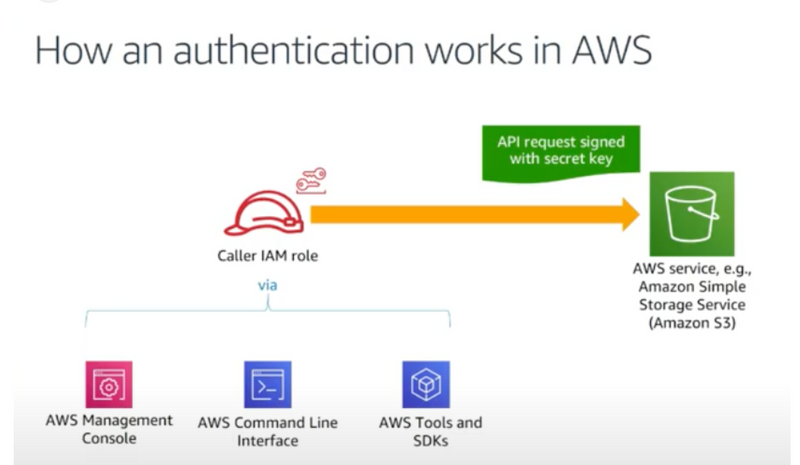
An IAM role is an IAM identity that you can create in your account that has specific permissions. An IAM role is similar to an IAM user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it. Also, a role does not have standard long-term credentials such as a password or access keys associated with it. Instead, when you assume a role, it provides you with temporary security credentials for your role session.
You can use roles to delegate access to users, applications, or services that don't normally have access to your AWS resources. For example, you might want to grant users in your AWS account access to resources they don't usually have, or grant users in one AWS account access to resources in another account. Or you might want to allow a mobile app to use AWS resources, but not want to embed AWS keys within the app (where they can be difficult to update and where users can potentially extract them). Sometimes you want to give AWS access to users who already have identities defined outside of AWS, such as in your corporate directory. Or, you might want to grant access to your account to third parties so that they can perform an audit on your resources.
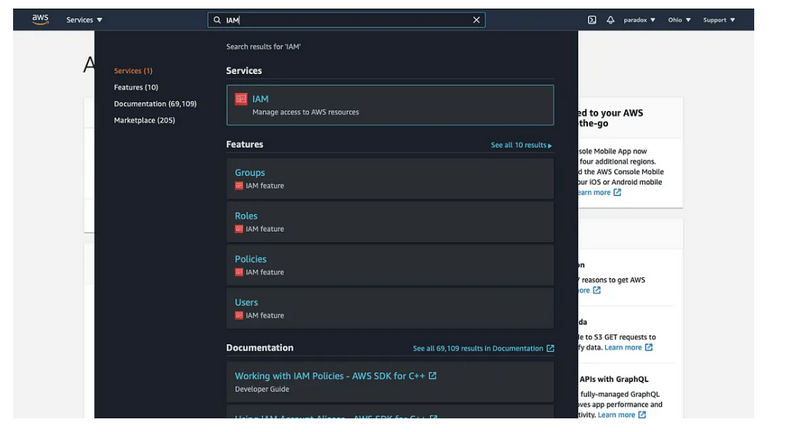
Step 1: Inside the search bar type IAM and click on it.
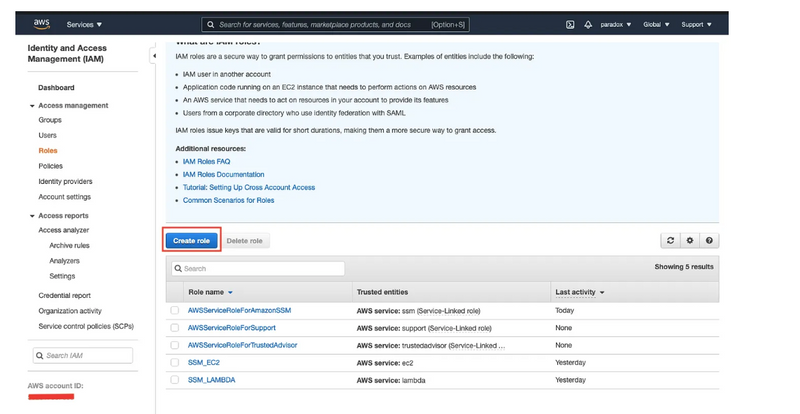
Step 2: Click in Roles under Access management.
Step 3: Click on Create Role
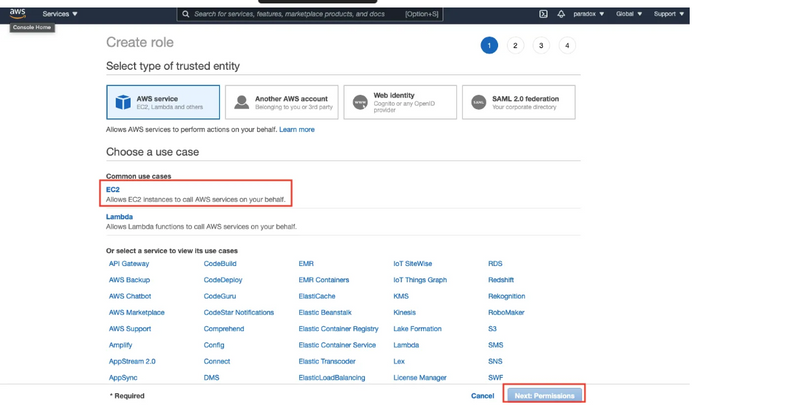
Step 4: Now, we can select any use case. You can select any service I am selecting EC2.
Selecting services means this service which in my case is EC2 will able to access AWS other services like accessing of S3 bucket in simple terms you gave the particular service rights to use other services.
After selecting your service click on Next: Permissions button. After selecting your service the button will be highlighted.
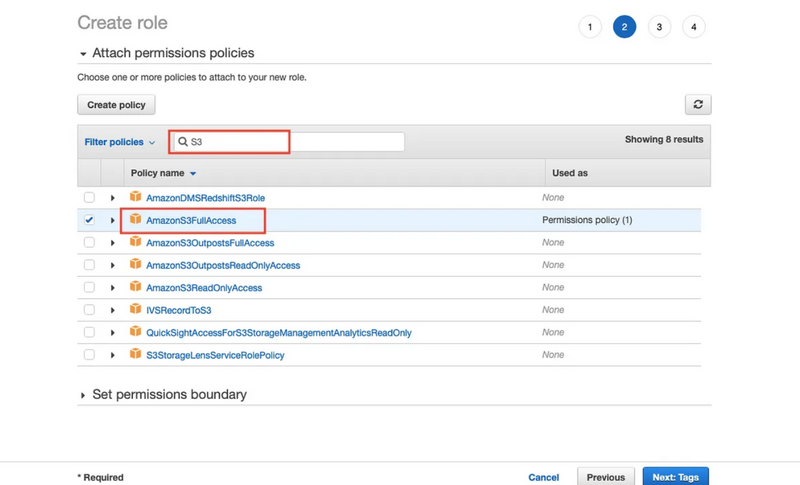
Step 5: Now we will search for the policy which we want to use in my case I want EC2 services to access S3 bucket.
A policy is an object in AWS that, when associated with an entity or resource, defines their permissions. AWS evaluates these policies when a principal, such as a user, makes a request. Permissions in the policies determine whether the request is allowed or denied. Most policies are stored in AWS as JSON documents. — From AWS Article
So, type the policy name which you want I want to access S3 bucket using my EC2 instance so I will type S3 and I will find AmazonS3FullAccess policy select it and click on Next: Tags button
You can add as many as policies you want on any particular service to know more about policies click
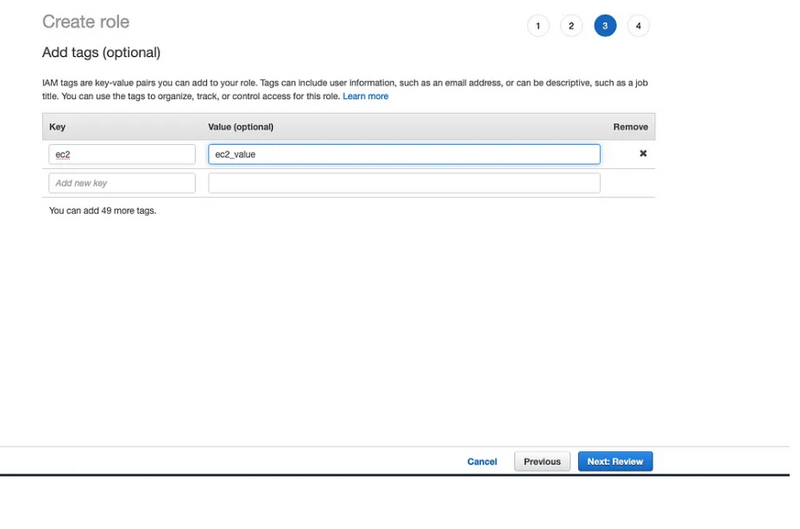
Step 6: After clicking in Next: Tags button you will be ask to add tags it is optional when you have many policies associated with different users and services it will help to organize policies.
Click on Next:Review button
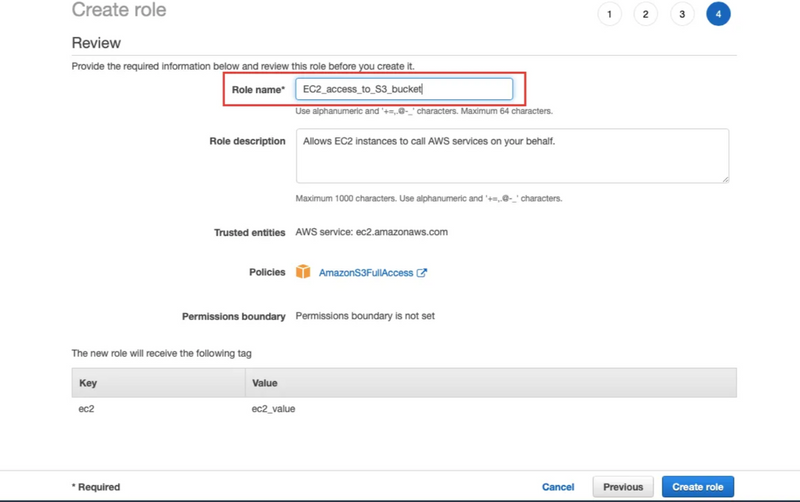
Step 7: Now, after doing all the above steps write the relevant role name of your policy. So, you will identify what’s this role for .Like in this role I am giving EC2 instances to access S3 bucket. So, i will name my role name according to these two services.
Now, click on Create role button.
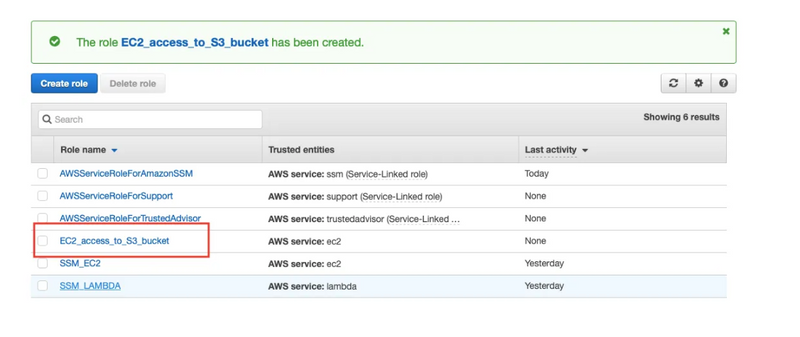
You will get the role has been created

Top comments (0)