Securing Linux Daemons with examples using linux commands
how to identify unnecessary daemons to secure linux server using linux Command
Reviewing the list of running daemons OR list all services:
display information for the specific service
To view the status of a specific service
display all servies that is not running in linux
list of all software package that is not running
list of all software package that is installed last 10 days and is not not running in linux
list of pakage that is installed in last 10 days
list of pakage that is installed in last 10 days using history
how to find particular software installed **
*how to find particular software running or not *
**identifying purpose of each daemons
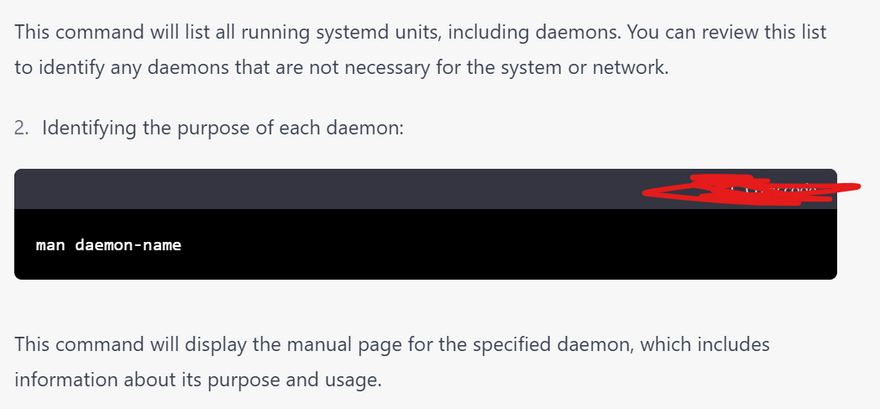
manual page for specified daemons
disabling unnecessary daemons
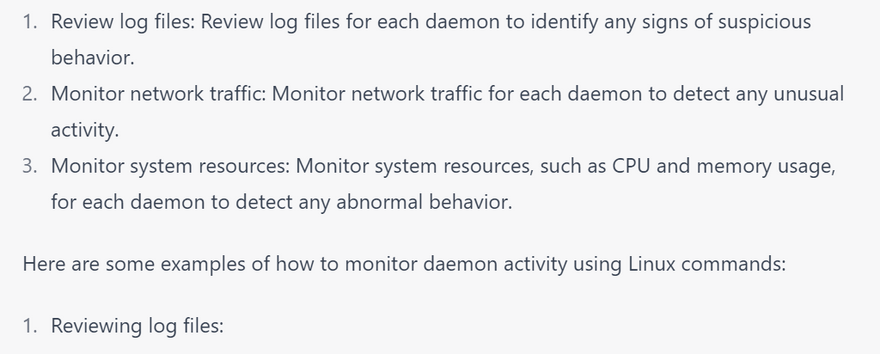
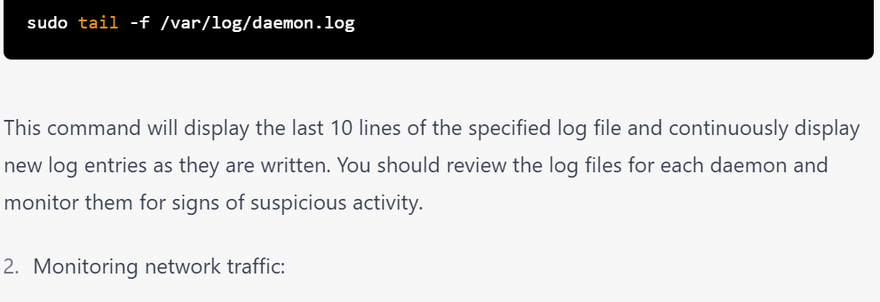
How to Monitor daemon activity
Review log file(tail)
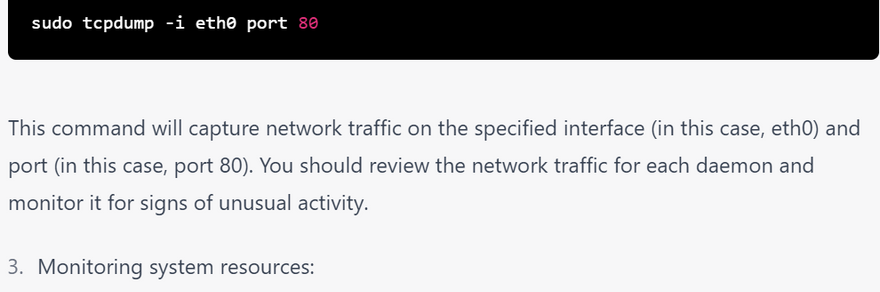
Monitor network traffic(tcpdump
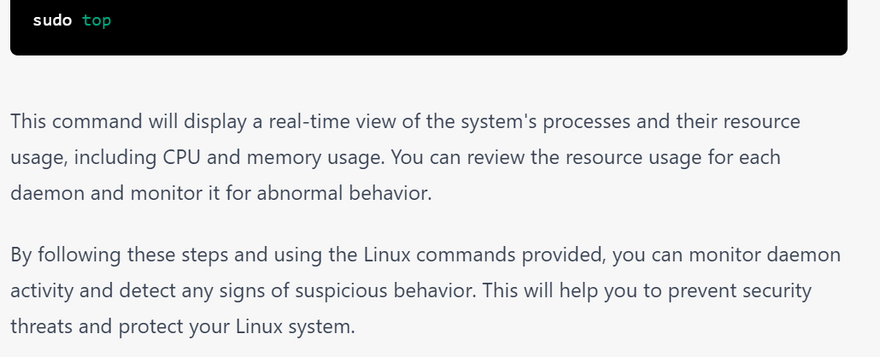
Monitor system resources(top)
how to use Security Patches to seure linux server
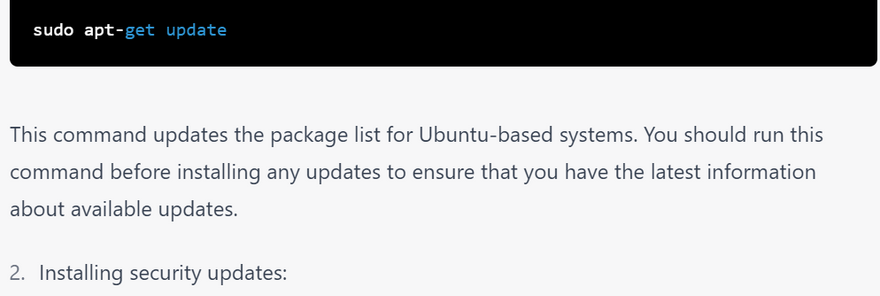
update package list
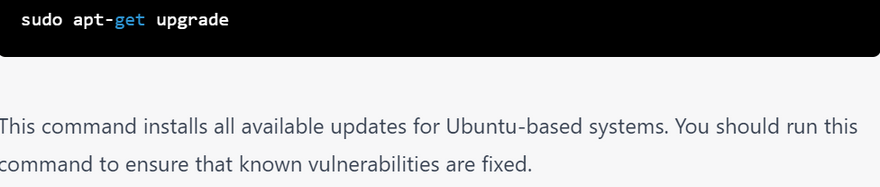
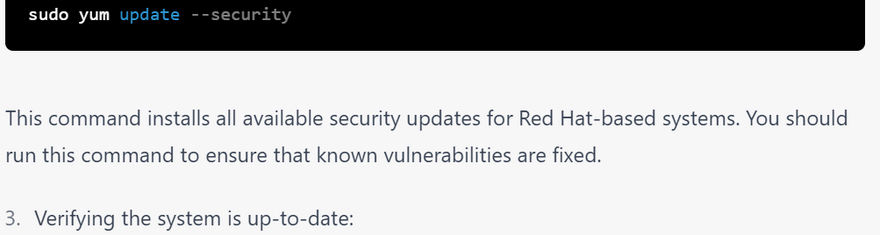
installing security update
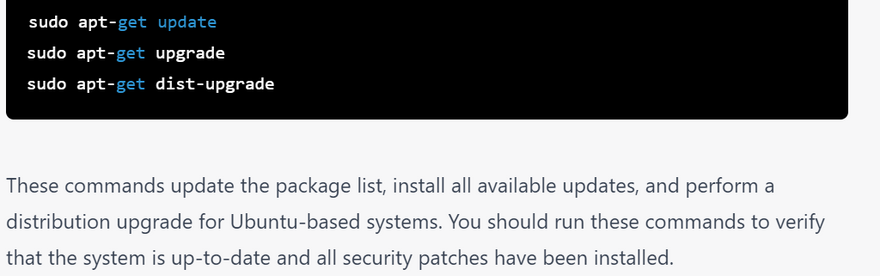
verify system upto date
Identifying unnecessary daemons is an important step in securing a Linux server. Daemons are background processes that run continuously and provide various services to the system or network. Here are some steps you can take to identify unnecessary daemons:
1.Review the list of running daemons: Review the list of running daemons on the server to identify any that are not necessary for the system or network.
2.Identify the purpose of each daemon: Identify the purpose of each daemon to determine if it is necessary for the system or network. This includes researching the daemon's function and reviewing documentation.
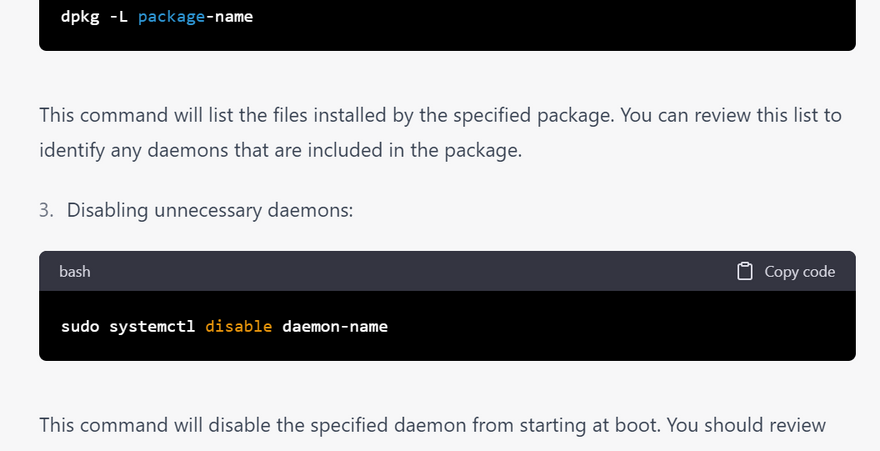
3.Disable unnecessary daemons: Disable any daemons that are not necessary for the system or network. This reduces the attack surface of the system and reduces the risk of vulnerabilities.
Here are some examples of how to identify unnecessary daemons using Linux commands:
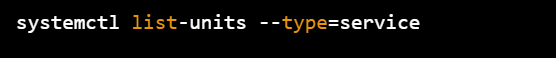
Reviewing the list of running daemons OR display a list all services
systemctl list-units --type=service
systemctl list-units --type=service | grep sshd
display information for the sshd service only.
To view the status of a specific service, use the following command:
systemctl status <service_name>
systemctl status sshd
*display all servies that is not running in linux *
systemctl list-units --type=service --state=inactive
service --status-all | grep -E "\[ + \]"
list of all software package that is not running
dpkg -l | grep ^ii | awk '{print $2}' | xargs -I{} sh -c 'systemctl is-active --quiet {} || echo {}'
rpm -qa | xargs -I{} sh -c 'systemctl is-active --quiet {} || echo {}'
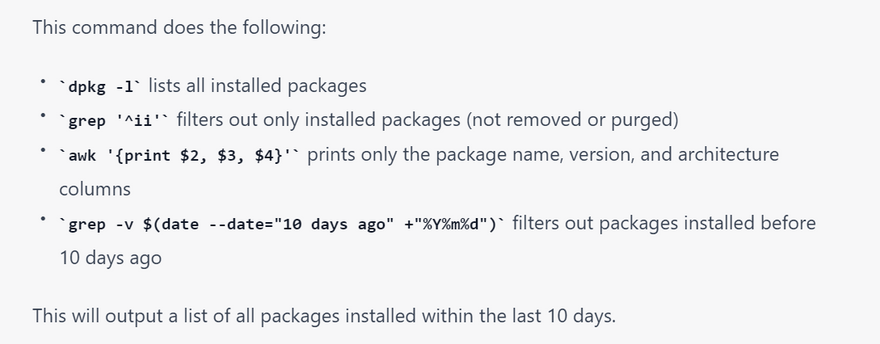
list of all software package that is installed last 10 days and is not not running in linux
dpkg -l | grep ^ii | awk '{print $2}' | xargs -I{} sh -c 'test $(find /var/lib/dpkg/info/{}.* -mtime -10 -print) && systemctl is-active --quiet {} || echo {}'
list of pakage that is installed in last 10 days
dpkg -l | grep '^ii' | awk '{print $2, $3, $4}' | grep -v $(date --date="10 days ago" +"%Y%m%d")
list of pakage that is installed in last 10 days
sudo grep "install " /var/log/dpkg.log | awk '$1 >= "'$(date --date="10 days ago" +%Y-%m-%d)'" {print $4}' | sort -u
This command searches the /var/log/dpkg.log file for lines containing the word "install", and then filters the lines to only include those that are from the last 10 days. Finally, it extracts the package names from those lines and removes duplicates.
Note that this command requires sudo privileges to access the dpkg.log file.
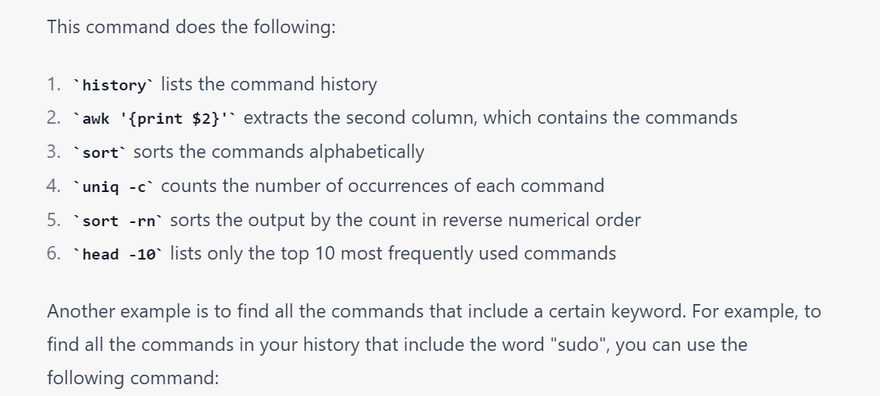
history | awk '{print $2}' | sort | uniq -c | sort -rn | head -10
history | grep sudo
history | grep install
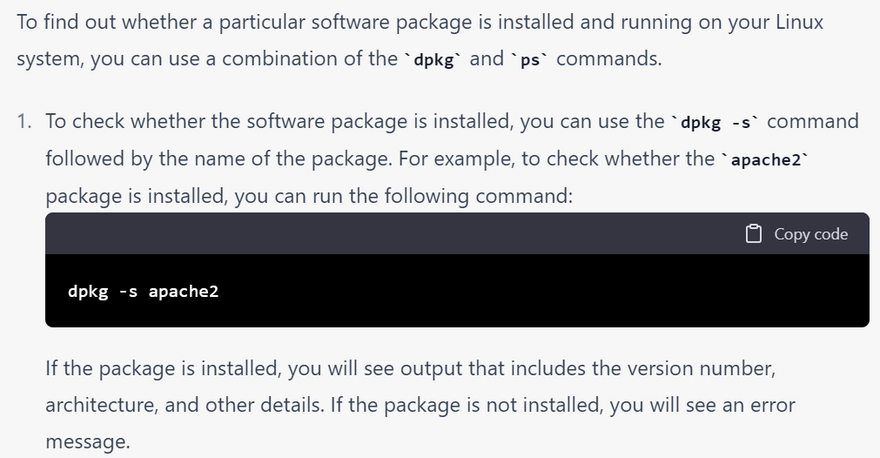
how to find particular software installed package running or not
dpkg -s apache2
To check whether the software package is running, you can use the ps command to list all currently running processes and search for the name of the software package. For example, to check whether the apache2 service is running, you can run the following
ps -ef | grep apache2
If the service is running, you will see output that includes information about the process, such as the process ID and the command that started the process. If the service is not running, you will not see any output.
Note that the exact name of the package and the corresponding service or process name may vary depending on the distribution and version of Linux you are using, as well as the particular software package you are looking for.
How to Monitor daemon activity
Monitoring daemon activity is an important part of securing a Linux system. Daemons are background processes that run continuously and provide various services to the system or network. By monitoring daemon activity, you can detect any signs of suspicious behavior and take action to prevent security threats. Here are some steps you can take to monitor daemon activity:
how to use Security Patches to seure linux server using linux Command
Keeping your Linux server up-to-date with security patches is an important step in securing your system. Security patches fix known vulnerabilities and improve the security of your system. Here are some steps you can take to use security patches to secure your Linux server:
These commands check for available updates, display information about available security updates, and install all available updates for Red Hat-based systems. You should run these commands to verify that the system is up-to-date and all security patches have been installed.
By following these steps and using the Linux commands provided, you can use security patches to secure your Linux server and reduce the risk of vulnerabilities.


Top comments (0)