List out the checklist of different way to Set the Working Directory in dockerfile
list out the checklist of different way to Copy Application Code in dockerfile
list out the checklist of different way to implement Install Dependencies: in dockerfile
list out the checklist of different way to implement Expose Ports in dockerfile
list out the checklist of different way to implement Expose Ports in dockerfile
list out the checklist of different way to implement Environment Variables: in dockerfile
list out the checklist of different way to implement Run Commands: in dockerfile
list out the checklist of different way to implement User Permissions in dockerfile
list out the checklist of different way to implement Clean up in dockerfile
list out the checklist of different way to implement Health Checks in dockerfile
list out the checklist of different way to implement Logging Configuration: in dockerfile
list out the checklist of different way to implement Security Considerations
list out the checklist of different way to implement Version Control and Tagging in dockerfile
Listout the checklist what Security Considerations: an apply in docker file
When creating a Dockerfile for real-time applications, there are several key considerations to ensure a smooth and efficient deployment. Here's a checklist for creating a
Dockerfile for real-time applications:
Select a Base Image:
Choose a base image that is suitable for your application. Consider using lightweight images like Alpine Linux for reduced image size.
Set the Working Directory:
Use the WORKDIR instruction to set the working directory within the container.
Copy Application Code:
Copy the application code and any necessary files into the container using the COPY instruction.
Install Dependencies:
Install any dependencies required by your application using package managers (apt-get, yum, etc.) or other methods.
Expose Ports:
Use the EXPOSE instruction to specify which ports the application will use. This helps in mapping the ports when running the container.
Environment Variables:
Set any environment variables needed for the application to run using the ENV instruction.
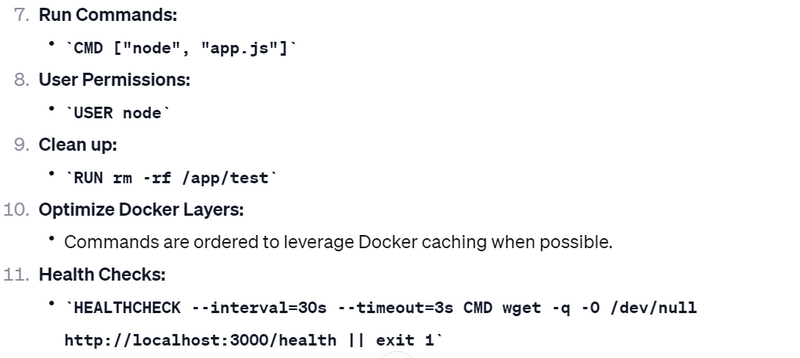
Run Commands:
Specify the command to run your application using the CMD or ENTRYPOINT instruction. This is the command that will be executed when the container starts.
User Permissions:
Consider using the USER instruction to run the application with a non-root user for security reasons.
Clean up:
Remove unnecessary files or packages after installation to reduce the size of the final image.
Optimize Docker Layers:
Group related commands together to make better use of Docker's layer caching mechanism. This helps to speed up the build process.
Health Checks:
Implement health checks to ensure that the container is running as expected. This is especially important for real-time applications that need to be highly available.
Logging Configuration:
Configure logging settings within the Dockerfile or provide a mechanism to customize logging configurations.
Security Considerations:
Ensure that your Dockerfile follows security best practices. This includes minimizing the attack surface, updating packages, and avoiding unnecessary privileges.
Version Control and Tagging:
Consider versioning your Docker image using tags. This helps in tracking changes and rolling back to a specific version if needed.
Documentation:
Include comments within the Dockerfile to explain complex steps or configurations. Additionally, consider providing a README file with information on how to use the Docker image.
Remember to continually test your Dockerfile and update it as needed to accommodate changes in your application or its dependencies. Regularly updating base images and adhering to best practices will contribute to a more reliable and secure Dockerized application.
# Use a lightweight base image
FROM alpine:3.14
# Set the working directory
WORKDIR /app
# Copy the application code into the container
COPY . .
# Install dependencies (for example, using npm for a Node.js application)
RUN apk --no-cache add nodejs npm \
&& npm install
# Expose the necessary port
EXPOSE 3000
# Set environment variables
ENV NODE_ENV=production
# Specify the command to run the application
CMD ["node", "app.js"]
# Use a non-root user for running the application
USER node
# Clean up unnecessary files
RUN rm -rf /app/test
# Implement a health check
HEALTHCHECK --interval=30s --timeout=3s \
CMD wget -q -O /dev/null http://localhost:3000/health || exit 1
==========================================
listout the checklist what Security Considerations: an apply in docker file
Ensuring the security of Docker containers is crucial for preventing potential vulnerabilities. Here's a checklist of security considerations for Dockerfiles:
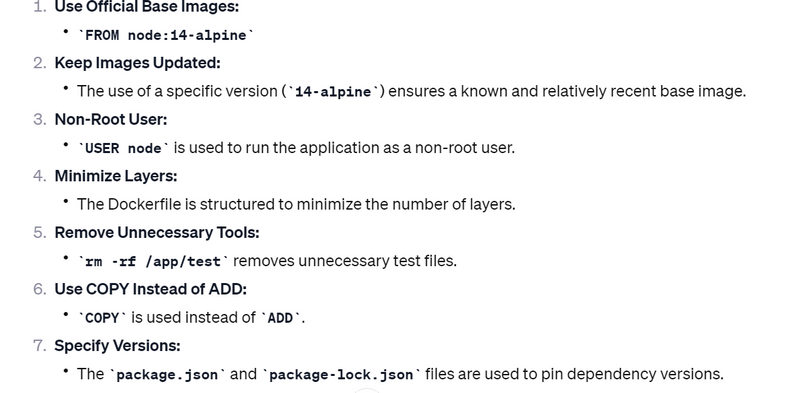
Use Official Base Images:
Start with official and minimal base images from trusted sources like Docker Hub.
Keep Images Updated:
Regularly update base images and dependencies to patch known vulnerabilities.
Non-Root User:
Use a non-root user to run the application within the container to minimize potential damage from security breaches.
Minimize Layers:
Reduce the number of layers in your Docker image to minimize the attack surface.
Remove Unnecessary Tools:
Remove any unnecessary tools or packages after the installation to reduce the attack surface.
Use COPY Instead of ADD:
Prefer the COPY instruction over ADD to avoid unintentional file retrievals from remote URLs.
Specify Versions:
Pin versions of packages to ensure predictable behavior and avoid unexpected updates.
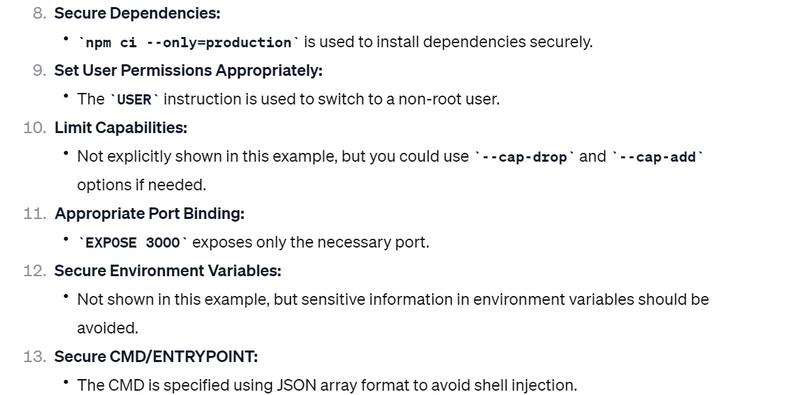
Secure Dependencies:
Verify the integrity of downloaded packages and dependencies, and use checksums when available.
Set User Permissions Appropriately:
Restrict file and directory permissions to only what is necessary for the application to function.
Limit Capabilities:
Use the --cap-drop and --cap-add options to limit or add Linux capabilities as needed by the application.
Appropriate Port Binding:
Only expose the necessary ports and avoid using the EXPOSE instruction if not needed.
Secure Environment Variables:
Avoid sensitive information in environment variables. If needed, use Docker secrets or other secure methods.
Secure CMD/ENTRYPOINT:
Be cautious with CMD and ENTRYPOINT to avoid shell injection attacks. Use JSON array format for CMD and ENTRYPOINT.
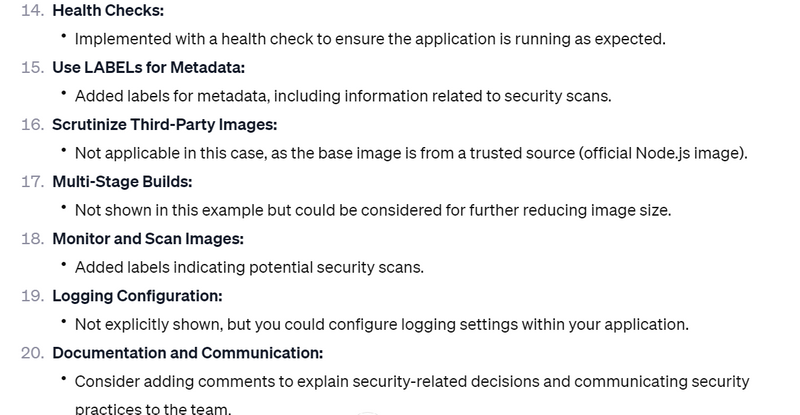
Health Checks:
Implement health checks to ensure that the application is running as expected.
Use LABELs for Metadata:
Add labels to provide metadata about your image, including security-related information.
Scrutinize Third-Party Images:
If using third-party images, review their Dockerfiles and ensure they meet security best practices.
Multi-Stage Builds:
Use multi-stage builds to minimize the size of the final image and exclude unnecessary build tools from the production image.
Monitor and Scan Images:
Use container security tools to scan images for vulnerabilities regularly.
Logging Configuration:
Configure logging to capture relevant security events and monitor container behavior.
Documentation and Communication:
Clearly document security practices in the Dockerfile and communicate security considerations to the development and operations teams.
Adhering to these security considerations will help enhance the security posture of your Dockerized applications. Keep in mind that security is an ongoing process, and regular reviews and updates are essential.
# Use a lightweight, official Node.js base image
FROM node:14-alpine
# Set the working directory
WORKDIR /app
# Copy only necessary files for dependency installation
COPY package.json package-lock.json ./
# Install dependencies with npm
RUN npm ci --only=production
# Copy the rest of the application code
COPY . .
# Use a non-root user to run the application
USER node
# Expose the necessary port
EXPOSE 3000
# Set environment variable for production
ENV NODE_ENV=production
# Specify the command to run the application with JSON array format
CMD ["node", "app.js"]
# Remove unnecessary files and packages
RUN rm -rf /app/test && \
npm prune --production
# Implement a health check
HEALTHCHECK --interval=30s --timeout=3s \
CMD wget -q -O /dev/null http://localhost:3000/health || exit 1
# Add security-related labels
LABEL maintainer="yourname@example.com" \
description="Node.js chat application" \
version="1.0" \
security.scans.daily="Clair" \
security.scans.weekly="Anchore"
# Set a non-root user for security
USER node
List out the checklist of different way to Set the Working Directory in dockerfile
Setting the working directory in a Dockerfile is essential for defining the directory where commands, such as RUN, CMD, and COPY, will be executed or applied. Here's a checklist of different ways to set the working directory in a Dockerfile along with examples:
Use the WORKDIR Instruction:
Use the WORKDIR instruction to set the working directory in your
FROM base_image
# Set the working directory
WORKDIR /path/to/your/directory
Combine WORKDIR with Other Instructions:
You can use multiple WORKDIR instructions in a Dockerfile, and subsequent instructions are relative to the last WORKDIR set.
FROM base_image
WORKDIR /app
# Subsequent commands will be executed in /app directory
RUN mkdir subdir
WORKDIR subdir
Use ARG to Set a Dynamic Working Directory:
You can use the ARG instruction to set a dynamic value for the working directory.
FROM base_image
ARG workdir=/path/to/your/directory
WORKDIR $workdir
Set Working Directory During Build:
You can set the working directory as part of the docker build command.
docker build --build-arg workdir=/path/to/your/directory -t your_image .
Use Environment Variable for Working Directory:
Set an environment variable for the working directory.
FROM base_image
ENV WORK_DIR /path/to/your/directory
WORKDIR $WORK_DIR
Combine WORKDIR with COPY:
Use WORKDIR in conjunction with COPY to set the working directory and copy files at the same time.
FROM base_image
WORKDIR /app
COPY . .
Set Working Directory in Docker Compose:
If you are using Docker Compose, you can set the working directory in the service definition.
version: '3'
services:
your_service:
build:
context: .
dockerfile: Dockerfile
args:
- workdir=/path/to/your/directory
Default WORKDIR in Base Images:
Some base images may already have a default WORKDIR. Check the documentation for the base image you are using.
FROM node:14
WORKDIR is already set to /usr/src/app in the node:14 image
Verify Working Directory in Container:
After building and running your container, verify that the working directory is set correctly.
docker run -it your_image pwd
Use Relative Paths:
When setting the working directory, consider using relative paths for better portability.
FROM base_image
WORKDIR ./app
By following these guidelines, you can effectively set and manage the working directory in your Dockerfile based on your specific needs and use cases. Adjust the examples to match the directory structure and requirements of your application.
list out the checklist of different way to Copy Application Code in dockerfile
Copying application code into a Docker image is a crucial step in the Dockerfile to ensure that the image contains the necessary files for the application to run. Here's a checklist of different ways to copy application code with examples:
Use the COPY Instruction:
Use the COPY instruction to copy files or directories from the build context into the image.
FROM base_image
# Copy the entire application directory into the image
COPY . /app
Use a Specific Directory in the Build Context:
Specify a specific directory from the build context to copy into the image.
FROM base_image
# Copy only the contents of the "src" directory into the image
COPY src/ /app/src
Use Wildcards in COPY:
Use wildcards to copy multiple files or directories matching a pattern.
FROM base_image
# Copy all .js files from the build context into the image
COPY *.js /app/
Use Multiple COPY Instructions:
Use multiple COPY instructions to copy files or directories from different locations.
FROM base_image
COPY src/ /app/src
COPY config/ /app/config
Use WORKDIR with COPY:
Combine WORKDIR and COPY to set the working directory and copy files in a single step.
FROM base_image
WORKDIR /app
COPY . .
Use .dockerignore to Exclude Unnecessary Files:
Create a .dockerignore file to exclude files or directories from being copied into the image.
node_modules
.git
Use ADD for URL and Remote Sources:
The ADD instruction can be used to copy files from a URL or remote source.
FROM base_image
ADD https://example.com/myfile.txt /app/
Copy Files from a Builder Stage:
If you're using multi-stage builds, copy files from a previous build stage into the current stage.
FROM builder as build
# Build your application and create artifacts
FROM base_image
# Copy artifacts from the build stage into the final image
COPY --from=build /app/artifacts /app
Verify Copied Files:
After building the image, run a container and verify that the application code has been copied correctly.
docker run -it your_image ls /app
Consider Volume Mounts for Development:
During development, consider using volume mounts to avoid rebuilding the image every time the code changes.
docker run -v $(pwd):/app your_image
By following these guidelines, you can effectively copy your application code into a Docker image, ensuring that the image contains all the necessary files for your application to run. Adjust the examples to match your application's directory structure and requirements.
list out the checklist of different way to implement Install Dependencies: in dockerfile
Installing dependencies in a Dockerfile is a crucial step to ensure that your application has all the required libraries and packages. The following is a checklist of different ways to implement the installation of dependencies with examples:
Use Package Managers:
Leverage package managers like APT (for Debian-based images) or YUM (for Red Hat-based images) to install system-level dependencies.
FROM base_image
# Install dependencies using APT
RUN apt-get update && \
apt-get install -y \
package1 \
package2 \
&& rm -rf /var/lib/apt/lists/*
Use Package Managers for Multiple Steps:
Utilize package managers in multiple steps to minimize the number of layers created in the image.
FROM base_image as builder
# Install build dependencies
RUN apt-get update && \
apt-get install -y build-essential
FROM base_image
# Copy only the necessary files from the builder stage
COPY --from=builder /usr/bin/build-binary /usr/bin/
Use Package Managers for Specific Package Versions:
Specify the version of each package to ensure consistency and reproducibility.
FROM base_image
# Install specific versions of packages
RUN apt-get update && \
apt-get install -y \
package1=1.2.3 \
package2=4.5.6 \
&& rm -rf /var/lib/apt/lists/*
Use Pip for Python Dependencies:
Use pip to install Python dependencies.
FROM python:3.9
# Install Python dependencies
RUN pip install \
package1==1.2.3 \
package2==4.5.6
Use npm for Node.js Dependencies:
Use npm to install Node.js dependencies.
FROM node:14
# Install Node.js dependencies
RUN npm install \
package1@1.2.3 \
package2@4.5.6
Use Go Modules for Go Dependencies:
Utilize Go modules to manage and install Go dependencies.
FROM golang:1.16
WORKDIR /app
# Copy go.mod and go.sum files to download dependencies
COPY go.mod go.sum ./
# Download and install Go dependencies
RUN go mod download
Use Virtual Environments for Python:
Use virtual environments to isolate Python dependencies.
FROM python:3.9
WORKDIR /app
# Create and activate virtual environment
RUN python -m venv venv
ENV PATH="/app/venv/bin:$PATH"
# Install Python dependencies
RUN pip install \
package1==1.2.3 \
package2==4.5.6
Use Alpine Linux for Smaller Images:
If image size is a concern, consider using Alpine Linux and its package manager (apk) for smaller images.
FROM alpine:3.14
# Install dependencies using apk
RUN apk --no-cache add \
package1 \
package2
Combine Install Steps for Image Optimization:
Combine multiple RUN commands into a single layer to reduce image size.
FROM base_image
# Combine install steps
RUN apt-get update && \
apt-get install -y \
package1 \
package2 \
&& rm -rf /var/lib/apt/lists/*
Clean Up After Installation:
Remove unnecessary files and caches to reduce the image size.
FROM base_image
# Install dependencies
RUN apt-get update && \
apt-get install -y \
package1 \
package2 \
&& rm -rf /var/lib/apt/lists/*
# Clean up
RUN apt-get clean && \
rm -rf /var/lib/apt/lists/*
By following these guidelines, you can effectively install dependencies in your Dockerfile based on the programming language and package management system used in your application. Adjust the examples to match the specific requirements of your project.
list out the checklist of different way to implement Expose Ports in dockerfile
Exposing ports in a Dockerfile is essential for defining which network ports your container will listen on. Here's a checklist of different ways to implement exposing ports in a Dockerfile with examples:
Use the EXPOSE Instruction:
Use the EXPOSE instruction to inform Docker that the specified ports on the container are intended to be published and made accessible to the host machine or other containers.
FROM base_image
# Expose port 80 for incoming traffic
EXPOSE 80
Expose Multiple Ports:
You can expose multiple ports by listing them in the EXPOSE instruction.
FROM base_image
# Expose port 80 for HTTP and port 443 for HTTPS
EXPOSE 80 443
Use Environment Variables for Port Configuration:
Set environment variables for port numbers to allow flexibility and make it easy to change port configurations.
FROM base_image
ENV HTTP_PORT=80
ENV HTTPS_PORT=443
# Expose ports using environment variables
EXPOSE $HTTP_PORT $HTTPS_PORT
Use the -p Option with Docker Run:
When running a container, you can use the -p option to bind container ports to host ports.
docker run -p 8080:80 -p 8443:443 your_image
Bind Ports Dynamically:
Allow Docker to dynamically assign host ports by omitting the host port number when using the -p option.
docker run -p 80 your_image
Use Multiple -p Options:
You can use multiple -p options to bind multiple ports.
docker run -p 8080:80 -p 8443:443 your_image
Bind to All Network Interfaces:
Use 0.0.0.0 to bind the exposed ports to all network interfaces on the host.
FROM base_image
# Expose ports and bind to all network interfaces
EXPOSE 0.0.0.0:80 0.0.0.0:443
Use -P Option for Random Host Ports:
Use the -P option to bind all exposed ports to random host ports.
docker run -P your_image
Document Exposed Ports in Docker Compose:
In Docker Compose, document the exposed ports in the service definition.
version: '3'
services:
your_service:
build: .
ports:
- "8080:80"
- "8443:443"
Test Connectivity to Exposed Ports:
After running the container, test connectivity to the exposed ports to ensure that the container is reachable.
telnet localhost 8080
Use HEALTHCHECK Instruction:
If applicable, consider adding a HEALTHCHECK instruction to ensure that the exposed service is healthy.
FROM base_image
# Expose port 80 for HTTP
EXPOSE 80
# Healthcheck command
HEALTHCHECK CMD curl --fail http://localhost:80/ || exit 1
By following these guidelines, you can effectively expose and manage ports in your Dockerfile based on your application's requirements. Adjust the examples to match the specific port configuration needed for your project.
list out the checklist of different way to implement Environment Variables: in dockerfile
Setting environment variables in a Dockerfile is a common practice for configuring containerized applications. Here's a checklist of different ways to implement environment variables in a Dockerfile with examples:
Use the ENV Instruction:
Use the ENV instruction to set environment variables in your Dockerfile.
FROM base_image
# Set environment variables
ENV KEY=value
Set Multiple Environment Variables:
You can set multiple environment variables using a single ENV instruction.
FROM base_image
# Set multiple environment variables
ENV KEY1=value1 \
KEY2=value2
Use ARG Instruction for Dynamic Values:
Use the ARG instruction to set dynamic values for environment variables during the build.
FROM base_image
ARG APP_VERSION=1.0.0
# Set environment variable with dynamic value
ENV APP_VERSION=$APP_VERSION
Use ARG with --build-arg During Build:
Pass values to build-args using --build-arg during the build process.
docker build --build-arg APP_VERSION=2.0.0 -t your_image .
Set Environment Variables in Docker Compose:
If using Docker Compose, set environment variables in the docker-compose.yml file.
version: '3'
services:
your_service:
image: your_image
environment:
KEY1: value1
KEY2: value2
Use Environment Variables in CMD or ENTRYPOINT:
Reference environment variables in the CMD or ENTRYPOINT instructions.
FROM base_image
ENV PORT=8080
# Use environment variable in CMD
CMD ["node", "app.js", "--port", "$PORT"]
Use Default Values in CMD or ENTRYPOINT:
Provide default values for environment variables in the CMD or ENTRYPOINT instructions.
FROM base_image
ENV PORT=8080
# Use default value if not provided
CMD ["node", "app.js", "--port", "${PORT:-8080}"]
Set Environment Variables for User:
Set environment variables specific to a user with the ENV instruction.
FROM base_image
USER appuser
# Set environment variable for the user
ENV USER_HOME=/home/appuser
Use Variables in COPY and ADD Instructions:
Reference environment variables in COPY or ADD instructions.
FROM base_image
ENV APP_DIR=/app
# Copy files using environment variable
COPY . $APP_DIR
Clear Environment Variables in the Same Instruction:
Clear environment variables in the same instruction to minimize layers.
FROM base_image
# Clear environment variables in the same instruction
ENV KEY1=value1 \
KEY2=value2 \
&& echo "Do something with the variables"
Use Build-Time Variables:
Use build-time variables to pass values during the build process.
FROM base_image
ARG BUILD_ENV
ENV ENVIRONMENT=$BUILD_ENV
Use .env Files:
Use .env files to manage environment variables outside the Dockerfile or Docker Compose files.
FROM base_image
# Use environment variables from .env file
ENV $(cat .env | xargs)
By following these guidelines, you can effectively manage environment variables in your Dockerfile based on your application's requirements. Adjust the examples to match the specific configuration needed for your project.
list out the checklist of different way to implement Run Commands: in dockerfile
Running commands in a Dockerfile is a fundamental step in defining the behavior of your container. Here's a checklist of different ways to implement run commands in a Dockerfile with examples:
Use the RUN Instruction:
Use the RUN instruction to execute commands during the image build process.
FROM base_image
# Run a command during the build
RUN apt-get update && apt-get install -y package
Run Multiple Commands:
You can run multiple commands in a single RUN instruction.
FROM base_image
# Run multiple commands
RUN apt-get update && \
apt-get install -y \
package1 \
package2
Use Shell Form vs. Exec Form:
Choose between shell form and exec form when running commands.
Shell Form:
RUN echo "Hello, World!"
Exec Form:
RUN ["echo", "Hello, World!"]
Use && for Conditional Execution:
Use && to conditionally execute commands based on the success of the previous one.
FROM base_image
# Install dependencies only if the previous command succeeds
RUN apt-get update && \
apt-get install -y package
Use Backslashes for Line Continuation:
Use backslashes () to continue a command on the next line for better readability.
FROM base_image
# Continue command on the next line
RUN apt-get update \
&& apt-get install -y package
Use Variables in RUN Commands:
Use variables for dynamic values in RUN commands.
FROM base_image
ARG APP_VERSION=1.0.0
# Use variable in the RUN command
RUN echo "Running app version: $APP_VERSION"
Use Shell Features:
Utilize shell features like variable substitution, redirection, and pipes in RUN commands.
FROM base_image
# Use shell features
RUN echo "Hello, World!" > /app/output.txt
Use Shell for Complex Commands:
Use the shell for complex commands that involve variables and conditionals.
FROM base_image
ARG APP_ENV=production
# Use shell for complex commands
RUN if [ "$APP_ENV" = "production" ]; then \
echo "Running in production mode"; \
else \
echo "Running in development mode"; \
fi
Use ENTRYPOINT and CMD for Execution at Runtime:
For commands that need to run when the container starts, use ENTRYPOINT or CMD.
FROM base_image
# Set default command to run when the container starts
CMD ["echo", "Hello, World!"]
Use SHELL Instruction for Default Shell:
Use the SHELL instruction to set the default shell for the RUN instructions.
FROM base_image
# Set default shell to /bin/bash
SHELL ["/bin/bash", "-c"]
RUN echo "Hello, World!"
Use Executable Scripts:
Use executable scripts for complex or reusable commands.
FROM base_image
# Copy script and execute it
COPY script.sh /usr/local/bin/
RUN chmod +x /usr/local/bin/script.sh
RUN script.sh
Use Wildcards for File Operations:
Use wildcards for file operations, such as copying multiple files.
FROM base_image
# Copy all .txt files from the build context
COPY *.txt /app/
By following these guidelines, you can effectively implement run commands in your Dockerfile based on your application's requirements. Adjust the examples to match the specific configuration and commands needed for your project.
list out the checklist of different way to implement User Permissions in dockerfile
Setting user permissions in a Dockerfile is important for improving security by running processes inside the container with the least necessary privilege. Here's a checklist of different ways to implement user permissions in a Dockerfile with examples:
Use the USER Instruction:
Use the USER instruction to set the user or UID (User ID) that the image should run as.
FROM base_image
# Set the user to a non-root user
USER appuser
Create a Non-Root User:
Create a non-root user in your Dockerfile.
FROM base_image
# Create a non-root user
RUN useradd -ms /bin/bash appuser
# Set the user
USER appuser
Use USER with ARG for Flexibility:
Use the USER instruction along with ARG to set the user dynamically during build time.
FROM base_image
ARG USER_ID=1000
# Create a non-root user with dynamic UID
RUN useradd -u $USER_ID -ms /bin/bash appuser
# Set the user
USER appuser
Specify User in Docker Compose:
If using Docker Compose, set the user in the service definition.
version: '3'
services:
your_service:
build:
context: .
dockerfile: Dockerfile
args:
- USER_ID=1000
Use a User-Provided Argument:
Allow users to provide the username and UID during the build process.
FROM base_image
ARG USER_NAME=appuser
ARG USER_ID=1000
# Create a non-root user with user-provided username and UID
RUN useradd -u $USER_ID -ms /bin/bash $USER_NAME
# Set the user
USER $USER_NAME
Use GID for Group ID:
Set both the UID and GID for better user management.
FROM base_image
ARG USER_NAME=appuser
ARG USER_ID=1000
ARG GROUP_ID=1000
# Create a non-root user with user-provided username, UID, and GID
RUN groupadd -g $GROUP_ID $USER_NAME && \
useradd -u $USER_ID -g $GROUP_ID -ms /bin/bash $USER_NAME
# Set the user
USER $USER_NAME
Use External User Databases:
For more complex scenarios, consider using external user databases or LDAP for user management.
FROM base_image
# Use an external user database or LDAP for user management
RUN adduser -D -H -u 1000 -s /bin/bash appuser
# Set the user
USER appuser
Use Build Arguments for Default User:
Allow users to provide a default user during build, but set it to a non-root user by default.
FROM base_image
ARG DEFAULT_USER=appuser
# Create a non-root user with a default username
RUN useradd -ms /bin/bash $DEFAULT_USER
# Set the user
USER $DEFAULT_USER
Use sudo for Limited Privileges:
If needed, use sudo to allow specific commands with elevated privileges for the non-root user.
FROM base_image
# Create a non-root user
RUN useradd -ms /bin/bash appuser
# Install sudo
RUN apt-get update && \
apt-get install -y sudo && \
rm -rf /var/lib/apt/lists/*
# Allow the non-root user to use sudo without a password
RUN echo "appuser ALL=(ALL) NOPASSWD:ALL" > /etc/sudoers.d/appuser
# Set the user
USER appuser
Use Dummy User for Lightweight Images:
For lightweight images, use a dummy user to avoid running as root.
FROM scratch
# Create a dummy user with no home directory
USER nobody
By following these guidelines, you can effectively implement user permissions in your Dockerfile based on your application's requirements. Adjust the examples to match the specific user management and security needs of your project.
list out the checklist of different way to implement User Permissions in dockerfile
Setting user permissions in a Dockerfile is important for improving security by running processes inside the container with the least necessary privilege. Here's a checklist of different ways to implement user permissions in a Dockerfile with examples:
Use the USER Instruction:
Use the USER instruction to set the user or UID (User ID) that the image should run as.
FROM base_image
# Set the user to a non-root user
USER appuser
Create a Non-Root User:
Create a non-root user in your Dockerfile.
FROM base_image
# Create a non-root user
RUN useradd -ms /bin/bash appuser
# Set the user
USER appuser
Use USER with ARG for Flexibility:
Use the USER instruction along with ARG to set the user dynamically during build time.
FROM base_image
ARG USER_ID=1000
# Create a non-root user with dynamic UID
RUN useradd -u $USER_ID -ms /bin/bash appuser
# Set the user
USER appuser
Specify User in Docker Compose:
If using Docker Compose, set the user in the service definition.
version: '3'
services:
your_service:
build:
context: .
dockerfile: Dockerfile
args:
- USER_ID=1000
Use a User-Provided Argument:
Allow users to provide the username and UID during the build process.
FROM base_image
ARG USER_NAME=appuser
ARG USER_ID=1000
# Create a non-root user with user-provided username and UID
RUN useradd -u $USER_ID -ms /bin/bash $USER_NAME
# Set the user
USER $USER_NAME
Use GID for Group ID:
Set both the UID and GID for better user management.
FROM base_image
ARG USER_NAME=appuser
ARG USER_ID=1000
ARG GROUP_ID=1000
# Create a non-root user with user-provided username, UID, and GID
RUN groupadd -g $GROUP_ID $USER_NAME && \
useradd -u $USER_ID -g $GROUP_ID -ms /bin/bash $USER_NAME
# Set the user
USER $USER_NAME
Use External User Databases:
For more complex scenarios, consider using external user databases or LDAP for user management.
FROM base_image
# Use an external user database or LDAP for user management
RUN adduser -D -H -u 1000 -s /bin/bash appuser
# Set the user
USER appuser
Use Build Arguments for Default User:
Allow users to provide a default user during build, but set it to a non-root user by default.
FROM base_image
ARG DEFAULT_USER=appuser
# Create a non-root user with a default username
RUN useradd -ms /bin/bash $DEFAULT_USER
# Set the user
USER $DEFAULT_USER
Use sudo for Limited Privileges:
If needed, use sudo to allow specific commands with elevated privileges for the non-root user.
FROM base_image
# Create a non-root user
RUN useradd -ms /bin/bash appuser
# Install sudo
RUN apt-get update && \
apt-get install -y sudo && \
rm -rf /var/lib/apt/lists/*
# Allow the non-root user to use sudo without a password
RUN echo "appuser ALL=(ALL) NOPASSWD:ALL" > /etc/sudoers.d/appuser
# Set the user
USER appuser
Use Dummy User for Lightweight Images:
For lightweight images, use a dummy user to avoid running as root.
FROM scratch
# Create a dummy user with no home directory
USER nobody
By following these guidelines, you can effectively implement user permissions in your Dockerfile based on your application's requirements. Adjust the examples to match the specific user management and security needs of your project.
list out the checklist of different way to implement Clean up in dockerfile
Cleaning up in a Dockerfile is crucial for optimizing image size and reducing security risks. Here's a checklist of different ways to implement cleanup in a Dockerfile with examples:
Use Multi-Stage Builds:
Utilize multi-stage builds to reduce the size of the final image by discarding unnecessary files from intermediate stages.
# Stage 1: Build stage
FROM base_image as builder
# Build your application
# Stage 2: Final stage
FROM base_image
# Copy only necessary files from the builder stage
COPY --from=builder /app /app
Remove Package Manager Cache:
Remove package manager cache to reduce the image size.
FROM base_image
# Install dependencies
RUN apt-get update && \
apt-get install -y package && \
rm -rf /var/lib/apt/lists/*
Clean Up Temporary Files:
Remove temporary files created during the build process.
FROM base_image
# Download and extract some files
RUN wget -O /tmp/file.tar.gz http://example.com/file.tar.gz && \
tar -zxvf /tmp/file.tar.gz -C /tmp && \
rm /tmp/file.tar.gz
Combine RUN Commands:
Combine multiple RUN commands to reduce the number of layers and optimize image size.
FROM base_image
RUN apt-get update && \
apt-get install -y \
package1 \
package2 \
&& rm -rf /var/lib/apt/lists/*
Remove Unnecessary Files:
Remove unnecessary files and directories to reduce the image size.
FROM base_image
# Copy only necessary files
COPY . /app
# Remove unnecessary files
RUN rm -rf /app/unneeded
Use .dockerignore:
Create a .dockerignore file to exclude unnecessary files and directories during the build process.
Minimize Image Layers:
Minimize the number of image layers by combining commands and using multi-stage builds.
FROM base_image
RUN apt-get update \
&& apt-get install -y \
package1 \
package2 \
&& rm -rf /var/lib/apt/lists/*
Clean apt and YUM Metadata:
Clean package manager metadata to reduce image size.
FROM base_image
RUN apt-get update && \
apt-get install -y package && \
apt-get clean && \
rm -rf /var/lib/apt/lists/*
Use Alpine Linux for Smaller Images:
Consider using Alpine Linux as a base image for smaller image sizes.
FROM alpine:3.14
# Install dependencies
RUN apk --no-cache add package
Remove Build Dependencies:
Remove build dependencies that are no longer needed after the build process.
FROM base_image as builder
# Build your application
# Remove build dependencies
RUN apt-get purge -y build-essential
# Final stage
FROM base_image
# Copy only necessary files from the builder stage
COPY --from=builder /app /app
Clean Up Script:
Create a cleanup script that removes unnecessary files and directories.
FROM base_image
# Copy files
COPY . /app
# Run cleanup script
RUN /app/cleanup.sh
# Your application setup
CMD ["app-start-command"]
Use Multi-Step Docker Compose Files:
Use multi-step Docker Compose files to separate development and production configurations.
version: '3.8'
services:
app:
build:
context: .
dockerfile: Dockerfile.dev
command: ["npm", "start"]
# Dockerfile.dev includes development dependencies
By following these guidelines, you can effectively implement cleanup in your Dockerfile to optimize image size and enhance security.
list out the checklist of different way to implement Health Checks in dockerfile
Implementing health checks in a Dockerfile is crucial for ensuring the availability and reliability of your applications running in containers. Here's a checklist of different ways to implement health checks in a Dockerfile with examples:
Use the HEALTHCHECK Instruction:
Use the HEALTHCHECK instruction to define a command to check the health of the container.
FROM base_image
# Set a basic health check
HEALTHCHECK CMD curl --fail http://localhost:80/ || exit 1
Specify Interval and Timeout:
Specify the interval and timeout for the health check to control how frequently it runs and how long it waits for a response.
FROM base_image
# Set health check with interval and timeout
HEALTHCHECK --interval=5s --timeout=3s CMD curl --fail http://localhost:80/ || exit 1
Use Shell Form and Exec Form:
Use either shell form or exec form for the health check command.
Shell Form:
HEALTHCHECK CMD curl --fail http://localhost:80/ || exit 1
Exec Form:
Dockerfile
Copy code
HEALTHCHECK CMD ["curl", "--fail", "http://localhost:80/"] || exit 1
Use HEALTHCHECK in Docker Compose:
If using Docker Compose, define the health check in the docker-compose.yml file.
version: '3'
services:
your_service:
build: .
healthcheck:
test: ["CMD", "curl", "--fail", "http://localhost:80/"]
interval: 5s
timeout: 3s
retries: 3
Customize Retries:
Customize the number of retries before considering the container unhealthy.
FROM base_image
# Set health check with custom retries
HEALTHCHECK --interval=5s --timeout=3s --retries=3 CMD curl --fail http://localhost:80/ || exit 1
Use Specific Ports:
Specify the ports used by your application in the health check command.
FROM base_image
# Set health check with specific ports
HEALTHCHECK --interval=5s --timeout=3s CMD curl --fail http://localhost:8080/ || exit 1
Use a Dedicated Health Check Script:
Create a dedicated script for the health check and execute it in the Dockerfile.
FROM base_image
# Copy health check script
COPY health-check.sh /usr/local/bin/
# Set health check using the script
HEALTHCHECK CMD /usr/local/bin/health-check.sh
Combine Health Check with Application Startup:
Combine the health check command with the command to start your application.
FROM base_image
# Set health check combined with application start command
HEALTHCHECK CMD curl --fail http://localhost:80/ || exit 1
CMD ["start-your-app"]
Use cURL for HTTP Health Checks:
Use cURL or another tool to perform HTTP health checks.
FROM base_image
# Set health check with cURL for HTTP endpoint
HEALTHCHECK --interval=5s --timeout=3s CMD curl --fail http://localhost:80/ || exit 1
Use Command-Line Health Checks:
Execute command-line health checks specific to your application's requirements.
FROM base_image
# Set health check with command-line checks
HEALTHCHECK CMD /usr/local/bin/check-my-app-health
Use an External Monitoring Tool:
Integrate an external monitoring tool or script for health checks.
FROM base_image
# Copy external health check script
COPY monitor-health.sh /usr/local/bin/
# Set health check using the external script
HEALTHCHECK CMD /usr/local/bin/monitor-health.sh
By following these guidelines, you can effectively implement health checks in your Dockerfile to ensure the proper functioning and availability of your containers. Adjust the examples to match the specific health check requirements of your project.
list out the checklist of different way to implement Logging Configuration: in dockerfile
Configuring logging in a Dockerfile is essential for capturing and managing application logs within containers. However, it's important to note that logging configuration is often specific to the logging mechanism used by the application rather than the Dockerfile itself. Here's a checklist with general considerations and examples on how to handle logging configuration in a Dockerfile:
Understand Logging Mechanism:
Identify the logging mechanism used by your application (e.g., stdout, stderr, log files, syslog) before configuring logging in the Dockerfile.
Leverage STDOUT and STDERR:
Many applications log to the standard output (stdout) and standard error (stderr) streams. Ensure that your application is configured to log to these streams for Docker compatibility.
FROM base_image
# Set up your application
CMD ["my-app"]
Use Environment Variables for Logging Configuration:
Allow users to configure logging parameters using environment variables.
FROM base_image
# Set default logging level
ENV LOG_LEVEL=info
# Configure logging in your application
CMD ["my-app", "--log-level", "$LOG_LEVEL"]
Log to Files Inside the Container:
Configure your application to log to files inside the container. Make sure to include any necessary setup in your Dockerfile.
FROM base_image
# Create a directory for logs
RUN mkdir /app/logs
# Set up your application to log to files
CMD ["my-app", "--log-file", "/app/logs/app.log"]
Configure External Logging Drivers:
If using Docker logging drivers (e.g., JSON file, syslog, fluentd), configure them through Docker Compose or other orchestration tools.
version: '3'
services:
your_service:
image: your_image
logging:
driver: syslog
options:
syslog-address: "udp://logs.example.com:514"
Integrate with Logging Agents:
If using logging agents or centralized logging solutions, ensure your application is configured to send logs to the appropriate endpoint.
FROM base_image
# Set up your application to send logs to a centralized logging server
CMD ["my-app", "--log-server", "logs.example.com"]
Use Log Rotation:
Implement log rotation to manage log file sizes and prevent them from growing indefinitely.
FROM base_image
# Install logrotate
RUN apt-get update && \
apt-get install -y logrotate && \
rm -rf /var/lib/apt/lists/*
# Add logrotate configuration
COPY logrotate.conf /etc/logrotate.conf
# Set up your application to log to files
CMD ["my-app", "--log-file", "/app/logs/app.log"]
Consider Log Formatting Options:
Explore and configure log formatting options based on your application's needs.
FROM base_image
# Set log format as a build argument
ARG LOG_FORMAT=json
# Configure your application with the specified log format
CMD ["my-app", "--log-format", "$LOG_FORMAT"]
Create Custom Logging Configuration Files:
Include custom logging configuration files in your image and configure your application to use them.
FROM base_image
# Copy custom logging configuration file
COPY logging.conf /etc/my-app/logging.conf
# Configure your application to use the custom logging configuration
CMD ["my-app", "--log-config", "/etc/my-app/logging.conf"]
Use Logging Libraries in the Application Code:
Utilize logging libraries in your application code that allow for flexible configuration and integration with various logging backends.
FROM base_image
# Set default log level
ENV LOG_LEVEL=info
# Configure your application to use a logging library with environment variable support
CMD ["my-app", "--log-level", "$LOG_LEVEL"]
Remember that logging configuration often depends on the specific logging solution and the application's logging capabilities. Adjust the examples to match your
list out the checklist of different way to implement Security Considerations
Ensuring security in Dockerfiles is critical to building secure containerized applications. Here's a checklist of different ways to implement security considerations in a Dockerfile with examples:
Use Official Base Images:
Start with official base images from trusted sources like Docker Hub to ensure a secure foundation.
FROM ubuntu:20.04
Update and Upgrade Packages:
Keep the base image and packages up-to-date by running package manager updates during the image build.
FROM base_image
# Update and upgrade packages
RUN apt-get update && \
apt-get upgrade -y && \
rm -rf /var/lib/apt/lists/*
Minimize the Number of Layers:
Minimize the number of layers in your Dockerfile to reduce the attack surface and improve image size.
FROM base_image
# Combine commands to reduce layers
RUN apt-get update && \
apt-get install -y package && \
rm -rf /var/lib/apt/lists/*
Non-Root User:
Run your application as a non-root user to limit potential security risks.
FROM base_image
# Create a non-root user
RUN useradd -ms /bin/bash appuser
# Set the user
USER appuser
Use COPY Instead of ADD:
Prefer the COPY instruction over ADD to copy files into the image, as COPY is more explicit and doesn't have the potential for unintended behavior.
FROM base_image
# Copy application files
COPY . /app
Limit Capabilities with --cap-drop and --cap-add:
Drop unnecessary Linux capabilities and only add the required ones to minimize privileges.
FROM base_image
# Drop unnecessary capabilities
RUN setcap -r /path/to/binary
# Add specific capabilities if needed
RUN setcap cap_net_bind_service=+ep /path/to/binary
Use COPY with --chown to Set Ownership:
Set ownership of copied files explicitly using --chown to avoid potential security risks.
FROM base_image
# Copy and set ownership
COPY --chown=appuser:appuser . /app
Set Environment Variables Securely:
Avoid sensitive information in plain text by setting environment variables securely.
FROM base_image
# Set sensitive environment variable
ENV SECRET_KEY=${SECRET_KEY}
Avoid Running SSH in Containers:
Minimize security risks by avoiding the installation and use of SSH in your containers.
FROM base_image
# Avoid installing SSH
Clean Up After Installations:
Remove unnecessary files and cleanup after package installations to reduce the image size and potential security vulnerabilities.
FROM base_image
# Install packages
RUN apt-get update && \
apt-get install -y package && \
rm -rf /var/lib/apt/lists/*
Implement Health Checks:
Implement health checks to ensure that the application is running correctly within the container.
FROM base_image
# Set health check
HEALTHCHECK CMD curl --fail http://localhost:80/ || exit 1
Use Multi-Stage Builds:
Utilize multi-stage builds to separate build dependencies from the final production image, reducing the attack surface.
# Stage 1: Build stage
FROM build_image as builder
# Build your application
# Stage 2: Final stage
FROM base_image
# Copy only necessary files from the builder stage
COPY --from=builder /app /app
Implement Network Segmentation:
If possible, implement network segmentation to restrict network access for containers.
FROM base_image
# Set up network segmentation if applicable
Regularly Update Base Images:
Regularly check for updates to your base images and update them to address any security vulnerabilities.
FROM base_image:latest
Scan Images for Vulnerabilities:
Use container security tools to regularly scan your Docker images for vulnerabilities.
# Integrate a security scanning tool
These considerations provide a foundation for enhancing security in Dockerfiles. Customize them based on your application's specific requirements and the security best practices recommended for your chosen technology stack.
list out the checklist of different way to implement Version Control and Tagging in dockerfile
Implementing version control and tagging in a Dockerfile is important for tracking changes, ensuring reproducibility, and managing the lifecycle of Docker images. Here's a checklist of different ways to implement version control and tagging in a Dockerfile with examples:
Use Versioned Base Images:
Start with versioned base images to ensure consistency across builds and avoid unexpected changes.
FROM base_image:2.0.1
Specify Full Base Image Digest:
Specify the full image digest to ensure that a specific, unmodified version of the base image is used.
FROM base_image@sha256:abc123def456...
Use Versioned Package Installations:
Version-lock dependencies in your Dockerfile to maintain consistency and avoid unexpected updates.
FROM base_image
# Install a specific version of a package
RUN apt-get update && \
apt-get install -y package=1.2.3 && \
rm -rf /var/lib/apt/lists/*
Label Dockerfile with Version Information:
Use labels in your Dockerfile to include version information, build numbers, or other metadata.
FROM base_image
# Label Dockerfile with version information
LABEL version="1.0" \
description="My Application Version 1.0" \
maintainer="author@example.com"
Use ARG for Dynamic Versioning:
Allow dynamic versioning during the build process using build arguments.
FROM base_image
ARG APP_VERSION=1.0.0
# Use dynamic version in labels
LABEL version=$APP_VERSION
# Use dynamic version in CMD or ENTRYPOINT
CMD ["my-app", "--version", "$APP_VERSION"]
Tag Images for Different Environments:
Use different tags for images built for different environments (e.g., development, production).
Dockerfile
Copy code
FROM base_image:latest as development
# Development-specific configurations
FROM base_image:production as production
# Production-specific configurations
Implement Semantic Versioning:
Follow semantic versioning principles for labeling versions, making it easier to understand the impact of changes.
FROM base_image
# Use semantic versioning
LABEL version="2.1.0"
Automate Image Tagging with CI/CD:
Automate the tagging process using continuous integration/continuous deployment (CI/CD) pipelines.
# Example CI/CD configuration (e.g., GitLab CI)
stages:
- build
- deploy
build:
stage: build
script:
- docker build -t my-app:${CI_COMMIT_REF_NAME} .
deploy:
stage: deploy
script:
- docker push my-app:${CI_COMMIT_REF_NAME}
Include Source Code Version Information:
Include source code version information in the Dockerfile to tie images to specific code versions.
FROM base_image
# Include source code version
ARG SOURCE_CODE_VERSION=main
# Use version in CMD or ENTRYPOINT
CMD ["my-app", "--source-code-version", "$SOURCE_CODE_VERSION"]
Leverage Multi-Stage Builds for Versioned Artifacts:
Use multi-stage builds to fetch versioned artifacts during the build process.
# Stage 1: Build stage
FROM build_image as builder
# Fetch versioned artifacts
RUN fetch-artifacts --version 1.2.3
# Stage 2: Final stage
FROM base_image
# Copy artifacts from the builder stage
COPY --from=builder /app /app
Automate Image Tagging with Git Tags:
Automate image tagging using Git tags to mark specific points in your project's history.
# Example Git tag-based image tagging in CI/CD
script:
- export TAG_NAME=$(git describe --tags)
- docker build -t my-app:${TAG_NAME} .
- docker push my-app:${TAG_NAME}
Use External Version Files:
Store version information in external files and copy them into the Docker image during the build.
FROM base_image
# Copy external version file
COPY version.txt /app/version.txt
# Use version information
CMD ["my-app", "--version", "$(cat /app/version.txt)"]
By following these guidelines, you can effectively implement version control and tagging in your


Top comments (0)