Search for failed login attempts in an Apache web server
search for error messages related to a specific daemon in a log file
extract the timestamps and error codes from a log file for a specific daemon
count the number of error messages for a specific daemon in a log file
Reviewing log files of each daemon can be a useful way to identify any signs of suspicious behavior. Here are some general steps you can follow:
1.Locate the log files: The location of the log files depends on the operating system and the daemon being used. In general, log files are stored in a directory named "log" or "logs" within the daemon's installation directory. You can also use the command "ps aux | grep " to identify the process ID (PID) of the daemon and then check the logs in the system's log directory (e.g., /var/log/).
2.Analyze the log files: Once you have located the log files, you should analyze them to look for any suspicious activity. Some examples of suspicious activity to look for include:
Repeated failed login attempts
Unusual network activity
Changes in file permissions
Errors or warnings that suggest a security breach
Check for anomalies: Look for anomalies in the logs, such as log entries at unusual times, log entries from unusual IP addresses, or log entries that indicate an unusual user account activity.
3.Use grep and other command-line tools: Use grep and other command-line tools to search through the log files for specific keywords that may indicate suspicious activity. For example, you could use the following command to search for failed login attempts in an Apache web server log:
grep "authentication failure" /var/log/httpd/access_log
ls /opt/lampp/logs/access_log | grep "GET" /opt/lampp/logs/access_log
TO find path of access log
sudo locate access_log
sudo apt-get install mlocate
To search for a specific string in the access log file:
sudo cat /var/log/apache2/access_log | grep "search_string"
To count the number of times a specific string appears in the access log file:
sudo cat /var/log/apache2/access_log | grep -c "GET"
sudo more /opt/lampp/logs/access_log | grep -c "GET"
sudo ls /opt/lampp/logs/access_log | grep -c "GET"
To view the last 10 lines of the error log file:
sudo tail //opt/lampp/logs/error_log -n 10
Monitor the logs regularly: To detect suspicious activity as soon as possible, it's important to monitor the logs regularly. Consider setting up a system to alert you if any suspicious activity is detected.
In summary, reviewing log files for each daemon can help identify signs of suspicious behavior. To do so, you should locate the log files, analyze them for anomalies, search for specific keywords using command-line tools, and monitor the logs regularly.
In Linux, you can review log files for each daemon to identify any signs of suspicious behavior using pipe commands. Here are some examples:
Using the grep command:
The grep command can be used to search log files for specific patterns, such as error messages or suspicious behavior.
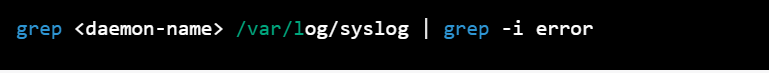
To search for error messages related to a specific daemon in a log file, you can use the following command:
grep <daemon-name> /var/log/syslog | grep -i error
Replace with the name of the daemon that you want to monitor. This command will search the /var/log/syslog file for lines that contain the specified daemon name, and then filter the output to only show lines that contain the word "error" (case-insensitive).
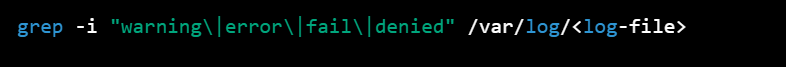
To search for suspicious behavior in a log file, you can use the following command:
grep -i "warning\|error\|fail\|denied" /var/log/<log-file>
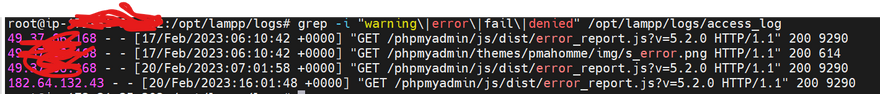
grep -i "warning\|error\|fail\|denied" /opt/lampp/logs/access_log
sudo more /opt/lampp/logs/access_log | grep -i "warning\|error\|fail\|denied"
sudo more /opt/lampp/logs/access_log | grep "warning\|error\|fail\|denied"
sudo cat /opt/lampp/logs/access_log | grep "warning\|error\|fail\|denied"
This command will search the specified log file for lines that contain any of the following keywords: "warning", "error", "fail", or "denied" (case-insensitive).
2.Using the awk command:
The awk command can be used to extract specific fields from log files, such as timestamps or error codes, and then filter or sort the output.
To extract the timestamps and error codes from a log file for a specific daemon, you can use the following command:
awk '/<daemon-name>/ { print $1, $2, $NF; }' /var/log/<log-file>
Replace and with the name of the daemon and the log file that you want to monitor, respectively. This command will search the log file for lines that contain the specified daemon name, and then print the first, second, and last fields (which should be the timestamp, hostname, and error code, respectively) of each matching line.
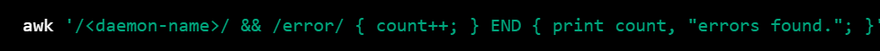
To count the number of error messages for a specific daemon in a log file, you can use the following command:
awk '/<daemon-name>/ && /error/ { count++; } END { print count, "errors found."; }' /var/log/<log-file>
Replace and with the name of the daemon and the log file that you want to monitor, respectively. This command will search the log file for lines that contain the specified daemon name and the word "error", and then count the number of matching lines and print the result.
In summary, you can use Linux pipe commands to review log files for each daemon to identify any signs of suspicious behavior, by piping the output of log file monitoring commands such as grep or awk to other commands such as sort, head, tail, or wc.



Top comments (0)