To filter specific entries from the log file
Failed login attempts
SSH connection issues
Suspicious activity
view the authentication log file
filter all the entries related to successful logins
last 10 entries in the authentication log file
identify if a specific user has been attempting to log in to the system with the wrong password
display the last 10 entries in the authentication log file related to SSH connections
display all the entries in the authentication log file related to SSH connections from a specific IP address
Authentication logs in Linux are typically stored in the /var/log/auth.log file. These logs record authentication-related activities such as login attempts, failed authentication attempts, and other security events. The logs are typically written in a text format, making it easy to examine them using various Linux commands.
To examine the authentication log files using Linux pipe command, you can use the following steps:
1.Open your terminal and log in as a superuser or use sudo to elevate your privileges.
2.Type the following command to view the authentication log file:
cat /var/log/auth.log
This command will display the contents of the authentication log file in your terminal.
3.To filter specific entries from the log file, you can use the grep command along with a specific keyword or pattern. For example, to filter all the entries related to successful logins, you can use the following command:
cat /var/log/auth.log | grep "session opened for user"
This command will display all the entries that contain the "session opened for user" string.
4.Another useful command to examine authentication logs is tail. This command allows you to display the last few entries from the log file. For example, to display the last 10 entries in the authentication log file, you can use the following command:
tail /var/log/auth.log -n 10
This command will display the last 10 entries in the authentication log file.
By using Linux pipe commands such as grep and tail, you can easily examine authentication log files and extract valuable information related to security events on your system.
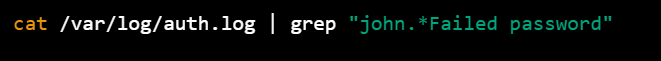
5.Failed login attempts: Authentication log files record all failed login attempts, including the username and IP address of the source. By examining the authentication log file using the grep command, you can easily identify if a specific user has been attempting to log in to the system with the wrong password. For example, the following command will display all the failed login attempts made by the user "john" in the authentication log file:
cat /var/log/auth.log | grep "john.*Failed password"
2.SSH connection issues: SSH connection issues can be caused by a variety of reasons, such as incorrect credentials, network issues, or firewall rules. By examining the authentication log file using the tail command, you can identify if there are any issues related to SSH connections. For example, the following command will display the last 10 entries in the authentication log file related to SSH connections:
tail /var/log/auth.log -n 10 | grep "sshd"
3.Suspicious activity: Authentication log files can also help you identify any suspicious activity on your system, such as unauthorized access or brute-force attacks. By examining the authentication log file using the grep command, you can easily identify any unusual or suspicious patterns in the log file. For example, the following command will display all the entries in the authentication log file related to SSH connections from a specific IP address:
cat /var/log/auth.log | grep "sshd.*from 192.168.0.100"
In conclusion, authentication log files can be very helpful in troubleshooting various security and authentication issues on your Linux system. By using Linux pipe commands such as grep and tail, you can easily examine the log files and extract valuable information to troubleshoot the issues

Top comments (0)