There are several possibilities for how executables like bash18, sh18, and init18 might be set in the user daemon's crontab on a Linux server. Here are some common scenarios:
Manually Added by User: The executables could have been manually added to the crontab by the user, either through the command-line interface or by editing the crontab file directly.
Example:
* * * * * /path/to/bash18
This entry in the crontab will execute the bash18 executable every minute.
Script Execution: Instead of directly adding the executables, a script containing commands to run these executables could be scheduled in the crontab.
Example:
* * * * * /path/to/script.sh
If script.sh contains commands to execute bash18, sh18, or init18, then they will be invoked as part of the script's execution.
Installation Scripts: Some software packages or system administrators may create installation scripts that set up scheduled tasks, including crontab entries for periodic execution of certain tasks or utilities.
Example:
@reboot /path/to/init18
This entry in the crontab will execute init18 every time the system reboots.
Malicious Activity: In some cases, the presence of unfamiliar executables in the crontab could be a sign of malicious activity, where attackers gain unauthorized access to the system and schedule tasks to execute their own malicious code.
Example:
* * * * * /path/to/malicious_script.sh
Here, malicious_script.sh could contain commands to perform unauthorized activities or exploit vulnerabilities on the server.
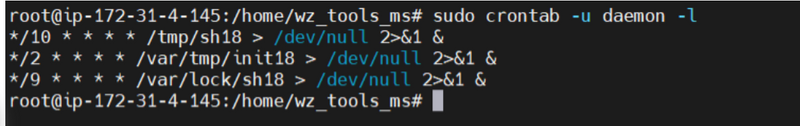
To investigate how these executables were added to the crontab, you can examine the modification timestamps of the crontab file (/var/spool/cron/crontabs/daemon) and cross-reference them with system logs or access logs to determine if the modifications were made by a legitimate user or if they are indicative of unauthorized access or malicious activity. Additionally, analyzing the content of the executables and associated scripts can provide insights into their purpose and origin.
# Example crontab entries for user daemon
*/5 * * * * /path/to/bash18_script.sh
0 3 * * * /path/to/sh18_script.sh
@reboot /path/to/init18_script.sh
output
Suppose we have a crontab entry in the daemon user's crontab file that uses bash18:
Contents of /var/spool/cron/crontabs/daemon:
*/5 * * * * /path/to/bash18_script.sh
Now, if we execute the command:
sudo grep -R 'bash18' /var/spool/cron/crontabs/*
The output could be:
/var/spool/cron/crontabs/daemon:*/5 * * * * /path/to/bash18_script.sh
This output indicates that in the daemon user's crontab file (/var/spool/cron/crontabs/daemon), there's a cron job scheduled to run a script (bash18_script.sh) using bash18 every 5 minutes. Similarly, you can run the command for other executables (sh18, init18, etc.) to find their occurrences in the crontab files.

Top comments (0)