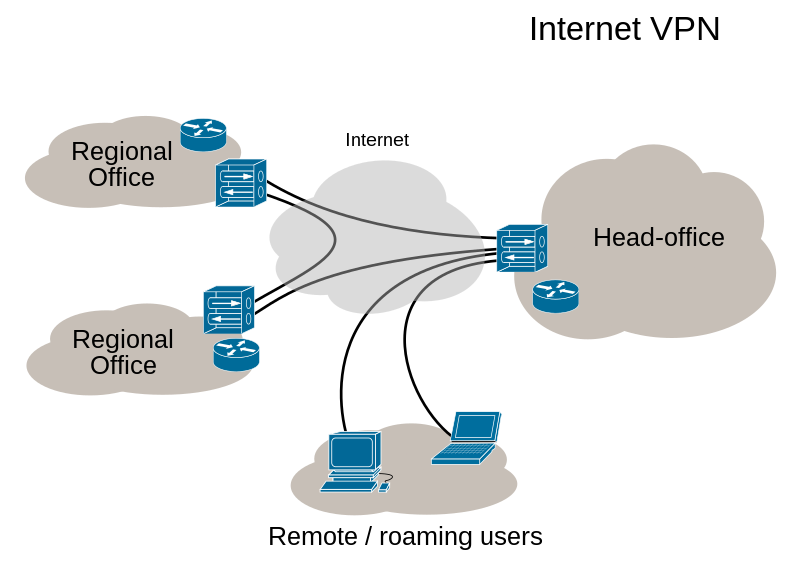
A virtual private network is a mechanism for creating a secure connection between a computing device and a computer network, or between two networks, using an insecure communication medium such as the public Internet
Let's go through a few examples to illustrate how VPNs work in different scenarios:
- Remote Work: Scenario:
User: Alice, an employee of XYZ Corp, needs to access the company's internal resources from her home.
Challenge: Ensuring a secure connection between Alice's home and the company's internal network.
Solution:
- XYZ Corp sets up a Remote Access VPN.
- Alice installs a VPN client on her device.
- When Alice connects to the VPN, her internet traffic is encrypted and securely transmitted to the company's network.
- She can now access internal files, databases, and applications as if she were physically present in the office .
- Online Privacy: Scenario:
User: Bob wants to enhance his online privacy and protect his data from potential snoopers on public Wi-Fi networks.
Challenge: Insecure public Wi-Fi networks pose a risk to the confidentiality of Bob's data.
Solution:
- Bob subscribes to a commercial VPN service.
- He installs the VPN app on his device.
- When Bob connects to the VPN, his internet traffic becomes encrypted.
- Even when using public Wi-Fi, the VPN protects his data from potential eavesdropping or malicious activities .
- Overcoming Geographical Restrictions: Scenario:
User: Charlie wants to access a streaming service that is restricted in his country.
Challenge: The streaming service is only available to users in specific geographic regions.
Solution:
- Charlie subscribes to a VPN service with servers in a country where the streaming service is accessible.
- He connects to the VPN server in that country.
- The streaming service sees Charlie's connection as originating from the VPN server's location.
- Charlie can now access the streaming service as if he were physically located in that country .
- Business Connectivity: Scenario:
Company: ABC Inc has branch offices in different cities that need secure communication.
Challenge: Ensuring secure and private communication between the offices over the internet.
Solution:
- ABC Inc deploys Site-to-Site VPNs between its branch offices.
- The VPNs create secure tunnels over the internet.
- Employees at each branch can securely access resources at other branches.
- Data transmitted between branches is encrypted, ensuring confidentiality and integrity .
- Anonymous Browsing: Scenario:
User: Dave wants to browse the internet without revealing his IP address.
Challenge: Websites and services track users based on their IP addresses, compromising privacy.
Solution:
- Dave uses a VPN to hide his real IP address.
- He connects to a VPN server in a different location.
- Websites and online services only see the IP address of the VPN server.
- Dave's online activities remain anonymous, and his real IP address is not exposed . These examples showcase the versatility of VPNs in addressing various challenges related to security, privacy, and access. Whether for individual use or within a corporate environment, VPNs offer a powerful solution to ensure secure and private communication over the internet.
VPN IN AWS
What is Virtual Private Network?
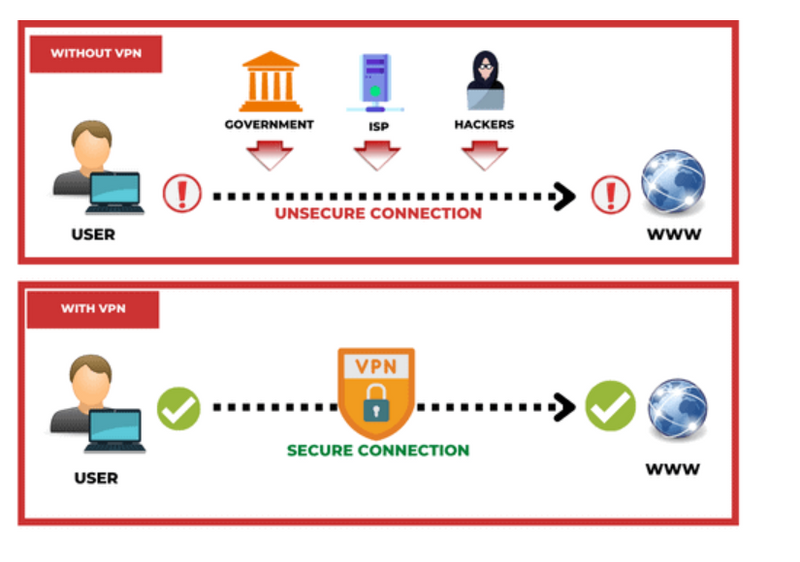
VPN (Virtual Private Network) refers to the ability to establish a secure network connection when using public networks. VPNs mask your online identity and encrypt your internet activity. This makes it more challenging for outside parties to monitor your internet activities and steal data. Real-time encryption is employed.
What is AWS VPN?
AWS Virtual Private Network (VPN) solutions connect your on-premises networks, distant offices, client devices, and the AWS global network in a secure manner. AWS Client VPN and AWS Site-to-Site VPN are the two services that make up this system. Each service offers a managed, scalable, and highly available cloud VPN solution to secure your network traffic.
Components of AWS VPN
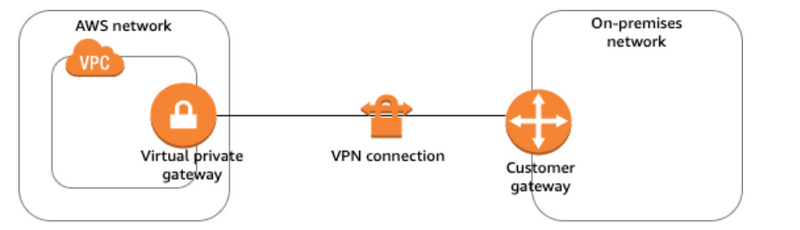
Virtual Private Gateway – VGW
A virtual private gateway is the VPN concentrator on the AWS side of the VPN connection
Customer Gateway – CGW
A customer gateway is a physical device or software application located on the customer side of the VPN connection.
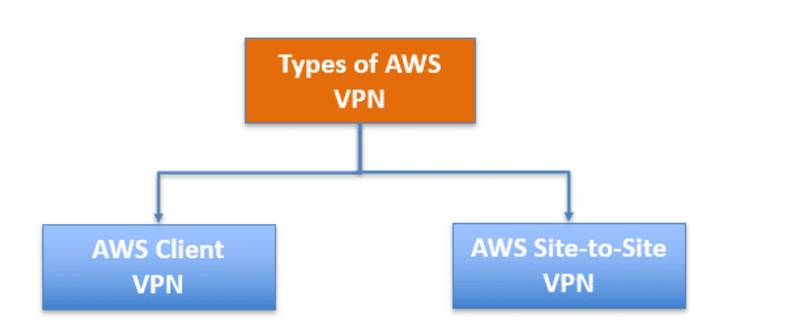
Types of AWS VPN
It provides two private connectivity options with the high availability and strong security your data needs:
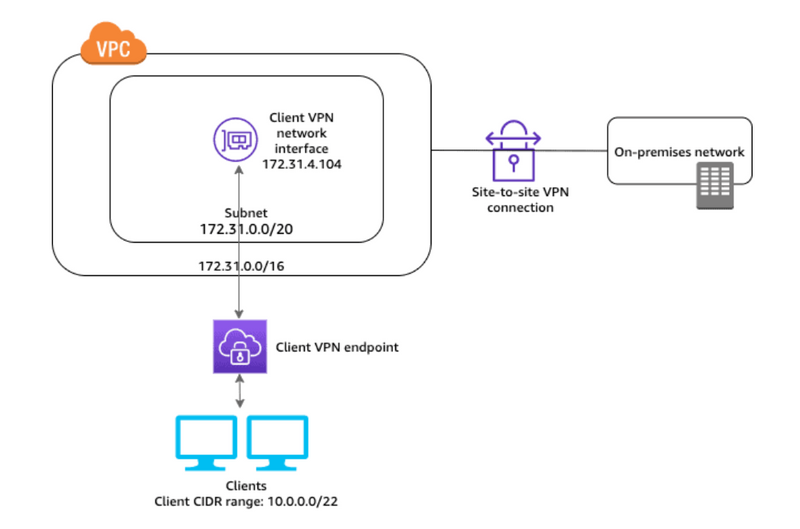
AWS Client VPN:
It is a fully managed remote access VPN solution that allows your distant employees to safely access resources on AWS as well as your on-premises network. It automatically adjusts up or down dependent on demand because it is fully elastic. Your users can access your applications in the same way before, during, and after the transfer to AWS.
The OpenVPN protocol is supported by AWS Client VPN, including the software client.
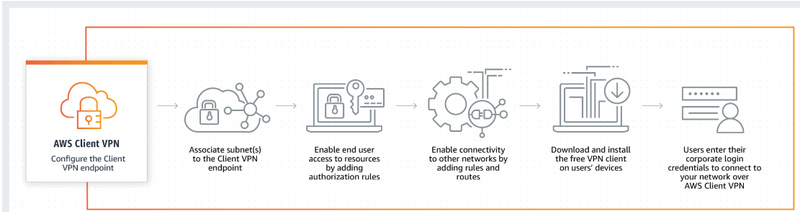
How it works
Use Cases:
Quickly scale remote access: Many of your employees could have to work remotely due to unforeseen circumstances. Due to the increase in VPN connections and traffic, your users’ experience may suffer in terms of performance or availability.
Access applications during migration: Users can securely access applications both on-premises and on AWS thanks to AWS Client VPN. This is useful when moving apps from on-premises sites to the cloud during a cloud migration.
Integrate with your authentication and MDM systems: When utilising the AWS-provided OpenVPN Client software, AWS Client VPN enables authentication using Microsoft Active Directory using AWS Directory Services, Certificate-based authentication, and Federated Authentication using SAML-2.0.
Securely connecting IoT devices: Utilizing certificate-based authentication, establish secure connections between IoT devices and Amazon Virtual Private Cloud (VPC) resources.
Features:
Authentication: Either Active Directory or certificates will be used for authentication. It works with AWS Directory Services, which links to your existing on-premises Active Directory, thus it does not require you to duplicate data from your existing Active Directory to the cloud.
Authorization: It offers network-based authorization, allowing you to create access control rules based on Active Directory groups that restrict access to particular networks.
Secure connectivity: It encrypts the traffic using the safe TLS VPN tunnel protocol. Each Client VPN endpoint terminates a separate VPN tunnel that gives users access to both on-premises and AWS services.
Connection management: Amazon CloudWatch Logs can be used to monitor, store, and access log files from AWS Client VPN connection logs. The associated log data can then be obtained from CloudWatch Logs.
Compatibility with your employees’ devices: Devices can be connected to your network using it. Employees have the flexibility to utilize any device they like, including Windows, Mac, iOS, Android, and Linux-based devices, thanks to its selection of OpenVPN-based clients.
Pricing
You are billed for the number of active client connections per hour and the number of linked subnets with Client VPN per hour in AWS Client VPN.
AWS Site-to-Site VPN:
It is a fully managed service that uses IP Security (IPSec) tunnels to establish a secure link between your data centre or branch office and your AWS resources. You can connect to both your Amazon Virtual Private Clouds (VPC) and the AWS Transit Gateway when utilizing it, and two tunnels are used for each connection to increase redundancy.
The Accelerated Site-to-Site VPN option, which works with AWS Global Accelerator to dynamically route your traffic to the closest AWS network endpoint with the best speed, offers even better performance for internationally distributed applications.
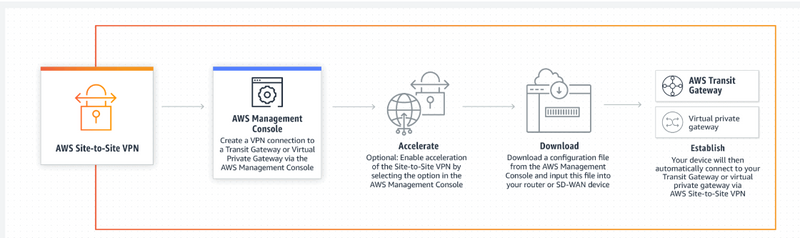
How it works
Use Cases:
Application Migration: A Site-to-site VPN connection between your network and the AWS cloud makes moving applications to the cloud easier. You can host Amazon VPCs behind your corporate firewall and migrate your IT resources without disrupting your users’ access to these applications.
Secure communication between remote locations: AWS Site-to-Site VPN connections can be used to securely communicate between remote sites.
Features:
Secure connectivity: It employs OpenVPN, which negotiates data channel parameters over a TLS encrypted control channel.
High availability: With AWS Direct Connect, you can create failover and CloudHub solutions. CloudHub allows your remote sites to communicate with one another as well as with the VPC.
Customization: It provides tunnel customization options such as inside tunnel IP address, pre-shared key, and Border Gateway Protocol Autonomous System Number (BGP ASN).
Network Address Translation (NAT) Traversal: It supports NAT Traversal applications, allowing you to use private IP addresses behind routers on private networks with a single public IP address facing the internet.
Private IP VPN: Private IP VPN enables the use of private IP addresses to deploy site-to-site VPN connections over Direct Connect (DX).
Monitoring: It can send metrics to CloudWatch to improve visibility and monitoring. CloudWatch also lets you send your own custom metrics and add data points in any order and rate you want.
Pricing
You are charged for each VPN connection hour that your VPN connection is provisioned and available if you create an AWS Site-to-Site VPN connection to your Amazon VPC. Each hour of partial VPN connection consumption is billed as a full hour. All data transferred via the VPN connection is also subject to standard AWS data transfer charges.
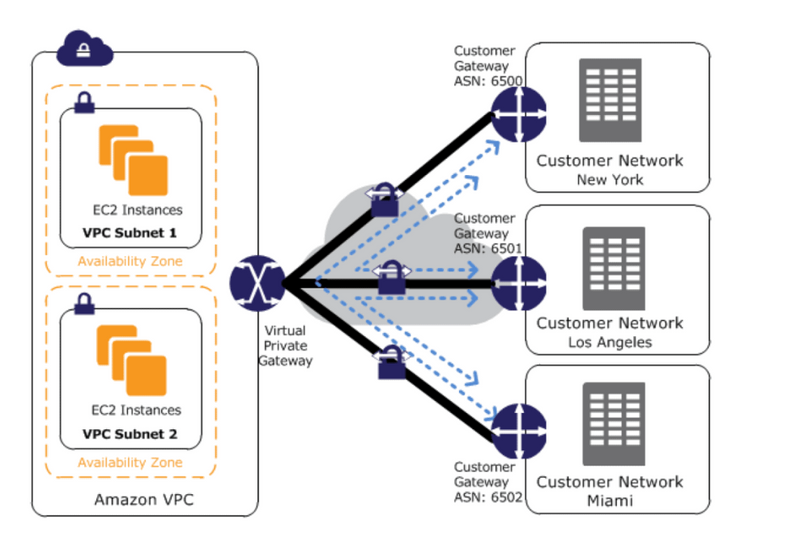
VPN CloudHub
If you have multiple VPN connections, it can be used to provide secure communication between multiple on-premises sites. It uses a Virtual Private gateway in a detached mode that can be used without a VPC and operates on a simple hub-and-spoke model.
VPN CloudHub architecture with blue dashed lines indicates network traffic being routed between remote sites via VPN connections. CloudHub necessitates the use of a virtual private gateway with multiple customer gateways.
To configure the CloudHub:
Multiple customer gateways can be created, each with its own unique public IP address and ASN.
A VPN connection can be established between each customer gateway and a shared virtual private gateway.
Every VPN connection must advertise its own BGP routes. This is accomplished through the use of network statements in the VPN configuration files for the VPN connection.
Frequently Asked Questions (FAQs)
Q1: What defines billable VPN connection hours?
Ans: VPN connection hours are charged for any time your VPN connections are “available.” The AWS Management Console, CLI, or API can be used to determine the status of a VPN connection. If you no longer want to use your VPN connection, simply disconnect to avoid being charged for additional VPN connection hours.
Q2: What is a target network?
Ans: A target network is a network that you associate with the Client VPN endpoint to provide secure access to AWS resources as well as on-premises resources. The target network is currently a subnet in your Amazon VPC.
Q3: Is AWS site-to-site VPN encrypted?
Ans. Each Site-to-Site VPN connection is made up of two encrypted IPsec VPN tunnels that connect AWS and your network. Each tunnel’s traffic can be encrypted with AES128 or AES256 and exchanged using Diffie-Hellman groups for Perfect Forward Secrecy.
amazon-web-services
SetUpVPNConnection
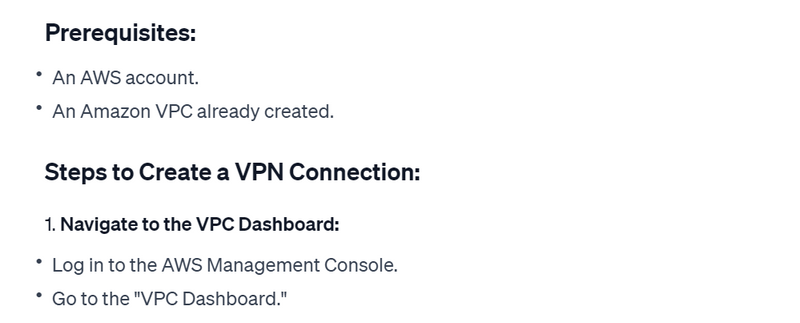
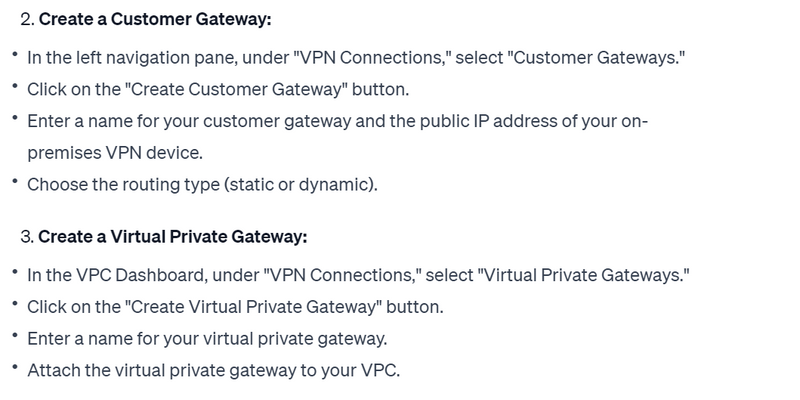
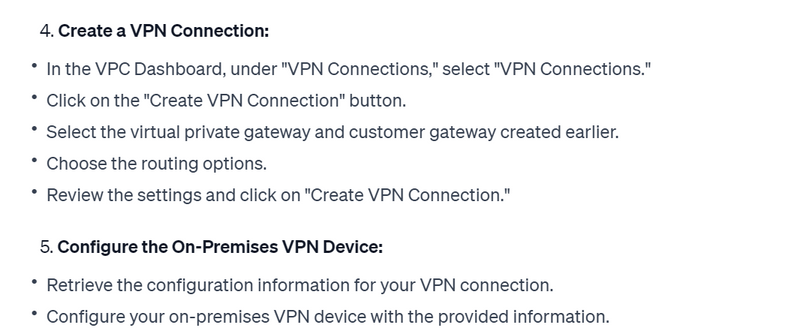
Example Configuration (for AWS-managed VPN):
Here's a simplified example of the configuration file you might download from AWS for an AWS-managed VPN connection:
# Example configuration for AWS-managed VPN (IPsec)
# Replace the placeholders with your actual values
# IKEv1 Configuration
Phase 1 Proposal
- Authentication Method: Pre-Shared Key
- Authentication Algorithm: SHA1
- Encryption Algorithm: AES-128
- Lifetime: 28800 seconds
# IKEv2 Configuration
Phase 1 Proposal
- Authentication Method: Pre-Shared Key
- Authentication Algorithm: SHA1
- Encryption Algorithm: AES-128
- Lifetime: 28800 seconds
# IPsec Configuration
Phase 2 Proposal
- Protocol: ESP
- Authentication Algorithm: SHA1
- Encryption Algorithm: AES-128
- Lifetime: 3600 seconds
# Pre-Shared Key (PSK)
Pre-Shared Key: YourSecretKey
# Virtual Private Gateway
Virtual Private Gateway IP: 203.0.113.1
# Customer Gateway
Customer Gateway IP: 198.51.100.1
Replace the placeholder values such as YourSecretKey, 203.0.113.1, and 198.51.100.1 with the actual values provided by AWS.
This is a simplified example, and the actual configuration may vary based on your specific requirements and the VPN device you are using on-premises. Always refer to AWS documentation and your VPN device documentation for accurate and up-to-date configuration details.

Top comments (0)