how to Keep the system up to date for securing linux server with examples
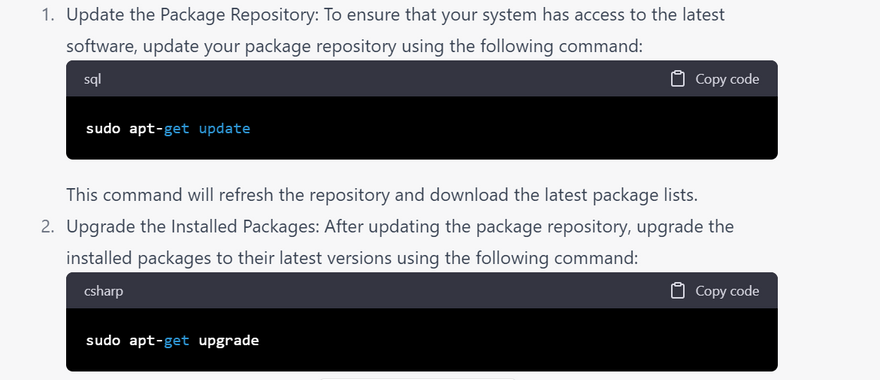
Update the operating system
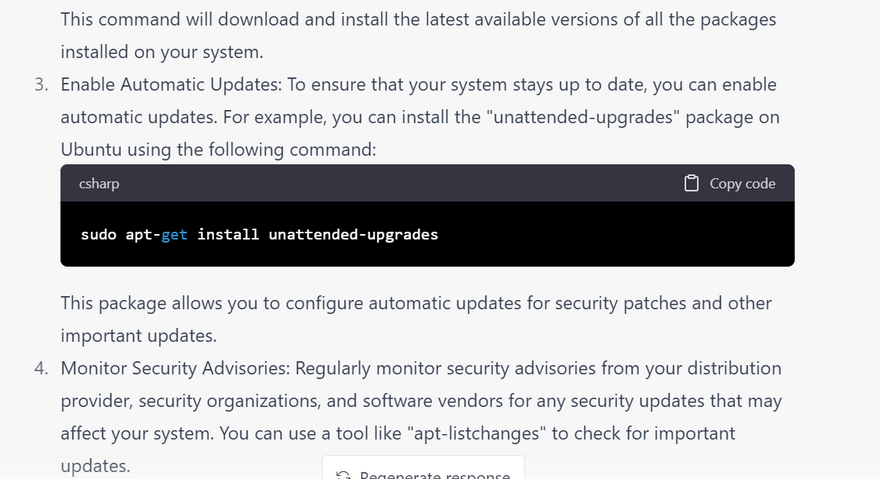
Install security updates
Check for updates regularly:
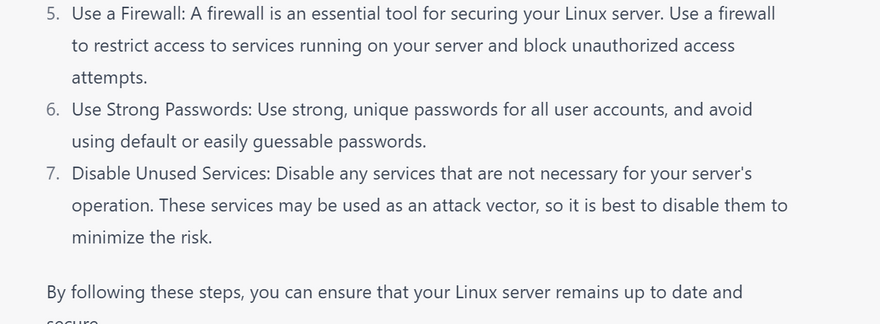
Use a firewall
Use a software package manager
strong password
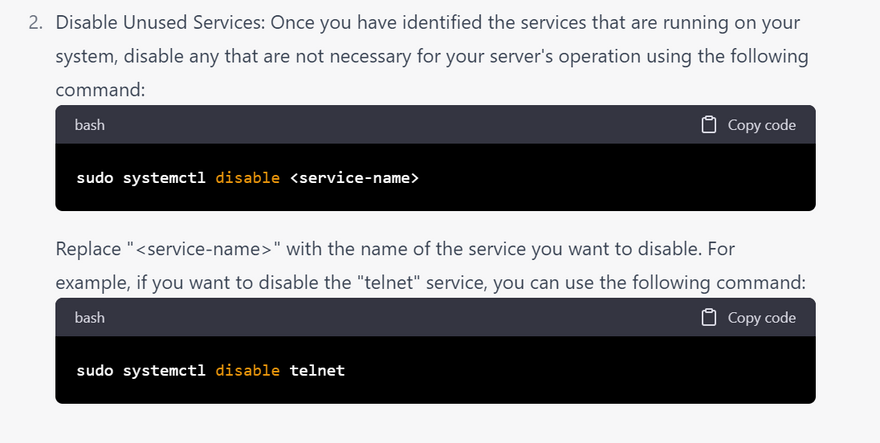
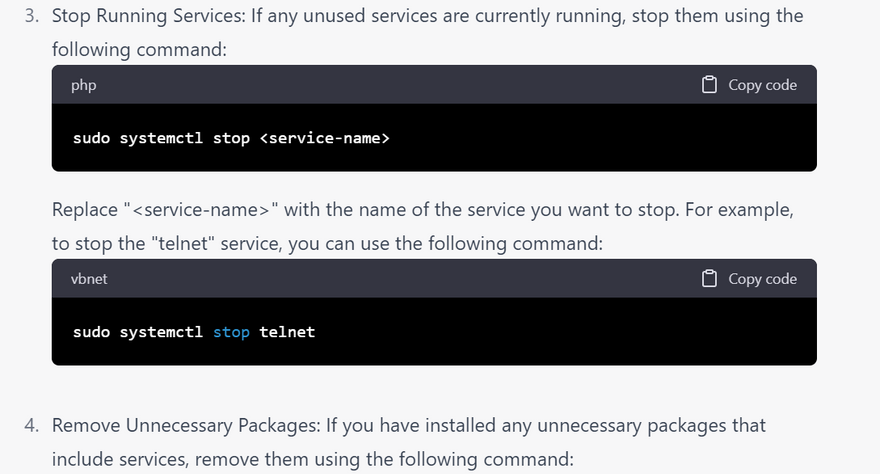
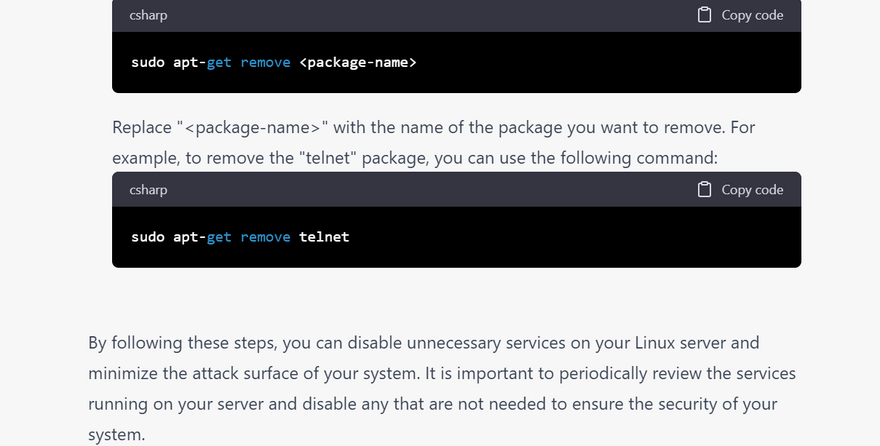
disable unused servie
Use a firewall
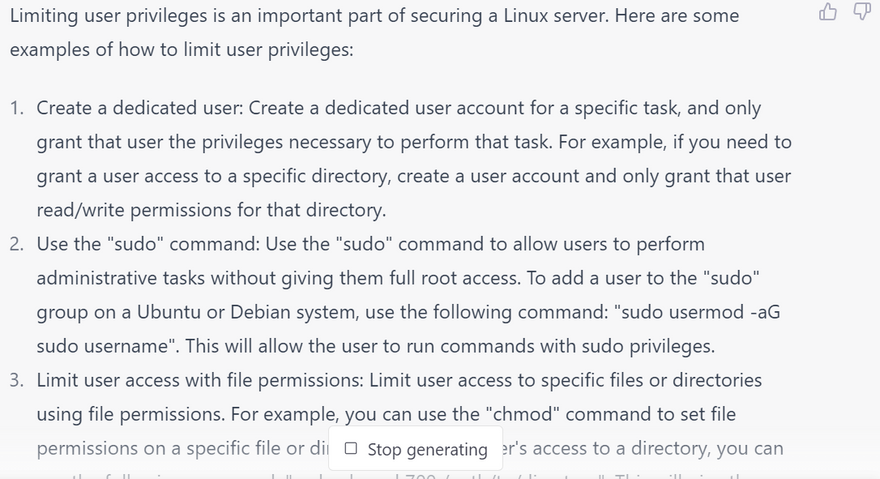
Limit user privileges
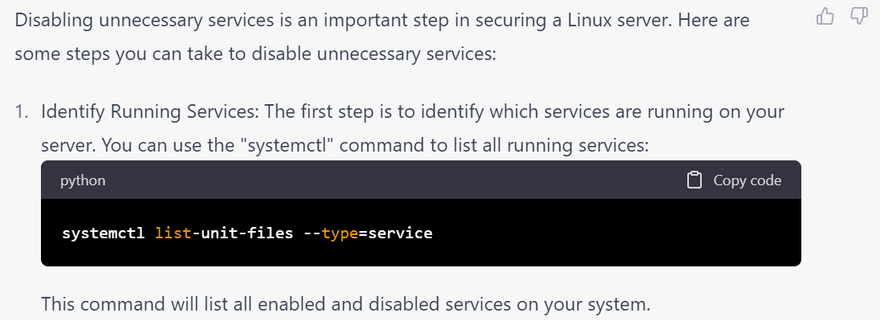
how to Disable unnecessary services for securing linux server with examples
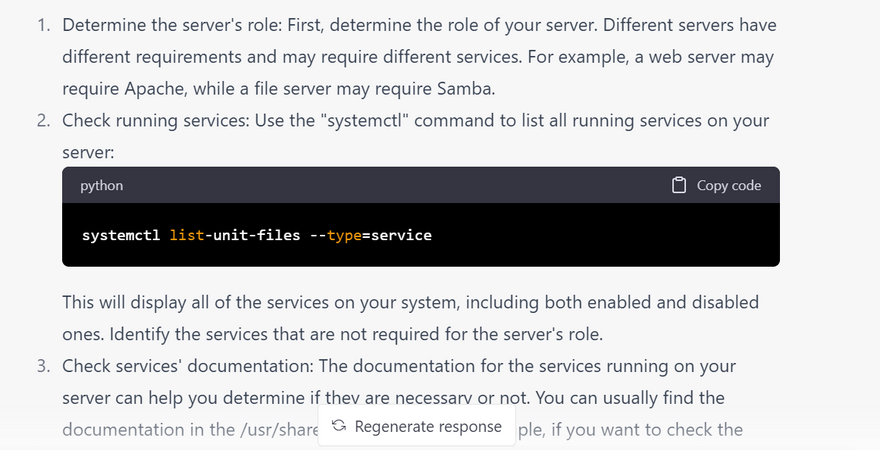
Identify the services running on the server
Identify which services are unnecessary
Disable the unnecessary services
how Limit user access with file permissions for securing linux server with examples
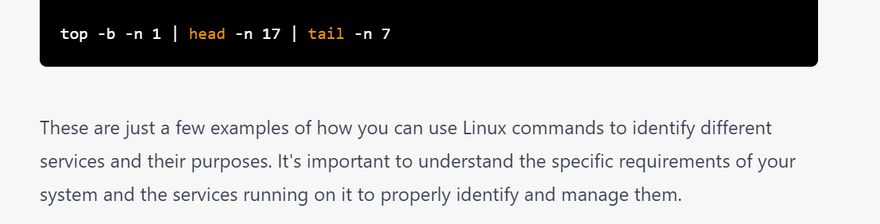
how to identify different servies purpose using linux commands with examples
systemctl
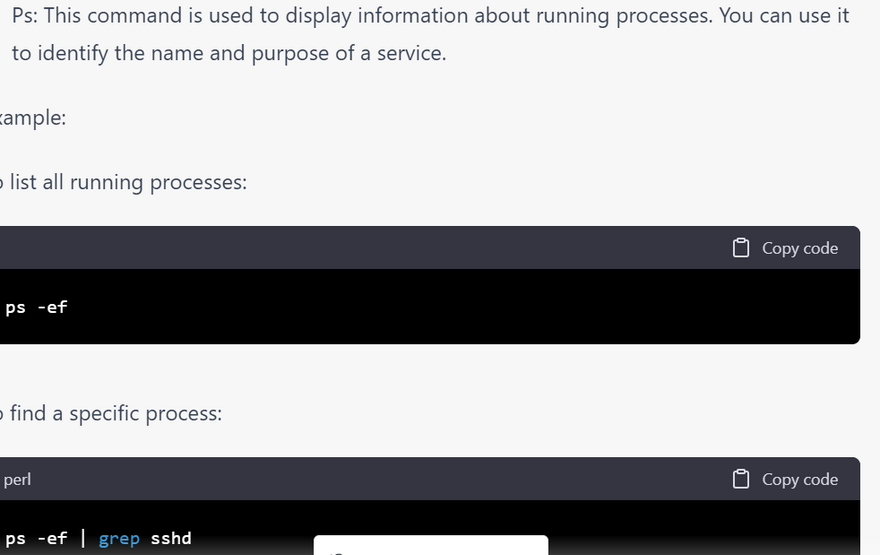
ps
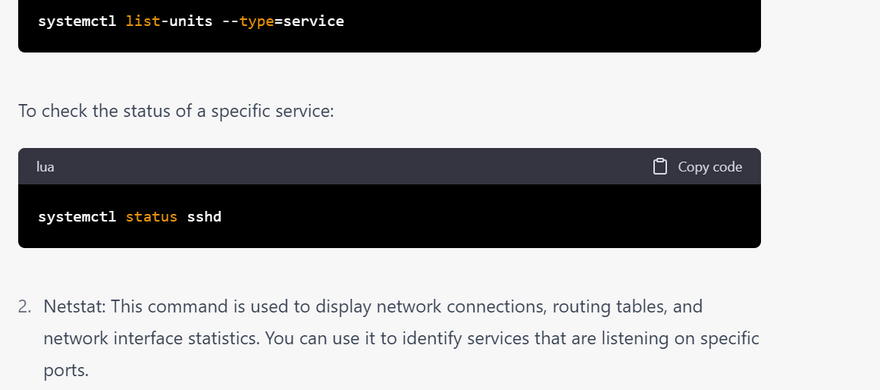
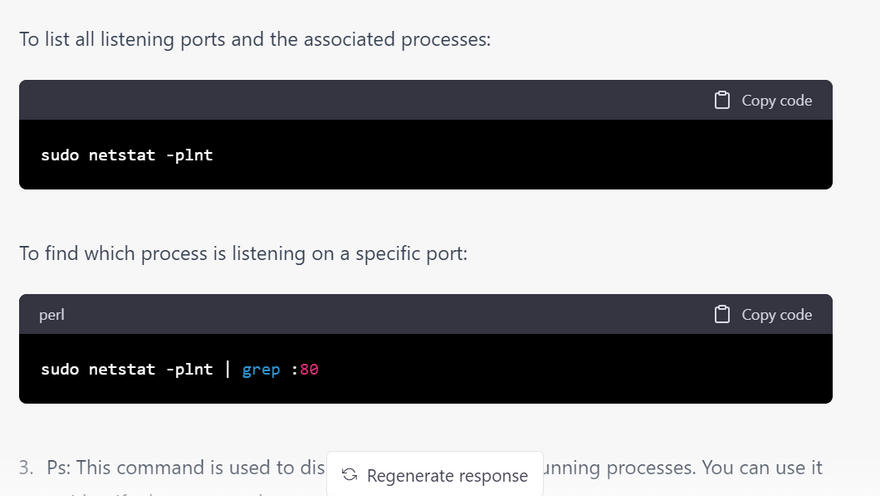
netstat
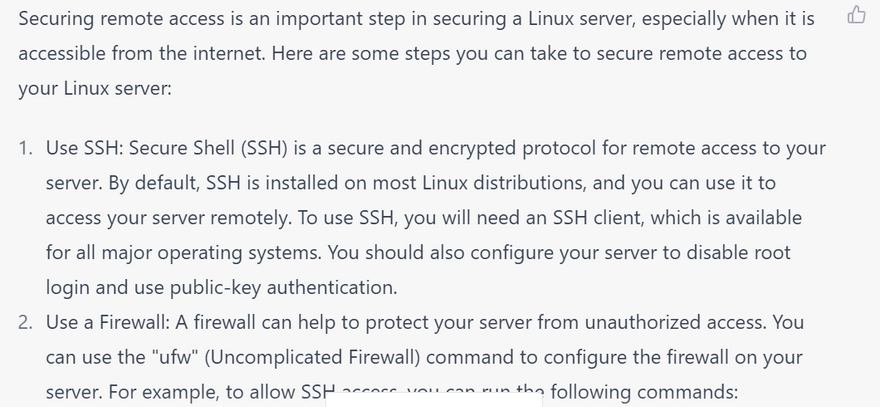
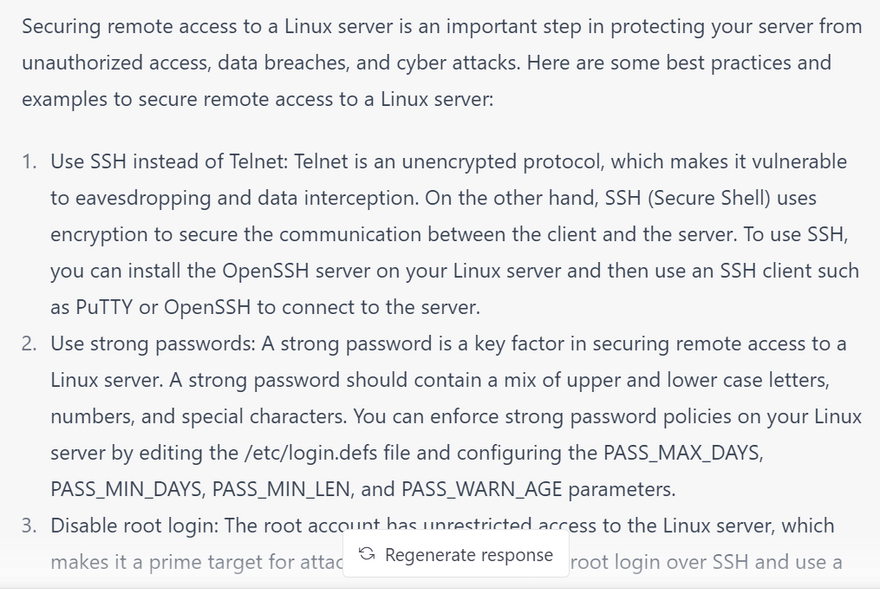
How to Secure remote access for securing linux server with examples
Use SSH for remote access
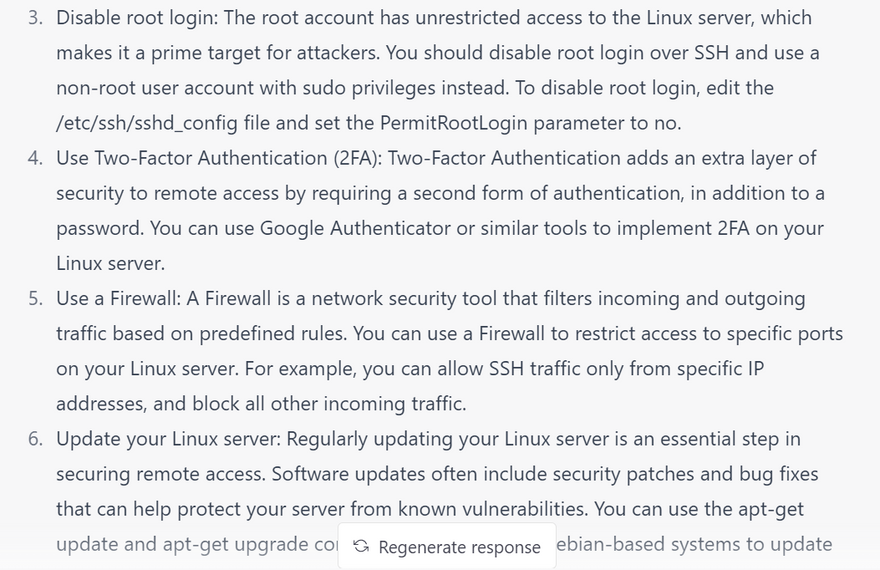
Disable root login
Use strong passwords
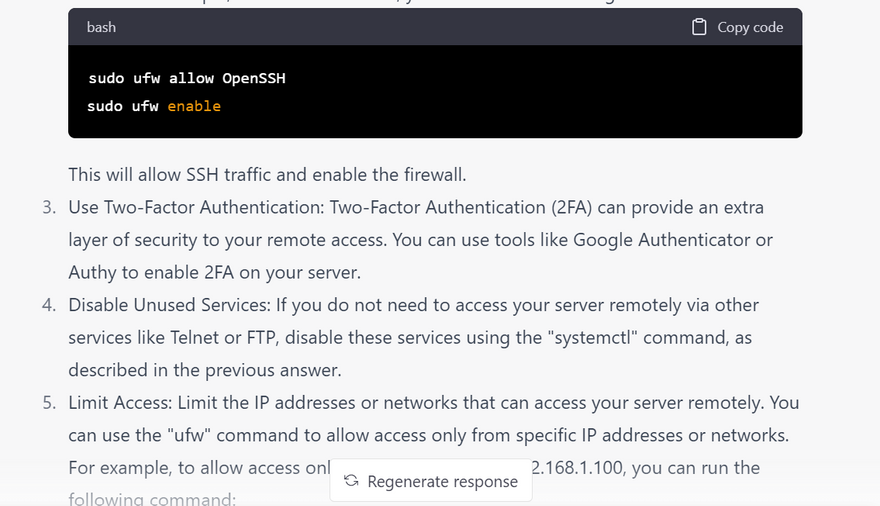
Enable Two-factor Authentication (2FA)
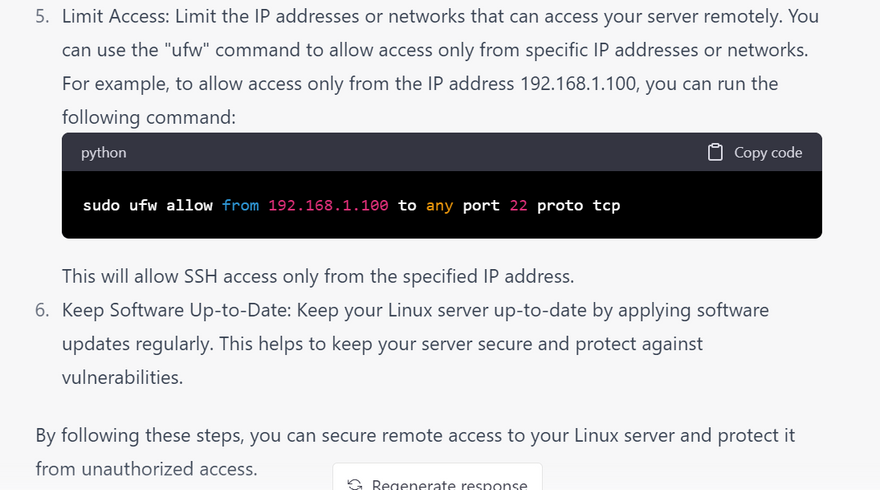
Limit IP address access
Securing a Linux server involves taking a variety of measures to prevent unauthorized access, protect sensitive data, and ensure system availability. Here are some best practices for securing a Linux server:
Keep the system up to date: Regularly update the system with the latest patches and security updates to address known vulnerabilities.
Use a firewall: Configure a firewall to restrict incoming and outgoing network traffic to only the necessary services and ports.
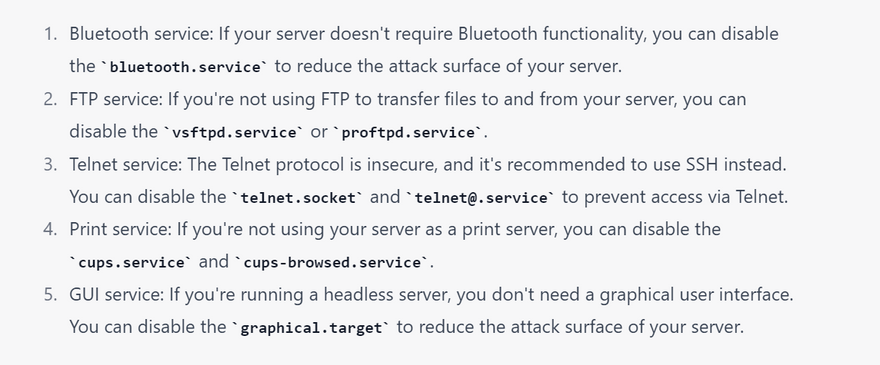
Disable unnecessary services: Turn off any unnecessary services that are not required for the server's operation. This reduces the attack surface and minimizes the risk of exploits.
Use strong passwords: Use strong passwords that are difficult to guess and change them regularly. Consider using a password manager to generate and store strong passwords.
Limit user privileges: Only grant users the privileges they need to do their job. Avoid giving users root access or allowing them to log in as the root user.
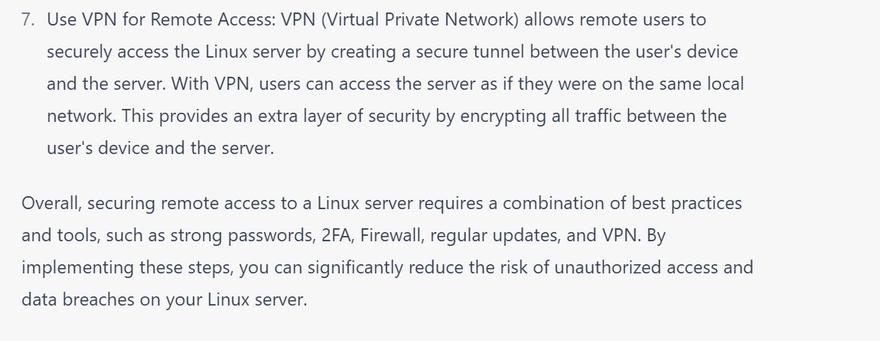
Secure remote access: Use secure remote access methods such as SSH and VPNs. Disable any unused remote access protocols and restrict access to only authorized users.
Monitor system logs: Regularly check system logs for signs of suspicious activity or potential security breaches.
Use encryption: Use encryption to protect sensitive data in transit and at rest. This includes encrypting network traffic, file systems, and backups.
Enable two-factor authentication: Enable two-factor authentication for user accounts to provide an additional layer of security.
Use security tools: Use security tools such as intrusion detection systems, antivirus software, and security scanners to identify and prevent security threats.
how to Keep the system up to date for securing linux server with examples
Use a firewall
how to Disable unnecessary services for securing linux server with examples
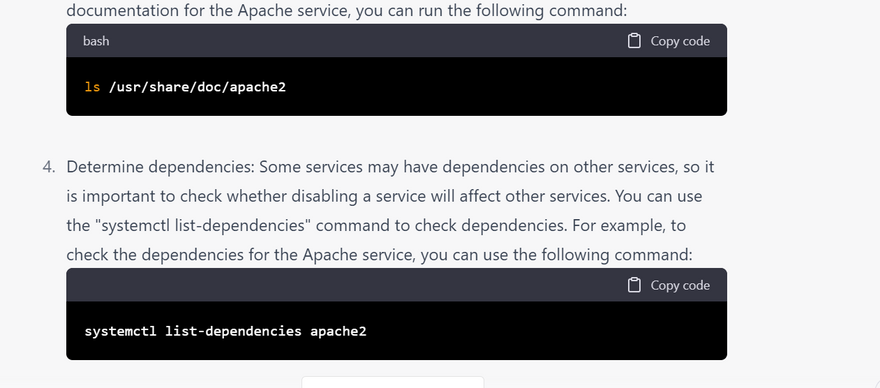
how to know what are the unnecessary services for securing linux server with examples
To determine which services are unnecessary on your Linux server, you can follow these steps:
how to identify different servies purpose using linux commands with examples
In Linux, there are several commands that can help you identify different services and their purposes. Here are a few examples:
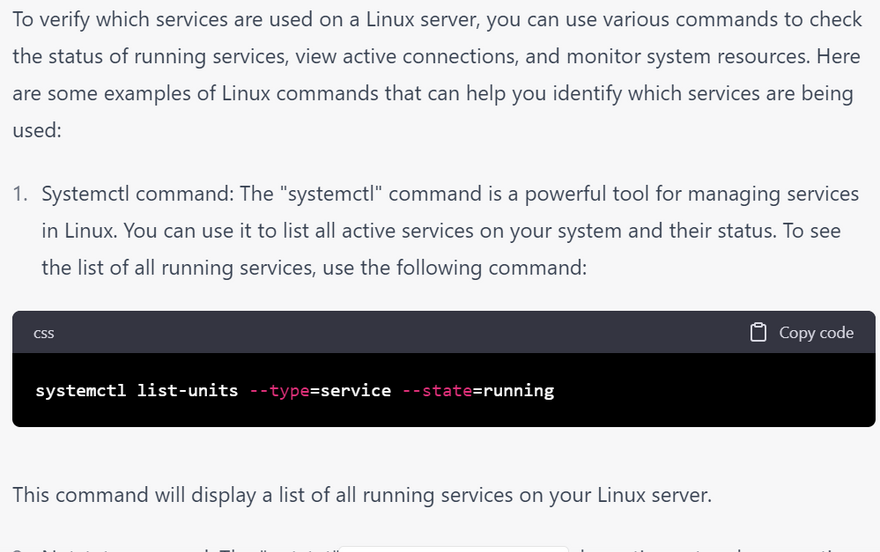
Systemctl: This command is used to control the system's systemd system and service manager. You can use it to identify the status, type, and purpose of a service.
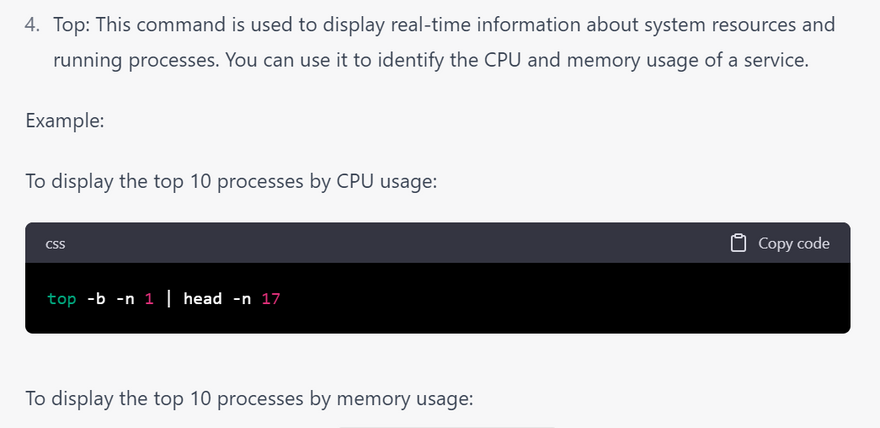
Example:
To list all services and their status:
Limit user privileges
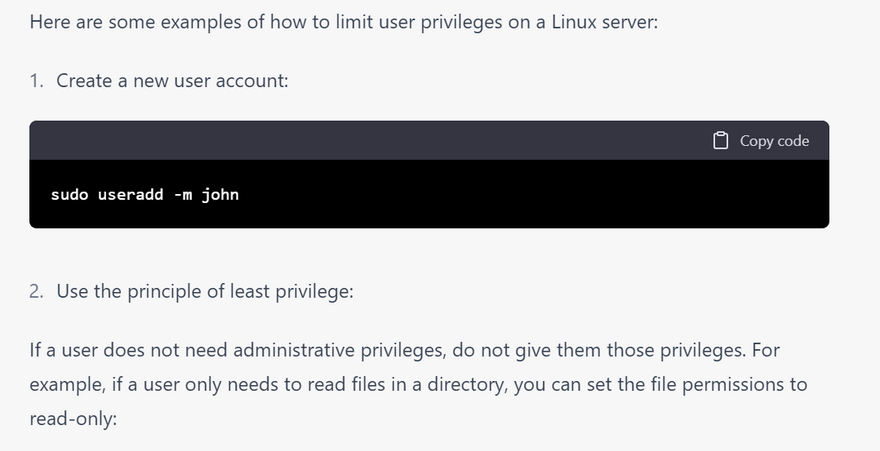
Use the principle of least privilege: Use the principle of least privilege to restrict user access to only the resources they need to perform their job. For example, if a user does not need administrative privileges, do not give them those privileges.
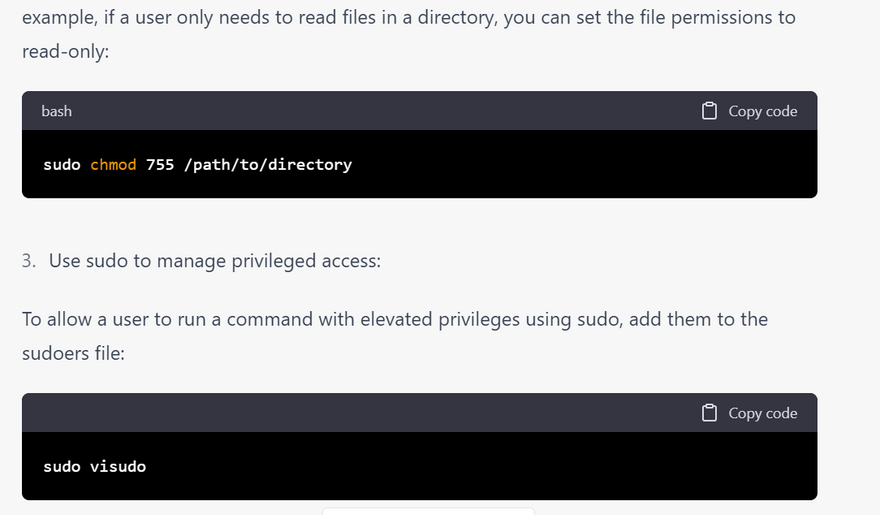
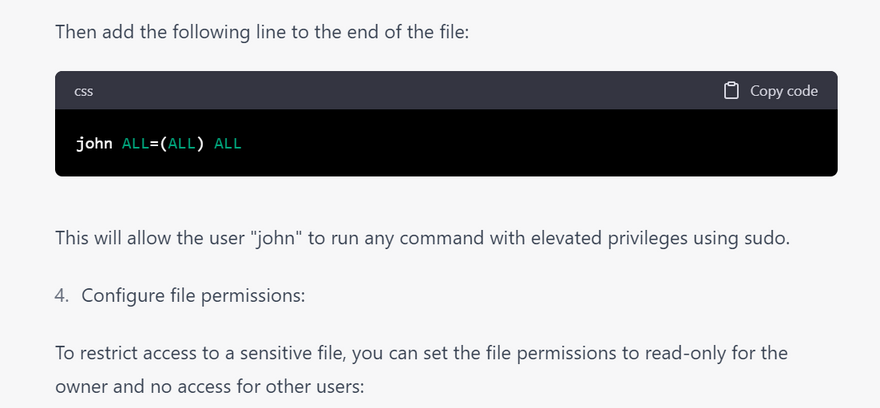
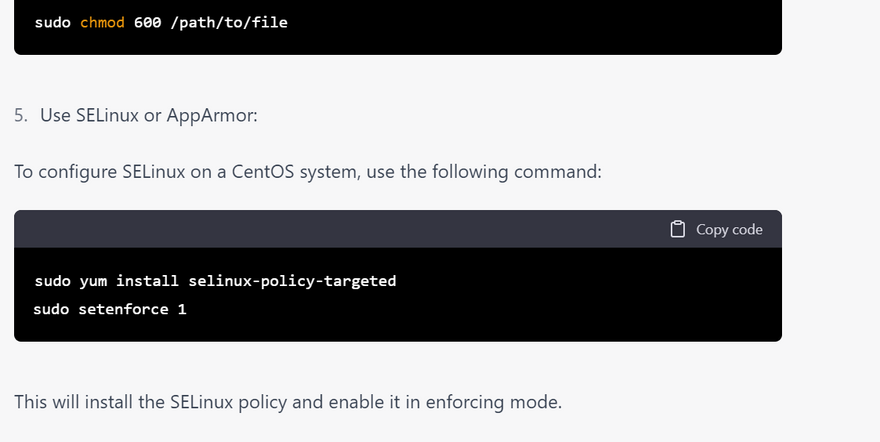
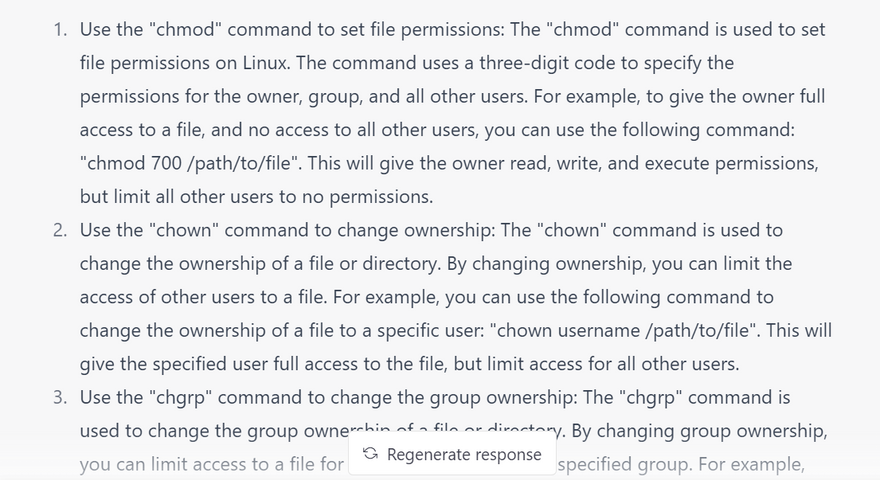
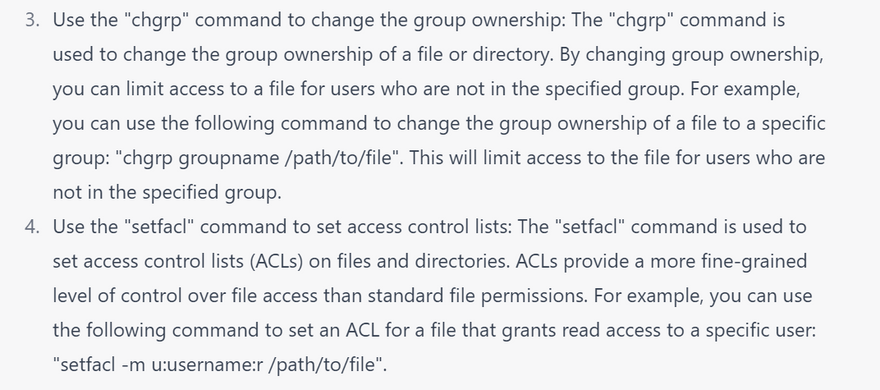
Configure file permissions: Use file permissions to restrict access to sensitive files and directories. You can use the chmod command to set file permissions, and the chown command to set ownership of files and directories.
Use SELinux or AppArmor: Use a mandatory access control system such as SELinux or AppArmor to enforce access controls and restrict user access to system resources.


Top comments (0)