Use of netstat command
What are indicators to consider to identify suspicious remote hacking activity in the netstat output
How to identify uncommon or unexpected ports for identifying suspicious network activity
write a command High Number of Connections malware attempting in linux server
How to identify unexpected outbound connections may indicate malicious activity
Use of netstat command
The netstat command is a powerful tool for monitoring network activity and troubleshooting network connectivity issues on a Linux system. When used with the -ntp options, netstat provides a comprehensive view of network connections along with the corresponding programs and process identifiers (PIDs). This can be invaluable for identifying suspicious network activity, including potential hacking attempts. Here's how you can use netstat -ntp:
netstat -ntp
Explanation of the command and its options:
netstat: This command is used to display network connections, routing tables, interface statistics, masquerade connections, and multicast memberships.
-n: This option tells netstat to display numerical addresses instead of resolving hostnames. This can speed up the display and can be useful in cases where DNS resolution is slow or unreliable.
-t: This option restricts netstat to displaying TCP connections.
-p: This option instructs netstat to display the PID and name of the program to which each socket belongs.
By running netstat -ntp, you'll get a list of all TCP connections along with their associated programs and PIDs. This information can help you monitor system activity and identify any suspicious connections or processes. For example, if you notice an unexpected program making outbound connections, it could be a sign of unauthorized access or malware.
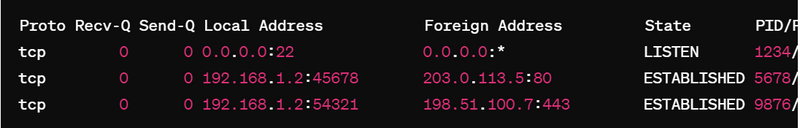
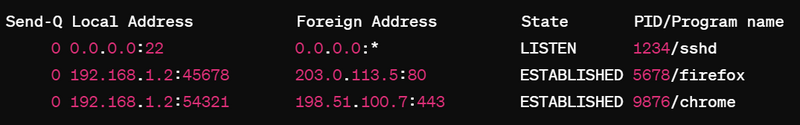
Here's a sample output of netstat -ntp:
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 1234/sshd
tcp 0 0 192.168.1.2:45678 203.0.113.5:80 ESTABLISHED 5678/firefox
tcp 0 0 192.168.1.2:54321 198.51.100.7:443 ESTABLISHED 9876/chrome
- sshd is listening for incoming SSH connections on port 22.
- Firefox has an established connection to an HTTP server on port 80.
- Chrome has an established connection to an HTTPS server on port 443.
- By regularly monitoring netstat -ntp output and investigating any unusual or suspicious connections, you can proactively identify and mitigate potential hacking activity or network connectivity issues on your Linux system.
What are indicators to consider to identify suspicious remote hacking activity in the netstat output
To identify suspicious remote hacking activity in the netstat output, you need to look for anomalies or patterns that deviate from normal behavior. Here are some indicators to consider:
Unusual Ports: Look for connections to uncommon or unexpected ports. For example, connections to well-known ports such as 80 (HTTP) or 443 (HTTPS) are normal for web browsing, but connections to other ports may be suspicious.
Unknown Processes: Check the PID/Program name column for processes that you don't recognize or expect to see. Suspicious processes may have obscure names or names that mimic legitimate system processes.
High Number of Connections: Watch out for processes with a high number of connections, especially if they are connecting to multiple remote addresses. This could indicate a botnet or malware attempting to establish command and control (C&C) connections.
Established Connections to Unusual Addresses: Be wary of connections to foreign addresses that are known for malicious activity, such as IP addresses associated with known botnets or malicious servers.
Outbound Connections from System Processes: While some system processes may legitimately establish outbound connections (e.g., for updates or telemetry), unexpected outbound connections may indicate malicious activity, such as data exfiltration.
Changes in Behavior Over Time: Regularly monitor netstat output over time and look for changes in network activity patterns. Sudden spikes in connections or new types of connections may indicate an ongoing attack.
Based on the provided netstat output:
The SSH daemon (sshd) is listening for incoming connections on port 22, which is normal behavior for SSH server.
There is an established connection from a process named firefox on the local machine (192.168.1.2) to a remote server (203.0.113.5) on port 80 (HTTP), which is likely just web browsing activity.
There is another established connection from a process named chrome on the local machine to a remote server (198.51.100.7) on port 443 (HTTPS), which is also likely just web browsing activity.
In this scenario, the connections appear to be legitimate. However, to identify suspicious activity, you should regularly monitor netstat output for any of the indicators mentioned above and investigate further if any anomalies are detected. Additionally, consider using intrusion detection systems (IDS), firewalls, and other security tools to enhance your network monitoring capabilities.
How to identify uncommon or unexpected ports for identifying suspicious network activity
One way to identify uncommon or unexpected ports for identifying suspicious network activity, including potential hacking attempts, on a Linux server is by using the netstat command along with grep to filter out specific ports. Here's an example:
netstat -tuln | grep -E -v "(^Active|^Proto|^tcp6|^udp6|^tcp|^udp|^unix|^Proto)"
Explanation of the command:
netstat -tuln: This command displays active listening ports (-l), their numerical form (-n), and filters only TCP (-t) and UDP (-u) sockets.
grep -E -v "(^Active|^Proto|^tcp6|^udp6|^tcp|^udp|^unix|^Proto)": This command filters out unwanted lines. -E enables extended regular expressions, and -v inverts the match so that it shows lines that do not match the pattern. The pattern matches lines that start with "Active", "Proto", "tcp6", "udp6", "tcp", "udp", "unix", or "Proto", effectively filtering out the headers and IPv6 entries.
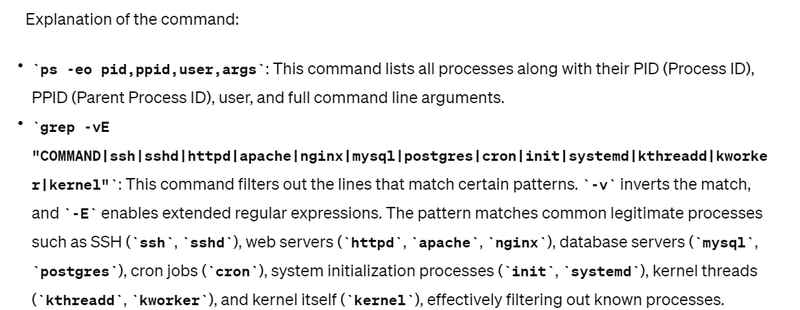
To identify suspicious processes that may have obscure names or names that mimic legitimate system processes for identifying suspicious network activity, you can use the ps command along with grep to filter out processes based on their names or other attributes. Here's an example:
ps -eo pid,ppid,user,args | grep -vE "COMMAND|ssh|sshd|httpd|apache|nginx|mysql|postgre
This command will give you a list of processes that are not commonly associated with standard system services. Processes with obscure names or mimicking legitimate processes may indicate suspicious or unauthorized activity. However, be cautious as some legitimate processes may have unusual names. Further investigation may be required before taking any action.
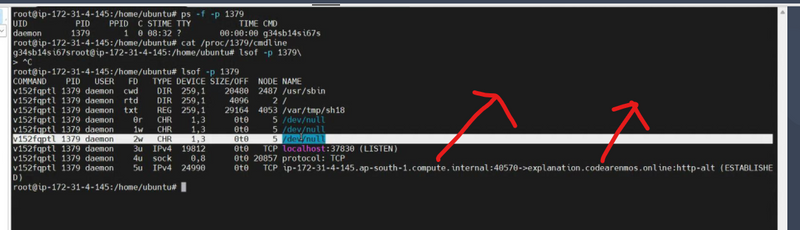
To identify suspicious network activity associated with a specific PID (Process ID) on a Linux server, you can utilize tools like strace or lsof to trace system calls or open files associated with that process. Here's how you can do it:
Using strace:
strace -p <PID>
Replace with the PID of the process you want to monitor.
Explanation:
strace is a system call tracer that allows you to see the system calls made by a process.
-p specifies the PID of the process you want to monitor.
By running strace with the PID of the suspicious process, you'll see a stream of system calls that the process is making. Look for any suspicious network-related system calls, such as attempts to connect to unfamiliar IP addresses or unusual activity.
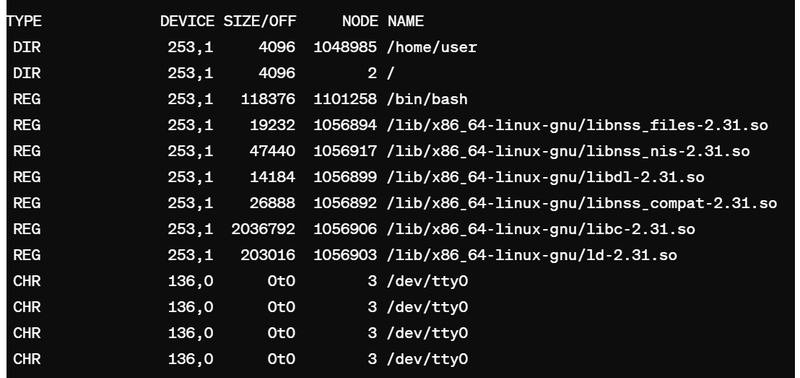
Using lsof:
lsof -p <PID>
Replace with the PID of the process you want to monitor.
Explanation:
lsof (List Open Files) is a command that lists information about files opened by processes.
-p specifies the PID of the process you want to monitor.
By running lsof with the PID of the suspicious process, you'll see a list of files and network connections opened by that process. Look for any suspicious network connections, such as connections to unknown or unauthorized hosts.
Example:
Let's say your suspicious process has a PID of 1379. You can use either strace or lsof to monitor its activity:
strace -p 1379
or
lsof -p 1379
This will provide detailed information about the system calls or open files associated with the process with PID 1379, helping you identify any suspicious network activity, including potential hacking attempts.
lsof -p <PID>
write a command High Number of Connections malware attempting in linux server
To identify a high number of connections, which could be indicative of malware or a potential hacking attempt on a Linux server, you can use the netstat command in combination with sort and uniq to count the number of connections per IP address and then sort them to find the IPs with the highest number of connections. Here's a command to achieve this:
netstat -ntu | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -nr
How to identify unexpected outbound connections may indicate malicious activity
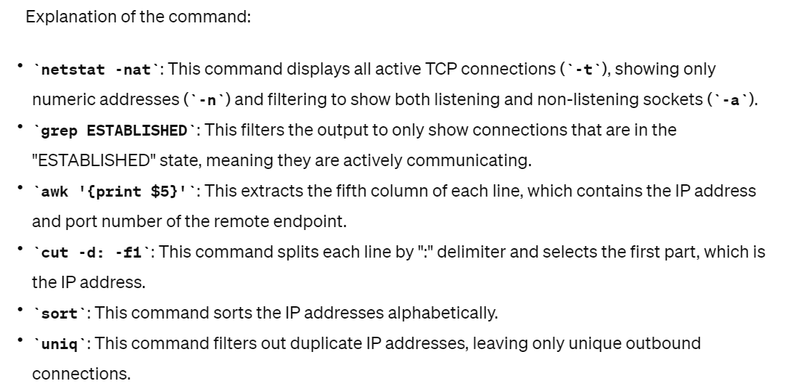
To identify unexpected outbound connections on a Linux server, which may indicate malicious activity, you can use the netstat command along with some filtering options. Specifically, you'll want to focus on outbound connections, as these could indicate unauthorized communication initiated by a potential attacker. Here's a command to achieve this:
netstat -nat | grep ESTABLISHED | awk '{print $5}' | cut -d: -f1 | sort | uniq
By running this command, you'll get a list of unique IP addresses to which outbound connections are established from your server. Reviewing these connections can help identify any unexpected outbound connections, which may be indicative of malicious activity. Further investigation into the purpose and legitimacy of these connections may be necessary to mitigate any potential security risks.
For example, running this command might produce output like:
203.0.113.10
203.0.113.15
192.0.2.20
These IP addresses represent outbound connections from your server. If any of these connections are unexpected or suspicious, you should investigate them further to determine if they pose a security risk.


Top comments (0)