Question
Which is readable format plaintext or chipertext?
Give a example of encryption and dencryption and Hashing?
Which is more secure between Hashing and Encryption?
Which is reversible between Hashing and Encryption
Real life example of Public key cryptography and Hashing
What is Keypair
Sender encrypt the data with the receiver’s public key or sender public key ?
What is Digest ?
Hashing is an example of one-way function or two-way function.
Solution
1.
readable format==> plaintext
$plaintext = "Your sensitive message";
not readable format==> chipertext or encrypted_text
chipertext=$encrypted_text = "qnHWqq1mElDqW2RCepH14VriPf5s2Q==";
2.
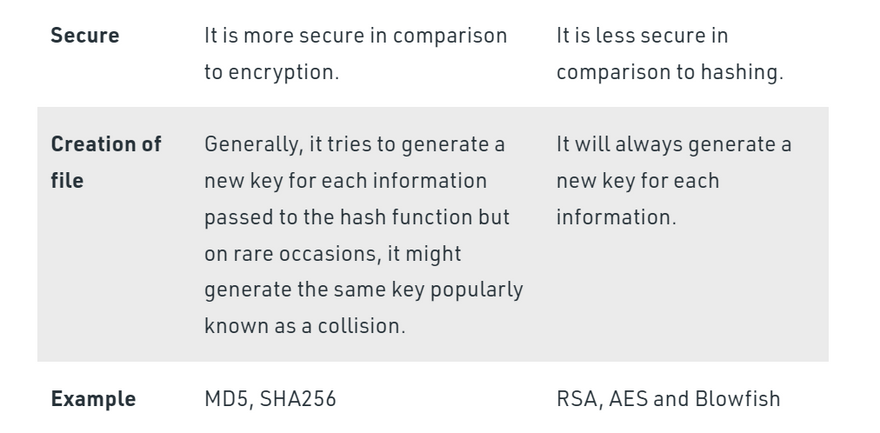
encryption ==>RSA, AES, and Blowfish
Hashing==>MD5, SHA256
3.
Hashing is more secure
4.
Encryption==>reversible
Hashing==>irreversible as we cannot convert again into plaintext
5.
Hashing==>fingerprint
Message Digest
Password Verification
Data Structures(Programming Languages)
Compiler Operation
Rabin-Karp Algorithm
Linking File name and path together
Game Boards
Graphics
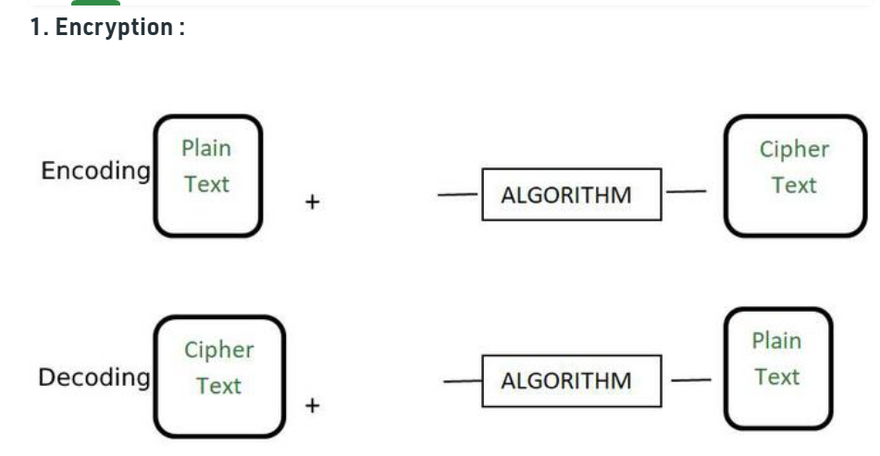
Encryption
- SSL Certificates Browsing the internet is an activity that most of us do every day. On the internet, encryption comes in the form of Secure Sockets Layers (SSL) certificates. SSL protection is a security technology feature that website owners can buy in order to increase the security of their site.
You can recognize an encryption protected website from the green padlock and the “HTTPS” in the URL.
SSL protection establishes an encrypted communication channel between a browser and a web server.
An active SSL certificate on a web server is especially useful on websites where visitors enter sensitive information such as credit card information, phone numbers, IDs, etc. That means that all the data that is being transferred between a browser and a web server is encrypted for security and privacy reasons.
For example, if you’ve seen awesome shoes on a webshop, you’ll need to enter your shipping details and payment information. On a SSL secured website, this means that all of your sensitive information is encrypted, so that the readable text that you entered will be encrypted into ciphertext (unreadable text). This makes online shopping very safe!
- Cash Withdrawal From ATMs Banks use Hardware Security Module (HSM) encryption methods in order to protect your PIN and other banking information while the transaction is in transit in the network.
HSM encryption comes in many different types but, in essence, it’s function is to encrypt the 4 to 6 digit PIN of every person that uses the ATM. Then, the PIN is decrypted at the HSM side in order to execute and validate the transaction or money withdrawal.
This encryption method ensures that hackers won’t be able to get their hands on your PIN in case they intercept the network data in transit.
- Email Webmail applications such as Gmail and Hotmail provide the earlier explained SSL encryption (HTTPS) in order to protect the user. However, it’s important to note that SSL encryption does not encrypt the text in emails.
Thus, without going too deep into the technical jibber-jabber, the NSA for example, would still be able to intercept your emails in readable text format.
Privacy-minded users are increasingly more often leaning towards end-to-end encryption email providers such as Protonmail and CounterMail. Millions of users have already made the switch to similar encryption protected email providers.
This email software ensures that every sent and received email is encrypted into ciphertext. So, even when the email is intercepted, it’s unreadable to anyone without the decryption key.
- File Storage Popular file storage platforms such as Dropbox and Google Drive, with 500 million and 800 million users respectively, greatly emphasize on the security of the platform.
Obviously, the platform wouldn’t be used by millions of users – individuals and businesses – if it didn’t provide a secure environment to store important files, photos and videos.
That means that every file is encrypted into cipherdata in order to protect the users. Dropbox even stated in their security protocol that they break every piece of data into multiple other pieces and encrypt these smaller pieces of data one by one.
Both platforms protect files in transit between servers and apps, but also at rest (when it’s stored on their server). Which is incredibly helpful for all these millions of users, to be sure all their important data is safely stored online.
- Messenger Apps (WhatsApp) According to TechCrunch, the popular messenger application WhatsApp had 1.5 billion active monthly users in Q4, 2017. Which is good for 60 billion messages sent per day.
It comes to no surprise that WhatsApp values the privacy of its users, which is why WhatsApp implemented complete end-to-end encryption in their messenger application. That means that all your messages, photos, videos, voice messages and files are secured.
Only the person you’re communicating with is able to read what you’re sending. End-to-end encryption also means that even WhatsApp is not able to read any messages, because it’s stored on their server in encrypted format.
And the best thing is that WhatsApp automatically encrypts every message by default and there’s no way to turn off the encryption.
6.
combination of public & private keys is called a key-pair
7.
Sender would always start with the receiver’s public key for encryption
.
8.
The output of a hash function is of fixed size ( say, a 64-character text). The output is also called a digest
.
9.
hash function is also called a one-way function as it is irreversible as we cannot convert again into plaintext
.
Encryption and hashing are the two terms used widely in cryptography. In this article, we will learn what is the difference between encryption and hashing.
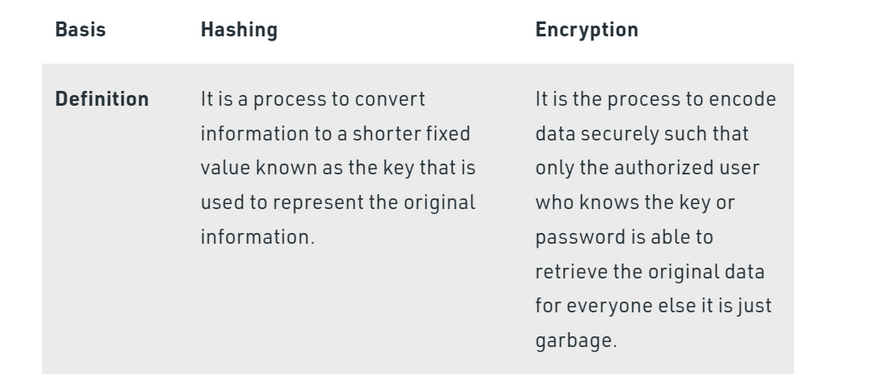
Encryption is the process of converting a normal readable message known as plaintext into a garbage message or not readable message known as Ciphertext. The ciphertext obtained from the encryption can easily be transformed into plaintext using the encryption key. Some of the examples of encryption algorithms are RSA, AES, and Blowfish.
<?php
$plaintext = "Your sensitive message";
$cipher = "AES-128-CTR";
$key = "Blog Desire";
$iv = "1232434565432123";
$ciphertext = openssl_encrypt($plaintext, $cipher, $key, $options=0, $iv);
echo $ciphertext;
<?php
$encrypted_text = "qnHWqq1mElDqW2RCepH14VriPf5s2Q==";
$cipher = "AES-128-CTR";
$key = "Blog Desire";
$iv = "1232434565432123";
$original_text = openssl_decrypt ($encrypted_text, $cipher, $key, $options = 0, $iv);
echo $original_text;
Public Key Cryptography
- When you receive a package from Amazon, you want to make sure that : a) Indeed Amazon has sent the package and not some bio-terrorist (signing) b) While in transit, nobody else knows what’s in the package (confidentiality) c) The package is not tampered while in transit (tamper-proofing)
- A network transaction involves : a sender, the network pipe and a receiver. A network transaction happens when a unit of data is moved at a particular point of time. Securing a transaction is of high importance. By securing, we mean that confidentiality and tamper-proofing is taken care of.
- Public key cryptography solves the problem of signing, confidentiality and tamper-proofing of network transactions. All in one neat package.
- Confidentiality is achieved by garbling (mixing up) the data in motion.
- A key is a number or a function that can be used to garble a piece of data. This is called encryption. A key can be used to reconstruct the original data from the garbled data. This is called decryption.
- If you use the same key for both encryption and decryption, then it is called symmetric cryptography. These key is private and is held only by the sender and the receiver.
- With symmetric keys, the data can be encrypted. But how would the sender transfer the key to the receiver? There is no practical/scalable way to do this on the network. Thus, key-sharing is a fundamental drawback of symmetric key encryption and it is not used widely.
- Asymmetric cryptography was established to fix the key-sharing problem in cryptography. Here, you use one key for encryption and a different key for decryption.
- Public key cryptography is basically asymmetric encryption with some additional steps.
- In public key cryptography, there are 5 elements : the actual data, sender’s public key, sender’s private key, receiver’s public key and receiver’s private key.
- A public key is announced and known to the world. A private key is stored in the owner’s mind or in a physical/digital safety locker. Private key is otherwise called a secret key.
- At a given point, a sender can make use of 3 keys : sender’s private key, sender’s public key and the receiver’s public key. Similarly, a receiver can make use of receiver’s private key, receiver’s public key, and the sender’s public key. Needless to say, one party can never know another party’s private key.
- The*combination of public & private keys is called a key-pair*. This pair can be generated on your computer’s command line program. Some prime-number mathematics goes behind the key-pair generation(the details are beyond the scope of this write-up). In a nutshell, it is real hard (time consuming) to know someone’s private key using their public key (through guess work and other means)
- It does not matter the order in which you use the keys. You can encrypt a piece of data with a public key, but the decryption can be done only with its corresponding private key. The reverse is also true. You can encrypt data with your private key. But it can be decrypted only with your public key.
- A sender would always start with the receiver’s public key for encryption. The receiver would use its own (receiver) private key for decryption. This fulfills the goal of confidentiality (data scrambling & reconstruction). So confidentiality is achieved by using the receiver’s key-pair.
- But the receiver still does not know who sent the data. It could have been sent by a hacker. So the sender needs to let the receiver know that the data is indeed sent by the sender. This process is called signing. Signing is done by attaching a small piece of additional data called the signature. (Note that a signature without data is useless). The next few steps might overwhelm a bit(as the topic itself cannot be oversimplified). Please feel free to read with a paper and pencil.
- A signature is created by using the sender’s key-pair. In this process, the sender first encrypts the data with sender’s private key. Lets call the result sender-privkey-encrypted-data (this is the signature). Now sender combines the signature and the data. Let’s call this “data + sender-privkey-encrypted-data”.
- The sender will again encrypt the “data + sender-privkey-encrypted-data” with the receiver’s public key. Lets call this result receiver-pubkey-encrypted-data. This “wrapped and encrypted” data is sent over the network (note that message in transit is twice the intended size, and this problem is “fixed” later at point 22). No intruder can decipher this message as only the receiver’s private key can decrypt receiver-pubkey-encrypted-data.
- The receiver would now take the receiver-pubkey-encrypted-data and decrypt it (for the first time) with the receiver’s private key. The result would be “data + sender-privkey-encrypted-data”. Receiver alone can see the “data”, hence confidentiality is achieved.
- The receiver would now decrypt (for the second time) only the “sender-key-encrypted-data” using the sender’s public key. Let’s call this “data2”.
- If the “data2” matches with “data”, then receiver is sure that the message was indeed sent by the sender (because only sender’s private key could have encrypted “data” to create “data2”).
- Data matching also ensures that message is not corrupted. Hence, tamper-proofing is also taken care of.
- Overall, a double-encryption process is used. The sender needs to sign (with sender’s private key ) and sender needs to encrypt (with receiver’s public key).
- Note that at point 16 we mentioned that the message in transit is twice the size of the intended message. This is because of the signature “sender-privkey-encrypted-data”. The size of the signature can be compressed by hashing the actual data and then encrypting only the hash. Hence, instead of encrypting a huge “data + sender-privkey-encrypted-data”, we can encrypt only the “data + sender-privkey-encrypted-hash”.
- This concludes public key cryptography ## Hashing
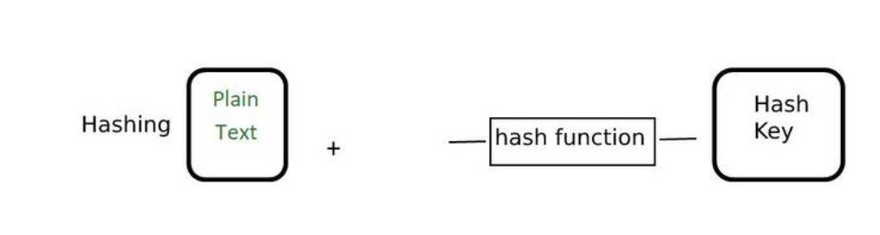
Hashing is the process of converting the information into a key using a hash function. The original information cannot be retrieved from the hash key by any means. Generally, the hash keys are stored in the database and they are compared to check whether the original information matches or not. They are generally used to store the passwords for login. Some of the examples of a hashing algorithm are MD5, SHA256.
Hashing
- Hashing is basically the act of using a hash function in order to produce a hash output. Examples of popular hash functions are SHA256, MD5, Bcyrpt, RIPEMD
- A hash function takes an input of any size (eg : your email password, the full text of the Illiad, or a blu-ray video of Inception)
- The output of a hash function is of fixed size ( say, a 64-character text). The output is also called a digest.
- Real example: sha256sum(“Meet me at 180 10th Ave. New York, NY 10011”) = 8D4364AFA2A79D46DDDA74361F9DF1EE939D84DC81E31FC53FAB221CA54E5E31
- In hashing, given an input, it is easy to compute the output. But it is practically impossible to reverse engineer a hash output and derive the input. Hence a hash function is also called a one-way function.
- Corollary : you cannot use hashing for encryption and decryption (as decryption is impossible due to the one-way nature). Technically, encryption/decryption functions are map functions(N to N). A hash function is a reduce function (N to 1). So fundamentally, cryptography and hashing are different beasts, though they may be combined for certain applications(such as public key cryptography).
- A hash output is useful to represent an input. This representation is called a fingerprint. This is useful if you want to make sure your data is not tampered or corrupted when it travels in a network. The hash of “sent data” should always equal the hash of “received data”. Basically, comparison of data is the most common use of hashing.
- In theory, it is possible that 2 different inputs can produce the same hash output. This is called collision. But in practice, a good hash function makes it real hard (time consuming) to find collisions.
Difference between Hashing and Encryption
:



Top comments (0)