Apply full chain on ssl certificate
Apply full chain on ssl certificate using acme.sh
How to get acme.sh
Apply full chain on ssl certificate
Applying a full chain SSL certificate on a server typically involves combining the SSL certificate with the intermediate certificates and configuring them on the server. Here is a step-by-step guide with commands for popular server types:
- Obtain Required Files Make sure you have the following:
- Your domain certificate (e.g., your_domain.crt or your_domain.pem)
- Intermediate certificates provided by your CA (often a bundle file like ca_bundle.crt)
- Private key generated during the CSR creation (e.g., your_domain.key )
- Create a Full Chain File Combine your certificate and the intermediate certificate(s) into a single file:
cat your_domain.crt ca_bundle.crt > fullchain.pem
This file (fullchain.pem) will contain:
Your certificate (your_domain.crt)
Intermediate certificates (ca_bundle.crt)
-
Install Full Chain on Your Server
For Apache
Edit the SSL configuration file: The configuration file is typically located in /etc/apache2/sites-available/ or /etc/httpd/conf.d/. Open the relevant SSL config file (e.g., default-ssl.conf):
sudo nano /etc/apache2/sites-available/default-ssl.conf
Update the file with the certificate paths:
SSLCertificateFile /path/to/fullchain.pem
SSLCertificateKeyFile /path/to/your_domain.key
Enable the SSL module and site:
sudo a2enmod ssl
sudo a2ensite default-ssl
Restart Apache:
sudo systemctl restart apache2
For NGINX
Edit the SSL configuration: The configuration file is typically located in /etc/nginx/sites-available/ or /etc/nginx/conf.d/. Open the relevant site config file:
sudo nano /etc/nginx/sites-available/your_site
Update the file with the certificate paths:
server {
listen 443 ssl;
server_name your_domain.com;
ssl_certificate /path/to/fullchain.pem;
ssl_certificate_key /path/to/your_domain.key;
# Optional security settings
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers HIGH:!aNULL:!MD5;
}
Test the configuration:
sudo nginx -t
Restart NGINX:
sudo systemctl restart nginx
For Other Servers
The steps are similar: locate the configuration file for your server, specify the paths for the fullchain.pem and private key, and restart the server.
- Verify SSL Installation After restarting the server, verify the installation:
Use an online SSL checker:
SSL Labs
SSL Shopper
Verify the certificate chain:
openssl s_client -connect your_domain.com:443 -showcerts
Look for the certificate chain in the output to ensure it includes your certificate and the intermediates.
Troubleshooting
If you see "certificate not trusted" errors, ensure the intermediate certificates are included in the full chain file.
For self-signed certificates, make sure the root CA is added to the client's trusted certificate store.
Apply full chain on ssl certificate using acme.sh
shows steps to generate and install an SSL certificate using the acme.sh script, which is an ACME client for Let's Encrypt and other certificate authorities.
Setting Environment Variables
export GD_Key="XXXXXXXXXXXXXX"
export GD_Secret="XXXXXXXXXXXXXX"
The command will first verify the GoDaddy API key and secret you exported:
GD_Key and GD_Secret are the API credentials for GoDaddy DNS.
These keys allow acme.sh to verify domain ownership using the DNS challenge method.
If there’s an issue with the API key/secret, an error will appear, such as:
Error: Invalid GD_Key or GD_Secret for DNS validation.
Running acme.sh to Issue SSL Certificate
./acme.sh --issue --dns dns_gd -d motoshare.in -d www.motoshare.in --force
--issue: Generates the SSL certificate.
--dns dns_gd: Uses GoDaddy DNS for domain validation.
-d motoshare.in -d www.motoshare.in: Issues the certificate for both the root domain (motoshare.in) and the subdomain (www.motoshare.in).
--force: Forces certificate generation, even if one already exists.
Viewing SSL Configuration File
more /opt/lampp/etc/extra/httpd-ssl.conf
Displays the Apache SSL configuration file to verify paths for certificates and keys.
Copying SSL Certificates and Key
The commands copy the newly issued certificate files to the appropriate directory used by Apache.
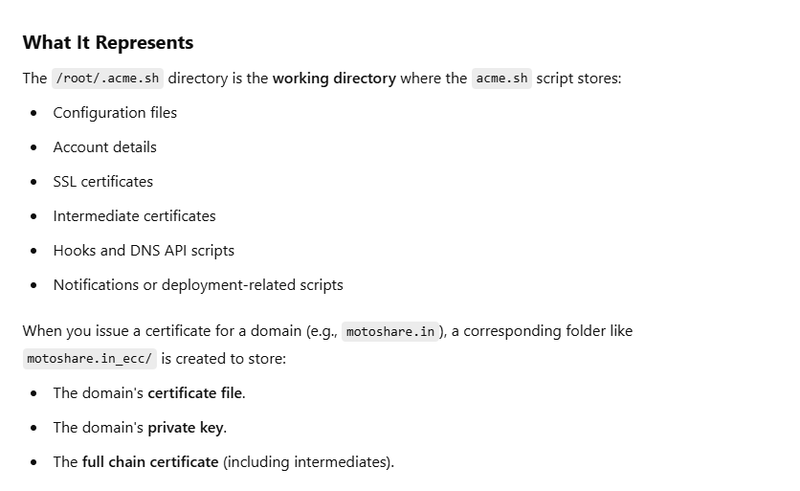
cp /root/.acme.sh/motoshare.in_ecc/motoshare.in.cer /opt/lampp/etc/certs/acme
cp /root/.acme.sh/motoshare.in_ecc/motoshare.in.key /opt/lampp/etc/certs/acme
cp /root/.acme.sh/motoshare.in_ecc/fullchain.cer /opt/lampp/etc/certs/acme
motoshare.in.cer: The certificate for motoshare.in.
motoshare.in.key: The private key for the certificate
.
fullchain.cer: The full chain file, which includes the domain certificate and intermediate certificates.
Editing SSL Configuration File
vi /opt/lampp/etc/extra/httpd-ssl.conf
Opens the Apache SSL configuration file for editing.
Verifying SSL Configuration
more /opt/lampp/etc/extra/httpd-ssl.conf
Checks the updated configuration after copying the certificates.
What This Does
Uses the acme.sh script to automate SSL certificate issuance via GoDaddy DNS verification.
Installs the certificate on the Apache server (LAMPP stack).
Ensures Apache references the correct certificate and key files
Explanation
Step 1: Checking the ACME Configuration The command will first verify the GoDaddy API key and secret you exported:
export GD_Key="XXXXXXXXXXXXXX"
export GD_Secret="XXXXXXXXXXXXXX"
If there’s an issue with the API key/secret, an error will appear, such as:
Error: Invalid GD_Key or GD_Secret for DNS validation.
Step 2: DNS Challenge Setup
acme.sh will set up a DNS challenge for motoshare.in and www.motoshare.in using the GoDaddy DNS API.
You will see messages like:
Creating domain key
Registering account
Getting domain challenge for motoshare.in
Getting domain challenge for www.motoshare.in
Adding DNS record: _acme-challenge.motoshare.in with value XXXX
Adding DNS record: _acme-challenge.www.motoshare.in with value XXXX
Waiting for DNS record to propagate
This step adds temporary DNS TXT records (used to validate domain ownership). It pauses for a while to allow DNS propagation.
Step 3: Certificate Issuance Once DNS validation is successful, the script generates the SSL certificate:
Verify finished, domain is verified.
Creating full chain certificate
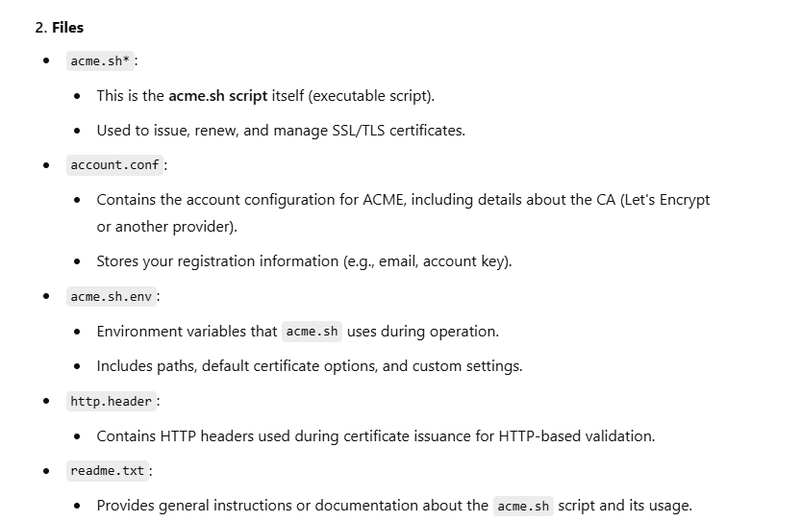
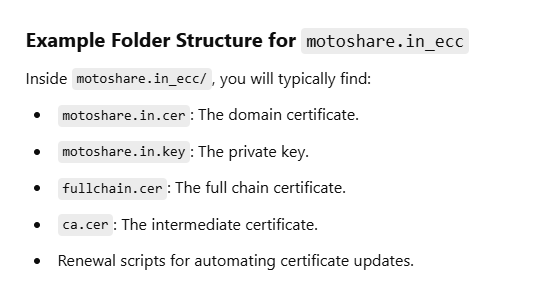
Certificate is saved: /root/.acme.sh/motoshare.in_ecc/motoshare.in.cer
Key is saved: /root/.acme.sh/motoshare.in_ecc/motoshare.in.key
Full chain is saved: /root/.acme.sh/motoshare.in_ecc/fullchain.cer
Key Outputs:
Certificate File: /root/.acme.sh/motoshare.in_ecc/motoshare.in.cer
Private Key: /root/.acme.sh/motoshare.in_ecc/motoshare.in.key
Full Chain Certificate: /root/.acme.sh/motoshare.in_ecc/fullchain.cer
Step 4: Summary At the end, acme.sh provides a summary of the process:
Certificate issued successfully:
- Domain: motoshare.in
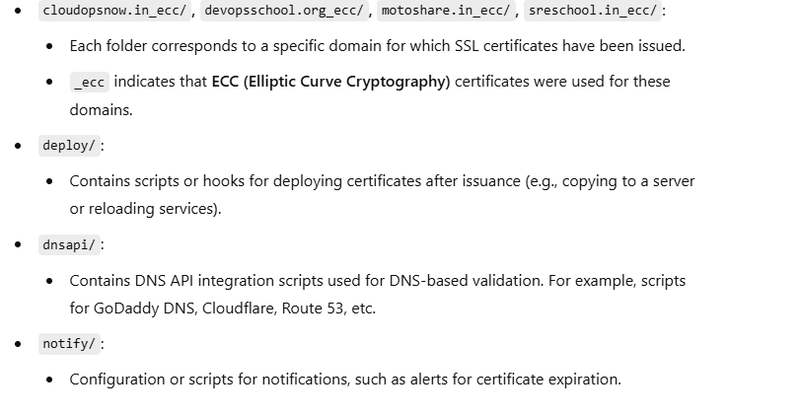
- Certificate Location: /root/.acme.sh/motoshare.in_ecc/
- Your cert is in /root/.acme.sh/motoshare.in_ecc/motoshare.in.cer
- Your cert key is in /root/.acme.sh/motoshare.in_ecc/motoshare.in.key
- The intermediate CA cert is in /root/.acme.sh/motoshare.in_ecc/ca.cer
- The full chain cert is in /root/.acme.sh/motoshare.in_ecc/fullchain.cer
How to get acme.sh
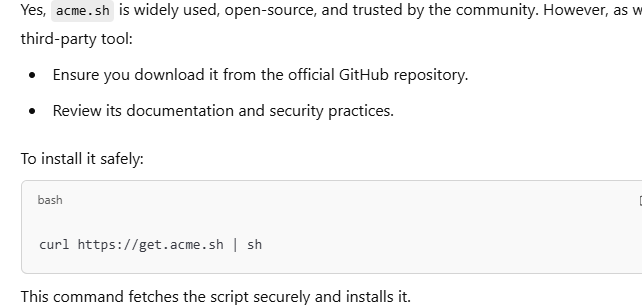
To get and install acme.sh, you can follow these simple steps. The installation process ensures the script is set up correctly and securely on your system.
Step 1: Download and Install acme.sh
Run the following command to download and install acme.sh from its official GitHub repository:
curl https://get.acme.sh | sh
Explanation:
curl https://get.acme.sh fetches the installation script.
| sh pipes the script to the shell for execution.
Step 2: Add acme.sh to PATH
Once the installation completes, the script will suggest adding the acme.sh binary to your PATH variable.
Run the following command to add it to your PATH for easier use:
export PATH="~/.acme.sh:$PATH"
To make this permanent, add it to your shell's startup file (e.g., .bashrc or .zshrc):
echo 'export PATH="~/.acme.sh:$PATH"' >> ~/.bashrc
source ~/.bashrc
Step 3: Verify Installation
To confirm that acme.sh was installed successfully, run:
acme.sh --version
Output:
v3.x.x (version number may vary)
Step 4: Using acme.sh
After installation, you can start issuing certificates. Example for a DNS-based Let's Encrypt certificate:
acme.sh --issue --dns dns_gd -d yourdomain.com -d www.yourdomain.com
Installing acme.sh Manually
If you prefer to clone the repository manually, use these steps:
Clone the repository:
git clone https://github.com/acmesh-official/acme.sh.git
cd acme.sh
Install the script:
./acme.sh --install
Add it to your PATH:
export PATH="~/.acme.sh:$PATH"
Default Installation Location
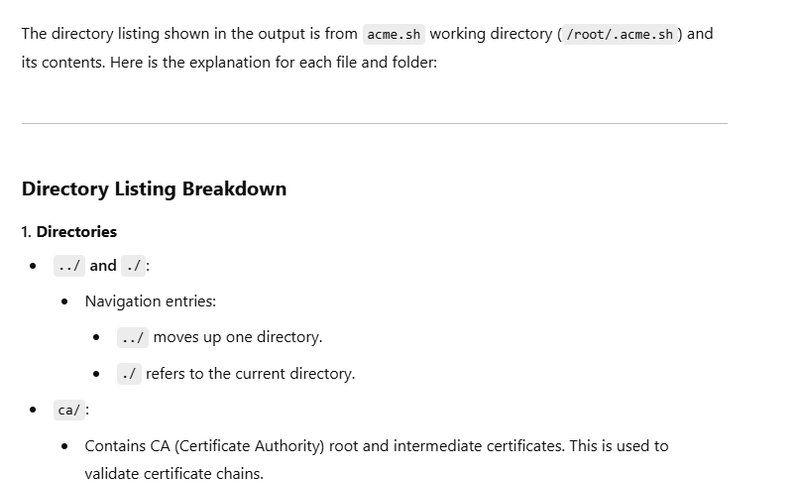
Once installed, acme.sh resides in:
~/.acme.sh/
This directory contains:
The acme.sh script.
Configuration files.
Issued SSL certificates.
Updating acme.sh
To update acme.sh to the latest version:
acme.sh --upgrade
Summary
- Run curl https://get.acme.sh | sh to install acme.sh.
- Add it to your PATH for easy access.
- Use acme.sh --version to confirm the installation.
- With this setup, you can begin issuing and managing SSL certificates using acme.sh .

Top comments (0)