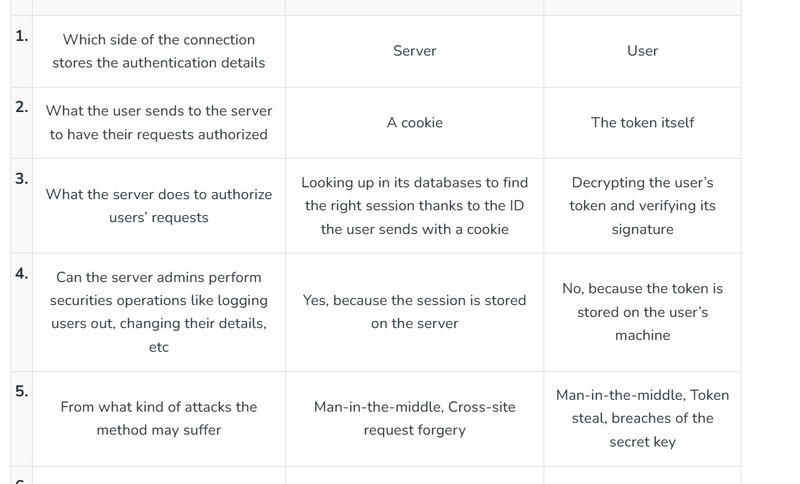
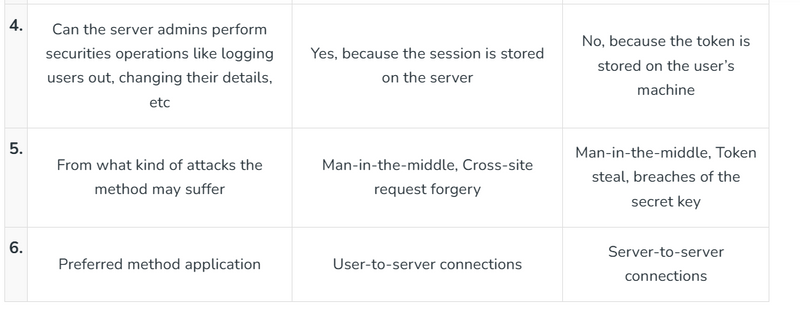
Difference between token and session
why session is called statefull and token are stateless
what are the different type of token and their role
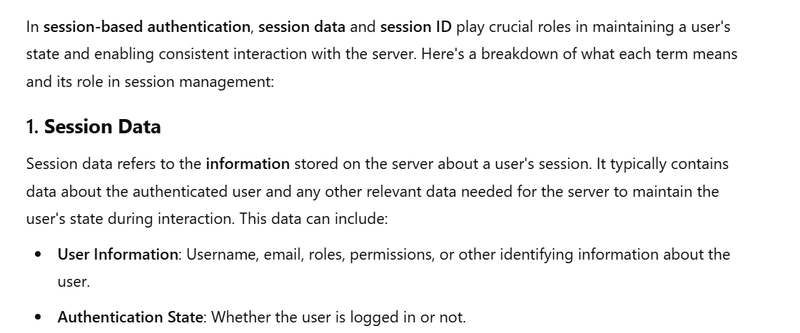
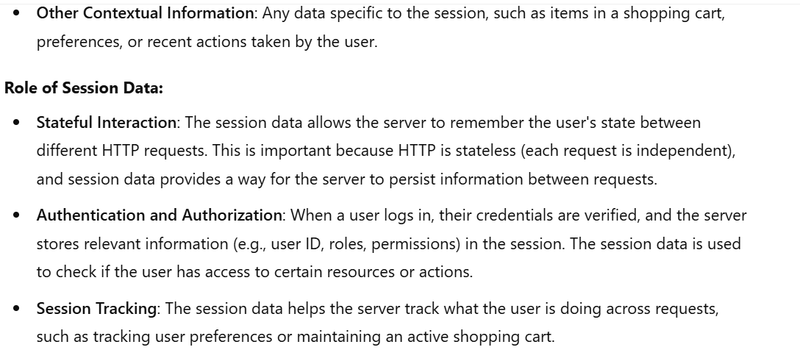
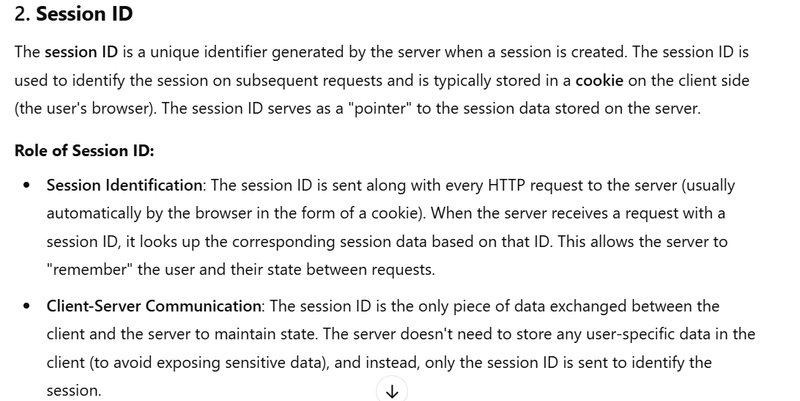
what is the role of session data and session id in session
where Token based authentication is used
Authentication can be managed using tokens (usually JWT - JSON Web Tokens) and sessions. Both methods are used to verify user identity and authorize access to certain resources, but they differ in their implementation and storage. Let me explain both methods in detail.
Session-Based Authentication
Session-based authentication uses a session identifier (usually stored on the server) to maintain a user's login state.
How It Works:
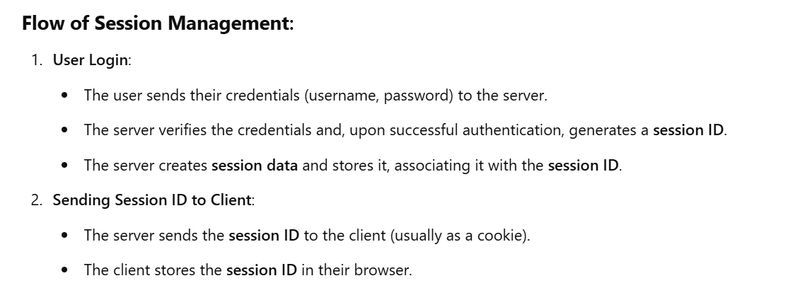
Login Request: The user logs in with their credentials (e.g., username and password).
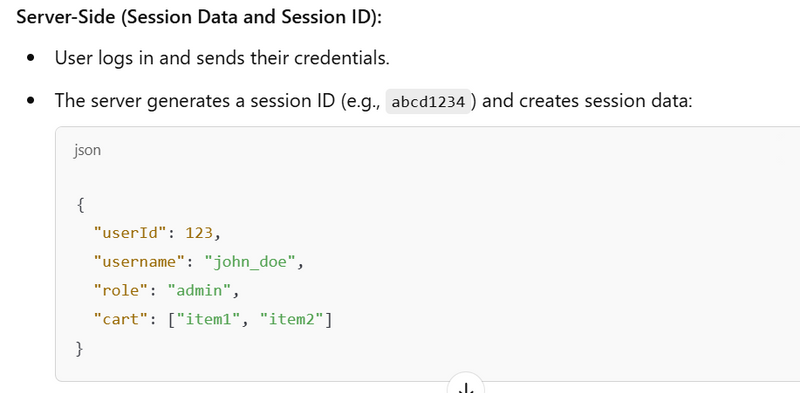
Session Creation: On the server side, the application creates a session for the user, storing the session ID in the server's memory or a database.
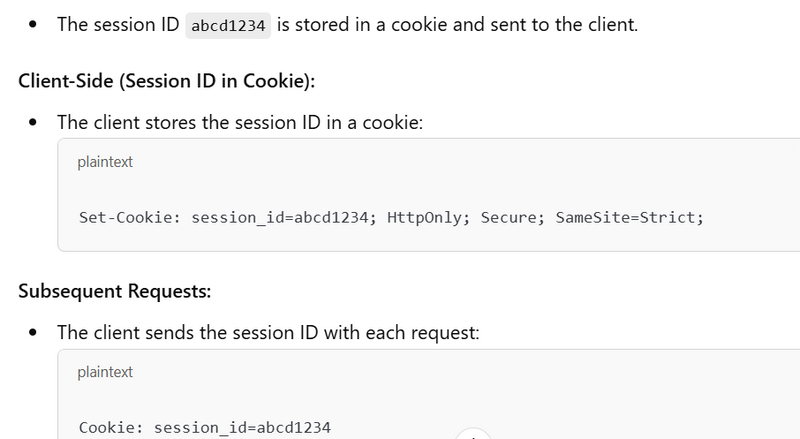
Session ID Storage: The server sends the session ID back to the client in the form of a cookie.
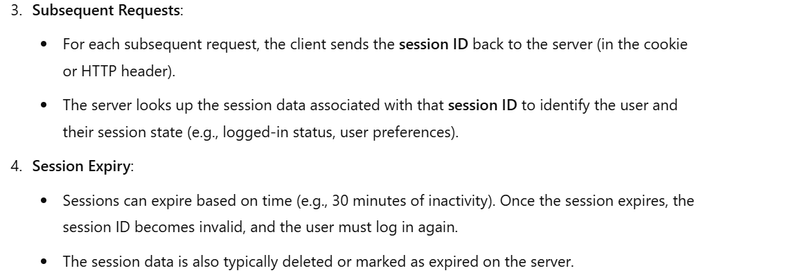
Subsequent Requests: For subsequent requests, the client automatically sends the session ID (in the cookie) to the server. The server then validates the session ID and checks if the user is authenticated.
Session Expiry: Sessions have an expiration time, after which the session will be invalid, and the user will need to log in again.
Advantages:
Server-side storage: Server manages the authentication state, making it more secure since the sensitive information is not exposed.
Automatic session management: Sessions are automatically handled by the server and client, simplifying state management.
Disadvantages:
Scalability: As the number of users grows, session management on the server can become a bottleneck.
Cross-domain issues: Cookies are often restricted to a single domain, which may make them harder to use across multiple domains.
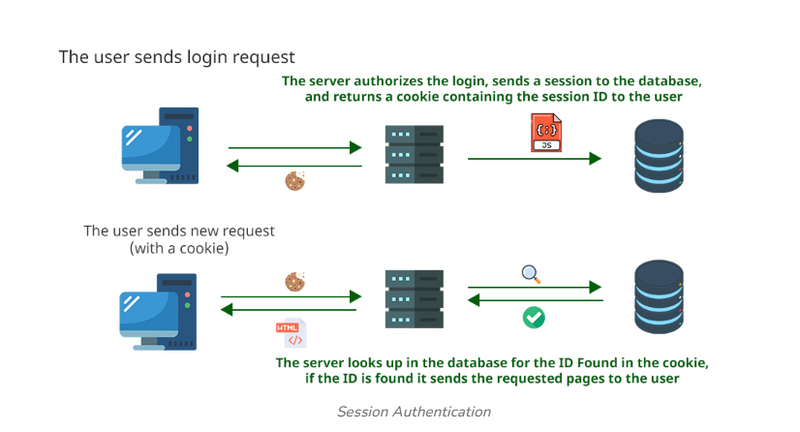
Session Authentication
A session is a small file, most likely in JSON format, that stores information about the user, such as a unique ID, time of login and expirations, and so on. It is generated and stored on the server so that the server can keep track of the user requests. The user receives some of these details, especially the ID, as cookies that will be sent with every new request, so that the server can recognize the ID and authorize the user’s requests.
Working
The user sends a login request to the server.
The server authenticates the login request, sends a session to the database, and returns a cookie containing the session ID to the user.
Now, the user sends new requests (with a cookie).
The server checks in the database for the ID found in the cookie, if the ID is found it sends the requested pages to the user.
Sessions
Sessions are a way to store user data on the server-side. Here's how sessions work:
-
Session Creation: When a user logs in, the server creates a session and stores the user's data in it. -
Session ID: The server sends a session ID to the client, which is stored in a cookie. -
Session Verification: The client sends the session ID with every subsequent request to the server. -
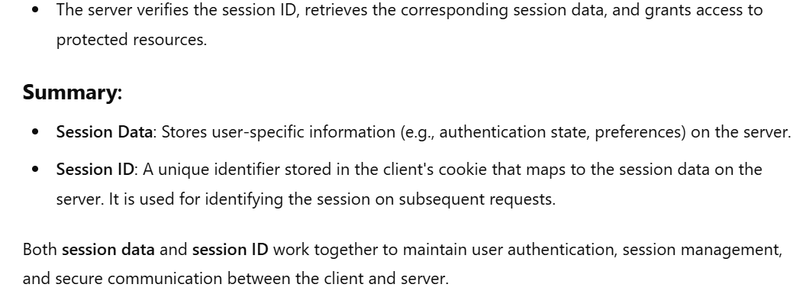
Session Validation: The server verifies the session ID and checks its validity. -
Access Granting: If the session ID is valid, the server grants access to the protected resource.
Token-Based Authentication (JWT)
Token-based authentication is stateless, using a token (usually JWT) that contains the user's identity and possibly other data. JWTs are typically used in REST APIs or single-page applications (SPAs).
How It Works:
Login Request: The user logs in with their credentials (e.g., username and password).
Token Generation: The server verifies the credentials and generates a JWT, which contains user data (e.g., user ID, roles, and expiration date). This token is signed with a secret key.
Token Sent to Client: The server sends the JWT to the client, usually as part of the response body or HTTP headers.
Storing the Token: The client stores the token in local storage or session storage (for web applications) or in the device's storage (for mobile apps).
Subsequent Requests: On subsequent requests, the client includes the JWT in the Authorization header (e.g., Authorization: Bearer ).
Token Verification: The server verifies the JWT by checking its signature and expiration. If the token is valid, the user is authenticated.
Token Expiry: JWTs have an expiration time, after which they are no longer valid. A refresh token can be used to obtain a new JWT without requiring the user to log in again.
Advantages:
Stateless: No need to store session data on the server. The token contains all the necessary information.
Scalable: Token-based authentication scales better, as the server doesn't need to manage user sessions.
Cross-domain: Tokens can be used across multiple domains and platforms (e.g., mobile apps, SPAs, microservices).
Flexibility: Tokens can be used for single sign-on (SSO) and can contain custom claims (data).
Disadvantages:
Token Storage Security: If a token is exposed (e.g., in local storage), it can be stolen and misused.
Token Revocation: Revoking a token before its expiration is difficult. You would typically need to implement a token blacklist or use short expiration times with refresh tokens.
A token is an authorization file that cannot be tampered with. It is generated by the server using a secret key, sent to and stored by the user in their local storage. Like in the case of cookies, the user sends this token to the server with every new request, so that the server can verify its signature and authorize the requests.
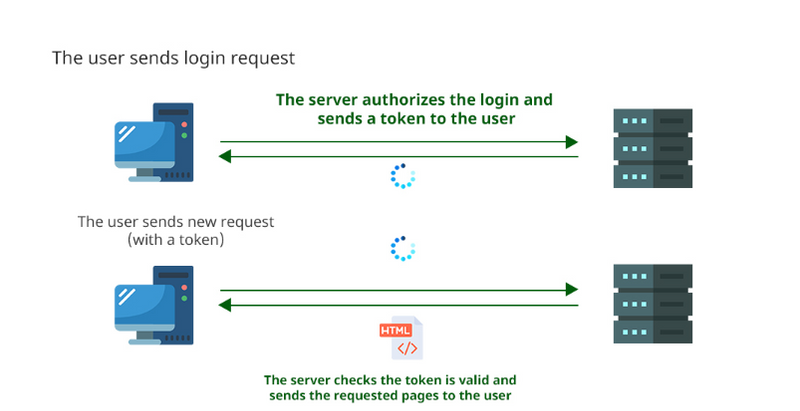
Working
The user sends a login request to the server.
The server authorizes the login and sends a token to the user.
Now, the user sends a new request(with a token).
The server checks the token is valid or not, if the token is valid it sends the requested pages to the user.
Tokens
Tokens are a type of authentication mechanism that allows users to access protected resources without providing their credentials every time. Here's how tokens work:
-
Token Generation: When a user logs in, the server generates a token and sends it to the client. -
Token Verification: The client sends the token with every subsequent request to the server. -
Token Validation: The server verifies the token and checks its validity. -
Access Granting: If the token is valid, the server grants access to the protected resource.
where Token based authentication is used
REST APIs
Single-Page Applications (SPAs)
Mobile Applications
Microservices Architectures
Cross-Domain Authentication
Single Sign-On (SSO)
Stateless Authentication in Distributed Systems
OAuth/OpenID Connect integration with third-party services
Token Refresh Mechanisms for long-lived sessions
what is the role of session data and session id in session
how-to-implement-secure-login-with-token-based-authentication-in-laravel-and-flutter
how-laravel-manages-user-login-and-session-id-storage


Top comments (0)