Allows access to the specific DynamoDB attributes
Allows access to the specific DynamoDB table
Allows access to read, write, update, and delete access on a DynamoDB table
Allows access to the specific DynamoDB attributes
how you might create an identity-based policy that allows access to the specific DynamoDB attributes. This policy grants the permissions necessary to complete this action programmatically from the AWS API or AWS CLI. To use this policy, replace the italicized placeholder text in the example policy with your own information. Then, follow the directions in create a policy or edit a policy.
The dynamodb:Select requirement prevents the API action from returning any attributes that aren't allowed, such as from an index projection. To learn more about DynamoDB condition keys, see Specifying Conditions: Using Condition Keys in the Amazon DynamoDB Developer Guide. To learn about using multiple conditions or multiple condition keys within the Condition block of an IAM policy, see Multiple values in a condition.
{
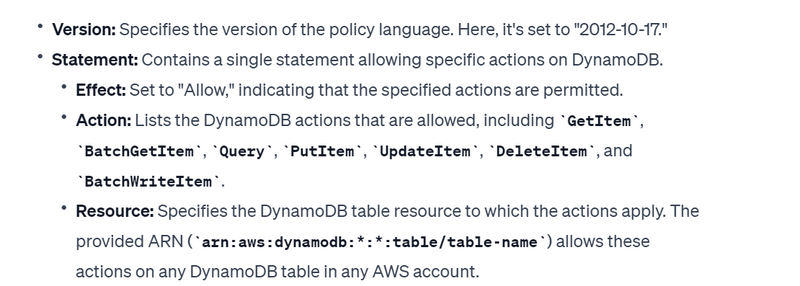
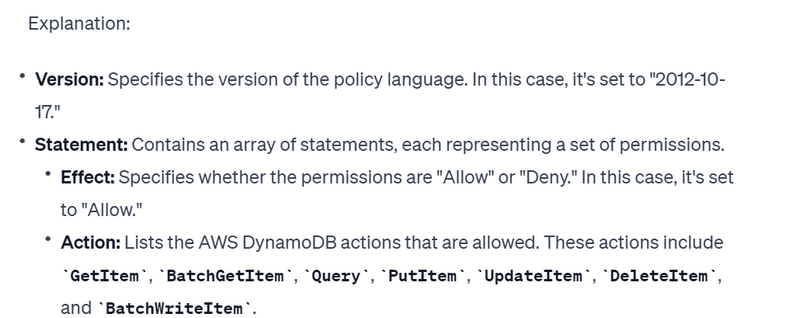
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"dynamodb:GetItem",
"dynamodb:BatchGetItem",
"dynamodb:Query",
"dynamodb:PutItem",
"dynamodb:UpdateItem",
"dynamodb:DeleteItem",
"dynamodb:BatchWriteItem"
],
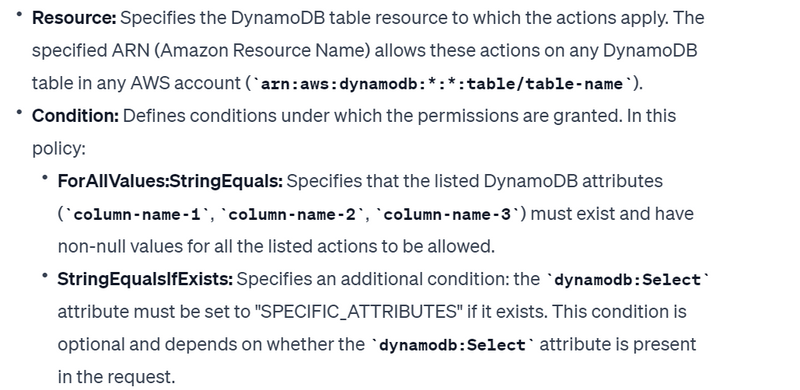
"Resource": ["arn:aws:dynamodb:*:*:table/table-name"],
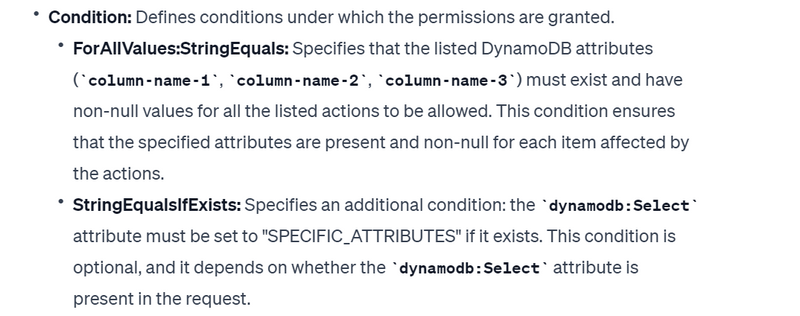
"Condition": {
"ForAllValues:StringEquals": {
"dynamodb:Attributes": [
"column-name-1",
"column-name-2",
"column-name-3"
]
},
"StringEqualsIfExists": {"dynamodb:Select": "SPECIFIC_ATTRIBUTES"}
}
}
]
}
Example:
Suppose you have a DynamoDB table named "example-table" with items having attributes named "column-name-1," "column-name-2," and "column-name-3." This policy allows a user to perform the specified DynamoDB actions (GetItem, BatchGetItem, etc.) on any DynamoDB table in any AWS account, but only if all specified attributes exist and have non-null values for each item. Additionally, if the user includes the dynamodb:Select attribute in the request, it must be set to "SPECIFIC_ATTRIBUTES" to satisfy the conditions of the policy.
Allows access to the specific DynamoDB table
This example shows how you might create an identity-based policy that allows full access to the MyTable DynamoDB table. This policy grants the permissions necessary to complete this action programmatically from the AWS API or AWS CLI. To use this policy, replace the italicized placeholder text in the example policy with your own information. Then, follow the directions in create a policy or edit a policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "ListAndDescribe",
"Effect": "Allow",
"Action": [
"dynamodb:List*",
"dynamodb:DescribeReservedCapacity*",
"dynamodb:DescribeLimits",
"dynamodb:DescribeTimeToLive"
],
"Resource": "*"
},
{
"Sid": "SpecificTable",
"Effect": "Allow",
"Action": [
"dynamodb:BatchGet*",
"dynamodb:DescribeStream",
"dynamodb:DescribeTable",
"dynamodb:Get*",
"dynamodb:Query",
"dynamodb:Scan",
"dynamodb:BatchWrite*",
"dynamodb:CreateTable",
"dynamodb:Delete*",
"dynamodb:Update*",
"dynamodb:PutItem"
],
"Resource": "arn:aws:dynamodb:*:*:table/MyTable"
}
]
}
The provided JSON represents an AWS Identity and Access Management (IAM) policy statement for working with Amazon DynamoDB. This policy grants permissions for two different scenarios:
List and Describe Operations:
Effect: Allow
Actions: This allows the specified actions on DynamoDB resources, such as listing tables, describing reserved capacity, describing limits, and describing time to live.
Resources: The wildcard () in the "Resource" field means that these actions are allowed on any DynamoDB resource.
**Operations on a Specific Table (MyTable)*:
Effect: Allow
Actions: This allows a more specific set of actions on a particular DynamoDB table named "MyTable". Actions include reading (Get, Query, Scan), writing (BatchWrite, PutItem), updating (Update), and deleting (Delete) items in the specified table. It also allows actions related to table management, such as creating (CreateTable) and describing (DescribeTable) the table.
Resources: The "Resource" field specifies the Amazon Resource Name (ARN) for the "MyTable" table. The wildcard (*) after "table" indicates that the permissions apply to any table with the name "MyTable" across all AWS regions.
Here's an example to illustrate how this policy works:
With the first statement, a user/role with this policy can list all DynamoDB tables, describe their reserved capacities, describe table limits, and get information about time to live settings for any DynamoDB resource.
With the second statement, the user/role can perform various actions (Get, Query, Scan, BatchWrite, CreateTable, etc.) on the specific DynamoDB table named "MyTable." This is a more fine-grained permission that allows specific operations on a particular resource.
Please note that in a real-world scenario, you would attach this policy to an IAM user, group, or role in AWS to grant the specified permissions. Also, the actual table name and specific actions might vary based on your use case.
Allows access to read, write, update, and delete access on a DynamoDB table
you need to allow your application to create, read, update, and delete data in Amazon DynamoDB tables, indexes, and streams. Substitute the AWS Region name, your account ID, and the table name or wildcard character (*) where appropriate.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "DynamoDBIndexAndStreamAccess",
"Effect": "Allow",
"Action": [
"dynamodb:GetShardIterator",
"dynamodb:Scan",
"dynamodb:Query",
"dynamodb:DescribeStream",
"dynamodb:GetRecords",
"dynamodb:ListStreams"
],
"Resource": [
"arn:aws:dynamodb:us-west-2:123456789012:table/Books/index/*",
"arn:aws:dynamodb:us-west-2:123456789012:table/Books/stream/*"
]
},
{
"Sid": "DynamoDBTableAccess",
"Effect": "Allow",
"Action": [
"dynamodb:BatchGetItem",
"dynamodb:BatchWriteItem",
"dynamodb:ConditionCheckItem",
"dynamodb:PutItem",
"dynamodb:DescribeTable",
"dynamodb:DeleteItem",
"dynamodb:GetItem",
"dynamodb:Scan",
"dynamodb:Query",
"dynamodb:UpdateItem"
],
"Resource": "arn:aws:dynamodb:us-west-2:123456789012:table/Books"
},
{
"Sid": "DynamoDBDescribeLimitsAccess",
"Effect": "Allow",
"Action": "dynamodb:DescribeLimits",
"Resource": [
"arn:aws:dynamodb:us-west-2:123456789012:table/Books",
"arn:aws:dynamodb:us-west-2:123456789012:table/Books/index/*"
]
}
]
}
To expand this policy to cover all DynamoDB tables in all AWS Regions for this account, use a wildcard (*) for the Region and table name. For example:
"Resource":[
"arn:aws:dynamodb:*:123456789012:table/*",
"arn:aws:dynamodb:*:123456789012:table/*/index/*"
]
Example:
Let's say you have a DynamoDB table named "example-table," and you want a user to be able to perform the specified actions (GetItem, BatchGetItem, etc.) on that table only if the specified attributes (column-name-1, column-name-2, column-name-3) exist and have non-null values. Additionally, if the user includes the dynamodb:Select attribute in the request, it must be set to "SPECIFIC_ATTRIBUTES." This policy ensures that the user can only access specific attributes and enforces conditions on both the presence of attributes and the value of the dynamodb:Select attribute.
dynamodb_attributes
dynamodb_specific-table
iam-policy-example-data-crud

Top comments (0)