Listout the checklist of Best practices for Dockerfile instructions
Checklist of best practices for using Docker
listout the checklist of best practice for docker security-best-practices
Listout the checklist of Best practices for Dockerfile instructions
Use Official Base Images:
Best Practice: Start with an official base image from a trusted source.
FROM ubuntu:20.04
2. Use a Minimal Base Image:
Best Practice: Choose a minimal base image to reduce the attack surface and image size.
Example:
FROM alpine:3.14
3. Group Related Commands:
Best Practice: Group related commands to reduce the number of layers and improve build performance.
Example:
RUN apt-get update && \
apt-get install -y \
package1 \
package2 && \
apt-get clean && \
rm -rf /var/lib/apt/lists/*
4. Use COPY Instead of ADD:
Best Practice: Prefer COPY over ADD for copying files and directories.
Example:
COPY . /app
5. Specify Version for System Libraries:
Best Practice: Specify the version for system libraries to ensure reproducibility.
Example:
RUN apt-get update && \
apt-get install -y \
package=1.2.3-4 && \
apt-get clean && \
rm -rf /var/lib/apt/lists/*
6. Use ENV for Environment Variables:
Best Practice: Use ENV to set environment variables.
Example:
ENV NODE_ENV=production
7. Clean Up Unnecessary Files:
Best Practice: Remove unnecessary files and cleanup to reduce the image size.
Example:
RUN apt-get purge -y --auto-remove \
package && \
rm -rf /var/lib/apt/lists/*
8. Use a Non-Root User:
Best Practice: Avoid running applications as the root user for security reasons.
Example:
USER appuser
9. Expose Only Necessary Ports:
Best Practice: Use EXPOSE to document the ports that the container listens on.
Example:
EXPOSE 80
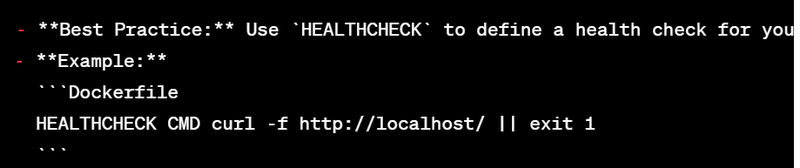
10. Use HEALTHCHECK for Health Checks:
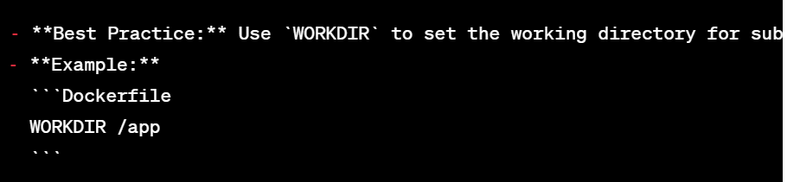
11. Specify Work Directory:
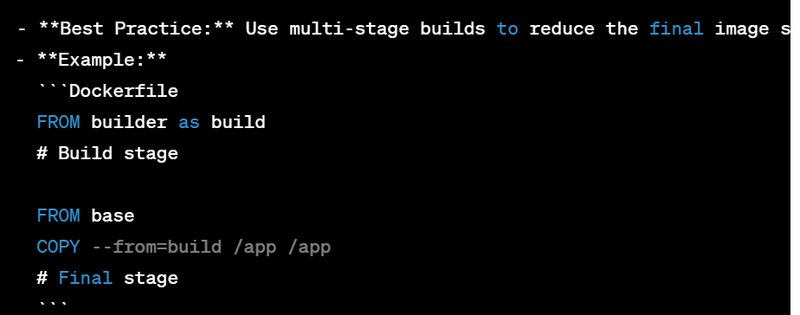
12. Use Multi-Stage Builds:
13. Avoid Using sudo:
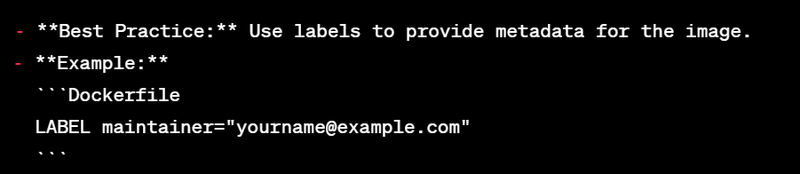
14. Label the Image:
15. Document Your Image:
These best practices contribute to building efficient, secure, and maintainable Docker images. Adapt these practices based on the specific requirements of your application and use case.
Checklist of best practices for using Docker
1. Use Official Images:
Best Practice: Start with official images from trusted repositories.
Example:
docker pull nginx:latest
2. Update Docker Regularly:
Best Practice: Keep Docker up-to-date to benefit from security updates and new features.
Example:
sudo apt-get update && sudo apt-get install docker-ce docker-ce-cli containerd.io
3. Run Containers with Limited Privileges:
Best Practice: Use the principle of least privilege for container processes.
Example:
docker run --rm --name mynginx -d -p 80:80 --security-opt=no-new-privileges nginx:latest
4. Use Docker Compose for Multi-Container Applications:
Best Practice: Utilize Docker Compose for managing multi-container applications.
Example: Create a docker-compose.yml file.
version: '3'
services:
web:
image: nginx:latest
ports:
- "80:80"
Run with:
docker-compose up -d
5. Remove Stopped Containers:
Best Practice: Regularly clean up stopped containers to save disk space.
Example:
docker container prune
6. Tag Images with Versions:
Best Practice: Tag Docker images with version information.
Example:
docker tag myapp:latest myapp:1.0
7. Use .dockerignore File:
Best Practice: Create a .dockerignore file to exclude unnecessary files from the build context.
Example:
.git
node_modules
8. Limit Image Layers:
Best Practice: Reduce the number of layers in your image for better performance and smaller size.
Example:
FROM alpine:3.14
RUN apk --no-cache add \
package1 \
package2 \
&& rm -rf /var/cache/apk/*
9. Use Docker Secrets for Sensitive Data:
Best Practice: Store sensitive data like passwords or API keys using Docker secrets.
Example: Create a secret and use it in a service.
echo "mysecret" | docker secret create my_secret_data -
In a docker-compose.yml:
version: '3.1'
services:
app:
image: myapp:latest
secrets:
- my_secret_data
secrets:
my_secret_data:
external: true
10. Monitor and Manage Resources:
- Best Practice: Monitor and limit container resources (CPU, memory) as needed.
- Example:
docker run --rm --name myapp -d -p 8080:80 --cpu-shares 512 --memory 512m nginx:latest
11. Use COPY Instead of ADD in Dockerfiles:
-
Best Practice: Prefer
COPYoverADDfor copying files in Dockerfiles. - Example:
COPY . /app
- Best Practice: Order your Dockerfile instructions to optimize build cache utilization.
- Example:
FROM node:14
WORKDIR /app
COPY package*.json ./
RUN npm install
COPY . .
13. Clean Up Build Artifacts:
- Best Practice: Remove unnecessary build artifacts to reduce the final image size.
- Example:
FROM node:14 as builder
WORKDIR /app
COPY . .
RUN npm install
RUN npm run build
FROM nginx:latest
WORKDIR /usr/share/nginx/html
COPY --from=builder /app/dist .
14. Use .dockerconfigjson for Registry Authentication:
-
Best Practice: Use
.docker/config.jsonfor storing registry authentication credentials. - Example: Manually authenticate and store credentials.
echo '{"auths":{"registry.example.com":{"auth":"<base64-encoded-auth>"}}}' > ~/.docker/config.json
15. Secure Docker Daemon:
These best practices help ensure that Docker images and containers are secure, efficient, and follow recommended patterns for development and deployment. Adapt these practices based on your specific use case and requirements.
listout the checklist of best practice for docker security-best-practices
1. Keep Docker Up-to-Date:
Best Practice: Regularly update Docker to benefit from security patches.
Example: Update Docker on a Linux system.
sudo apt-get update
sudo apt-get install docker-ce docker-ce-cli containerd.io
2. Enable Content Trust:
Best Practice: Enable Docker Content Trust to verify image integrity.
Example: Enable content trust globally.
export DOCKER_CONTENT_TRUST=1
3. Use Official Images:
Best Practice: Start with official images from trusted repositories.
Example: Pull an official NGINX image.
docker pull nginx:latest
4. Minimize Image Size:
Best Practice: Reduce the size of your Docker images to minimize attack surface.
Example: Use a minimal base image.
FROM alpine:3.14
5. Limit Privileges:
Best Practice: Run containers with the least necessary privileges.
Example: Start a container with a non-root user.
docker run --user 1000:1000 myimage
6. Avoid Running as Root:
Best Practice: Minimize running processes as the root user within containers.
Example: Use a non-root user in a Dockerfile.
USER appuser
7. Use Docker Bench Security:
Best Practice: Run Docker Bench Security to check for common security misconfigurations.
Example: Run Docker Bench Security.
docker run -it --net host --pid host --userns host --cap-add audit_control \
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
-v /etc:/etc:ro \
-v /usr/bin/docker-containerd:/usr/bin/docker-containerd:ro \
-v /usr/bin/docker-runc:/usr/bin/docker-runc:ro \
-v /usr/lib/systemd:/usr/lib/systemd:ro \
-v /var/lib:/var/lib:ro \
-v /var/run/docker.sock:/var/run/docker.sock:ro \
--label docker_bench_security \
docker/docker-bench-security
8. Use Image Scanning Tools:
Best Practice: Utilize image scanning tools to identify vulnerabilities.
Example: Use Docker Security Scanning.
docker scan myimage
9. Network Segmentation:
Best Practice: Use network segmentation to control container communication.
Example: Create a custom bridge network.
docker network create --driver bridge mynetwork
10. Secure Docker Daemon:
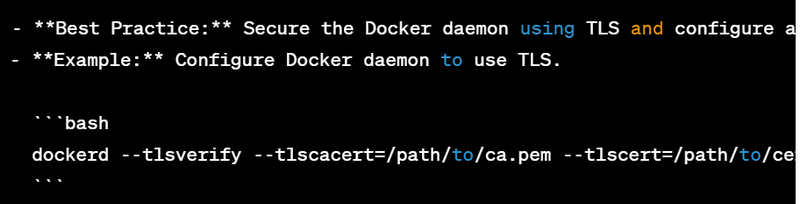
- Best Practice: Secure the Docker daemon with TLS and restrict access.
- Example: Start Docker daemon with TLS.
dockerd --tlsverify --tlscacert=/path/to/ca.pem --tlscert=/path/to/cert.pem --tlskey=/path/to/key.pem -H=0.0.0.0:2376
11. Use Docker Secrets for Sensitive Data:
- Best Practice: Store sensitive data using Docker secrets.
- Example: Create a secret and use it in a service.
echo "mysecret" | docker secret create my_secret_data -
12. Container Resource Constraints:
- Best Practice: Enforce resource constraints on containers.
- Example: Limit container memory and CPU.
docker run --rm -it --memory 512m --cpus 0.5 myimage
13. Use Security Profiles:
- Best Practice: Leverage security profiles (AppArmor, SELinux) to restrict container actions.
- Example: Run a container with AppArmor.
docker run --security-opt apparmor=myapp_profile myimage
14. Regularly Audit and Monitor Containers:
- Best Practice: Implement regular auditing and monitoring of container activities.
Example: Use tools like Docker Stats or Prometheus for monitoring.
15. Disable Inter-container Communication:Best Practice: Disable inter-container communication when not needed.
Example: Use network modes to control container communication.
docker run --network=none myimage
These practices help improve the security posture of Docker containers. Always adapt security measures based on your specific use case and requirements.



Top comments (0)