of commands as and when they are looked up for execution.
h) histexpand: This enables shell scripts to use! style history substitution. One would have stumbled across the usage of ! is a sentence and get an error. This is because of the! style history substitution. If this annoys one, one can surely set off this variable.
i) ignoreeof: If you want to use Ctrl + D in windows to keep your session or script running, and not leave the shell, we would need to use this variable. In short, when the shell reads EOF, it will not exit. For example, if you set IGNOREEOF=18, one would have to press Ctrl+D 18 times to leave the shell.
j) history: This is to enable command history. You would have noticed these while pressing up button you can see the previous commands you have used.
k) monitor: This variable enables the shell script to have job control during execution.
l) noclobber: This variable enables bash to not overwrite an existing file using >, >& operators.
m) noexec: Using this variable one would just read the commands and not execute them. This is widely used for doing syntax checks in the code.
n) noglob: This variable option is used for disabling a file name generation or in other words, pathname expansion.
o) nounset: In the case of parameter expansion, any unset parameters are treated as an error when this variable is used in the set command.
p) onecmd: This variable as the name suggests executes one command and then exits.
q) physical: When this variable is used, symbolic links don’t work. For example, if one needs to change the directory, they can’t use the cd as a physical directory structure would be used.
r) pipefail: When this variable is used, the pipeline is returned with a value which is the last command to exit with a non-zero status. This is to understand the last point of error in the code.
s) posix: When used, the bash behavior is changed making default operation different from POSIX standard.
t) privileged: This allows security by running the shell script without inheriting it from the environment and hence the environment variables are not accessible.
u)verbose:: This allows the input lines of the shell to be printed as they are read.
v) vi: This is to start a vi styled editing interface.
w) xtrace: This allows all the commands and their arguments to be printed as they get executed. Widely used for tracing back to an error in case many shell processes are run.
In the output you would see that all the command post point 1 gets printed as they are executed.
37) ls: ls is the command which is responsible for listing the folders and files present in a particular directory. This shell scripting command is often appended with other commands such as –ltr or –lrt, etc. depending upon the need.
syntax: ls
38) Piping (|): This is another very basic command that is used to fetch the output received from one command straight away into another. This symbol called pipe can most often be seen along with the grepping command. At some places, this piping can also be said to be chaining.
syntax: cat filename |grep string
39) Dig: This is another Intermediate command which is used to query the Domain name servers and provide information about the host addresses, nameservers, mail exchanges, etc. related information. It is mostly used to query a single given host.
40) Rename: this command is used to rename a file name
41) chown: Different users in the operating system have ownership and permission to ensure that the files are secure and put restrictions on who can modify the contents of the files.
Each user has some properties associated with them, such as a user ID and a home directory. We can add users into a group to make the process of managing users easier.
A group can have zero or more users. A specified user can be associated with a “default group”. It can also be a member of other groups on the system as well.
Ownership and Permissions: To protect and secure files and directory we use permissions to control what a user can do with a file or directory. It uses three types of permissions:
Read: This permission allows the user to read files and in directories, it lets the user read directories and subdirectories stores in it.
Write: This permission allows a user to modify and delete a file. Also it allows a user to modify its contents (create, delete and rename files in it) for the directories. Unless the execute permission is not given to directories changes does do affect them.
Execute: This permission on a file allows it to get executed. For example, if we have a file named php.sh so unless we don’t give it execute permission it won’t run.
Types of file Permissions:
User: This type of file permission affects the owner of the file.
Group: This type of file permission affect the group which owns the file. Instead of the group permissions, the user permissions will apply if the owner user is in this group.
Other: This type of file permission affects all other users on the system.
syntax:
chown [OPTION]… [OWNER] [: [GROUP]] FILE…
chown [OPTION]… –reference=RFILE FILE…
Example: To change owner of the file:
chown owner_name file_name
42) chgrp: chgrp command is used to change the group ownership of a file or directory. All files belong to an owner and a group. You can set the owner by using “chown” command, and the group by the “chgrp” command.
Syntax:
chgrp [OPTION]… GROUP FILE…
chgrp [OPTION]… –reference=RFILE FILE…
43) chmod: the chmod command is used to change the access mode of a file.
Syntax :chmod [reference][operator][mode] file...
The references are used to distinguish the users to whom the permissions apply i.e. they are list of letters that specifies whom to give permissions.
Reference Class Description
u owner file's owner
g group users who are members of
the file's group
o others users who are neither the
file's owner nor members of
the file's group
a all All three of the above, same as ugo
The operator is used to specify how the modes of a file should be adjusted. The following operators are accepted:
Operator Description
Adds the specified modes to the specified classes
Removes the specified modes from the specified classes
= The modes specified are to be made the exact modes for the specified classes
The modes indicate which permissions are to be granted or removed from the specified classes. There are three basic modes which correspond to the basic permissions:
r Permission to read the file.
w Permission to write (or delete) the file.
x Permission to execute the file, or, in
the case of a directory, search it.
44) IFS: IFS stands for Internal Field Separator. It is an environment variable that defines a field separator. By default, space, tab, and newline are considered as field separators
45) env: env is used to either print environment variables. It is also used to run a utility or command in a custom environment.
syntax: env [OPTION]... [-][NAME=VALUE]... [COMMAND [ARG]...]
a) Without any argument: print out a list of all environment variables.
b) u or –unset: remove variable from the environment
$ env -u variable_name
46) kill: This command is a built-in command which is used to terminate processes manually. kill command sends a signal to a process which terminates the process. If the user doesn’t specify any signal which is to be sent along with kill command then default TERM signal is sent that terminates the process.
a) kill -l: To display all the available signals
Syntax: $kill -l
b) ill pid : To show how to use a PID with the kill command.
Syntax: $kill pid
c) kill -s: To show how to send signal to pro
Syntax: kill {-signal | -s signal} pid
d) kill -L:This command is used to list available signals
in a table format.
Syntax: kill {-l | --list[=signal] | -L | --table}

Top comments (0)