Steps to identify unexpected or unusual file accesses or network connections
How to identify High Number of Connections malware attempting in linux server
How to identify unexpected outbound connections may indicate malicious activity in linux server
Steps to identify unexpected or unusual file accesses or network connections
To identify unexpected or unusual file accesses or network connections from the output of lsof -p 1379, you would typically look for patterns that deviate from normal system behavior. Here are some steps you can take:
Examine Network Connections: Look for network connections (if any) that the process has opened. Suspicious network connections might include connections to unknown or suspicious IP addresses, especially if they're on uncommon ports.
Check File Accesses: Review the files and directories that the process has opened. Look for accesses to sensitive system files, configuration files, or directories that are not typically accessed by the process. Pay attention to any unexpected or unusual file accesses.
Analyze Access Patterns: Look for any patterns in file accesses or network connections that seem unusual or out of place. For example, if the process is accessing a large number of files in a short period, or if it's repeatedly connecting to different hosts, it could indicate suspicious behavior.
Compare with Known Behavior: Compare the observed file accesses and network connections with the expected behavior of the process or similar processes on the system. This can help you identify deviations from normal activity.
Investigate Further: If you identify any suspicious file accesses or network connections, investigate further to determine the nature of the activity. This may involve analyzing the content of accessed files, monitoring network traffic, or conducting forensic analysis.
In the example output provided:
Network Connections: Look for entries where the TYPE column is IPv4 or IPv6, indicating network connections. Check the associated IP addresses and ports to see if they match known or expected connections.
File Accesses: Review the entries with TYPE other than IPv4 or IPv6. Check the NAME column to see which files or directories are being accessed. Pay attention to accesses to system files or directories outside the expected scope of the process.
By carefully analyzing the output and looking for deviations from normal behavior, you can identify unexpected or unusual file accesses or network connections that may indicate suspicious activity
How to identify High Number of Connections malware attempting in linux server
To identify a high number of connections, which could be indicative of malware or a potential hacking attempt on a Linux server, you can use the netstat command in combination with sort and uniq to count the number of connections per IP address and then sort them to find the IPs with the highest number of connections. Here's a command to achieve this:
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nr
By running this command, you'll get a list of IP addresses along with the number of connections each IP has established with your server. This will help you identify any IPs with a high number of connections, which may indicate suspicious activity. Further investigation may be required to determine the nature of these connections and whether they pose a security threat.
How to identify unexpected outbound connections may indicate malicious activity in linux server
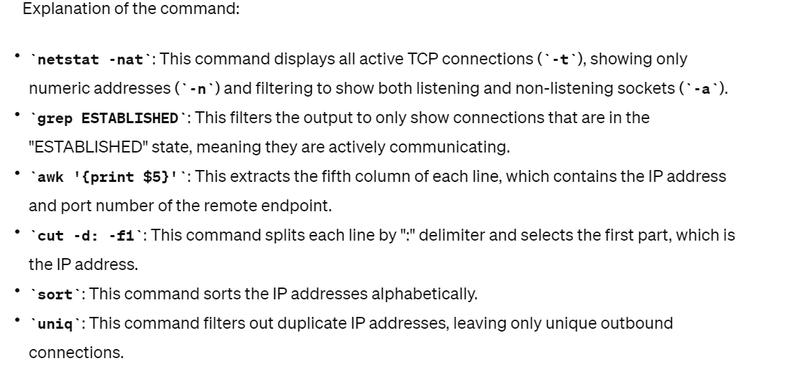
To identify unexpected outbound connections on a Linux server, which may indicate malicious activity, you can use the netstat command along with some filtering options. Specifically, you'll want to focus on outbound connections, as these could indicate unauthorized communication initiated by a potential attacker. Here's a command to achieve this:
netstat -nat | grep ESTABLISHED | awk '{print $5}' | cut -d: -f1 | sort | uniq
By running this command, you'll get a list of unique IP addresses to which outbound connections are established from your server. Reviewing these connections can help identify any unexpected outbound connections, which may be indicative of malicious activity. Further investigation into the purpose and legitimacy of these connections may be necessary to mitigate any potential security risks.


Top comments (0)