Various approach and investigations of potential hacking activity
Explain the w command role to find suspicious activity
you can use various commands to check who is currently logged in and at what time. Here are some commonly used commands:
who: The who command displays a list of all users currently logged into the system, along with information about their login sessions.
Example:
$ who
$ who
user1 tty1 2024-03-25 08:30
user2 pts/0 2024-03-25 09:15 (:0)
w: The w command provides more detailed information about users currently logged in, including what they are doing and how long they have been idle.
Example:
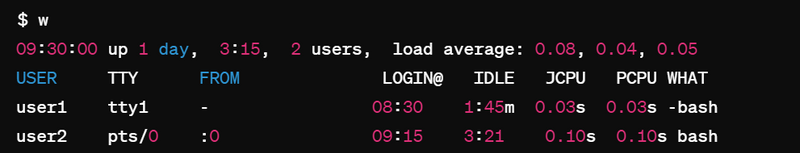
$ w
$ w
09:30:00 up 1 day, 3:15, 2 users, load average: 0.08, 0.04, 0.05
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
user1 tty1 - 08:30 1:45m 0.03s 0.03s -bash
user2 pts/0 :0 09:15 3:21 0.10s 0.10s bash
last: The last command displays a list of previous login sessions, showing when each user logged in and out.
Example:
$ last
$ last
user1 tty1 Thu Mar 25 08:30 still logged in
user2 pts/0 Thu Mar 25 09:15 still logged in
lastlog: The lastlog command displays a list of when each user last logged into the system.
Example:
$ lastlog
$ lastlog
Username Port From Latest
user1 tty1 Thu Mar 25 08:30:00 +0300 2024
user2 pts/0 :0 Thu Mar 25 09:15:00 +0300 2024
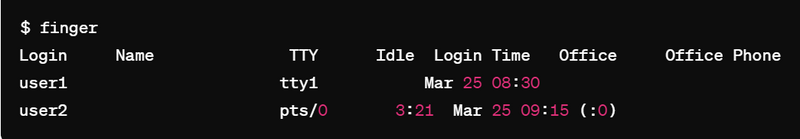
finger: The finger command can be used to gather information about users currently logged in, including their login name, real name, terminal, and login time.
Example:
$ finger
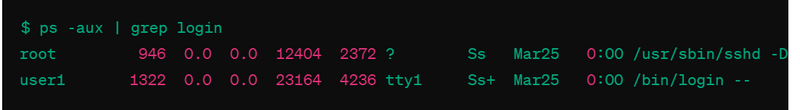
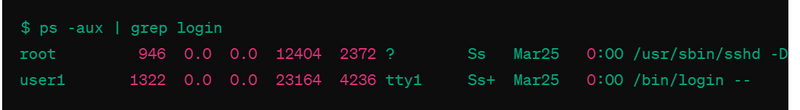
ps: The ps command can be used to check active processes on the system, which can include login processes.
Example:
$ ps -aux | grep login
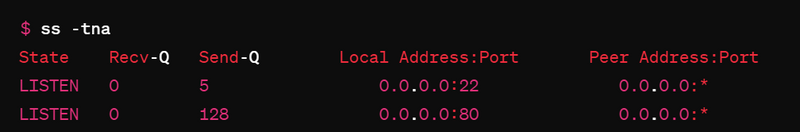
ss: The ss command can be used to display socket statistics, which may include active network connections, including login sessions.
Example:
$ ss -tna
These commands can provide insight into who is currently logged into the system and when they logged in, helping to monitor for unauthorized access or suspicious activity during a hacking incident. Always ensure you have appropriate permissions to run these commands, especially in a security-sensitive environment.
Various approach and investigations of potential hacking activity
If you suspect hacking activity and want to investigate further based on the output of the who command, you can follow these steps:
Identify Suspicious Activity: Look for anomalies or suspicious entries in the output of the who command. In this case, the presence of unexpected or unauthorized users could indicate potential hacking activity.
Investigate User Sessions: Focus on the user sessions listed by the who command. In your example, users "user1" and "user2" are logged in. Determine if these users are authorized to be logged in at the given time.
Check User Activities: Use other commands like w, last, ps, or ss to gather more information about the activities of the suspicious users. Look for any unusual processes or network connections associated with their sessions.
Review System Logs: Check system logs such as /var/log/auth.log or /var/log/secure for any suspicious login attempts, failed login attempts, or other relevant activity around the time of the suspected hacking.
Take Action: If you find evidence of unauthorized access or malicious activity, take appropriate action to mitigate the threat. This may include terminating suspicious sessions, blocking malicious IP addresses, changing passwords, and notifying system administrators or security personnel.
Remember, it's important to approach investigations of potential hacking activity with caution and thoroughness. False positives can occur, so ensure that you gather sufficient evidence before taking any remedial actions.
Explain the w command role to find suspicious activity
$ w
In the output of the w command, you can gather additional clues about potential hacking activity by examining the columns indicating user activity:
USER: This column lists the username associated with each logged-in session.
TTY: Indicates the terminal or pseudo-terminal where the user is logged in.
FROM: Represents the remote host or display from which the user logged in. In the case of local logins, it might display a dash (-).
LOGIN@: Shows the time when the user logged in.
IDLE: Indicates the idle time since the last user activity.
JCPU: Stands for "total CPU time used by the job's processes" in minutes and seconds.
PCPU: Stands for "CPU time used by the process" in minutes and seconds.
WHAT: Represents the command or activity the user is currently engaged in.
Given the suspicious entry "hacking activity" under the "WHAT" column for user2, this is indicative of potential malicious activity. You should investigate this further by:
Analyzing Processes: Use the ps command to inspect the processes associated with the suspicious user's session. Look for any unusual or unauthorized processes running.
Checking System Logs: Review system logs to see if there are any suspicious activities or attempted breaches associated with this user's session.
Monitoring Network Connections: Use tools like netstat or ss to monitor network connections associated with the suspicious user. Look for any connections to unfamiliar or suspicious destinations.
Terminate Suspicious Activity: If you determine that the activity is indeed malicious, take immediate action to terminate the user's session, block further access, and mitigate any potential damage.

Top comments (0)