refer
refer2
openssl-decrypt-error-padding-versus-raw
error-error0909006cpem-routinesget-nameno-start-line-node
error-error0909006cpem-routinesget-nameno-start-line-node
Issues 1
C:\openssl rsautl -decrypt -in xxxx_Key -inkey xxxxprivatekey.pem -hexdump -out aeskey.txt
Loading 'screen' into random state - done
RSA operation error
5612:error:0407109F:rsa routines:RSA_padding_check_PKCS1_type_2:pkcs decoding er
ror:.\crypto\rsa\rsa_pk1.c:273:
5612:error:04065072:rsa routines:RSA_EAY_PRIVATE_DECRYPT:padding check failed:.\
crypto\rsa\rsa_eay.c:602:
Solution
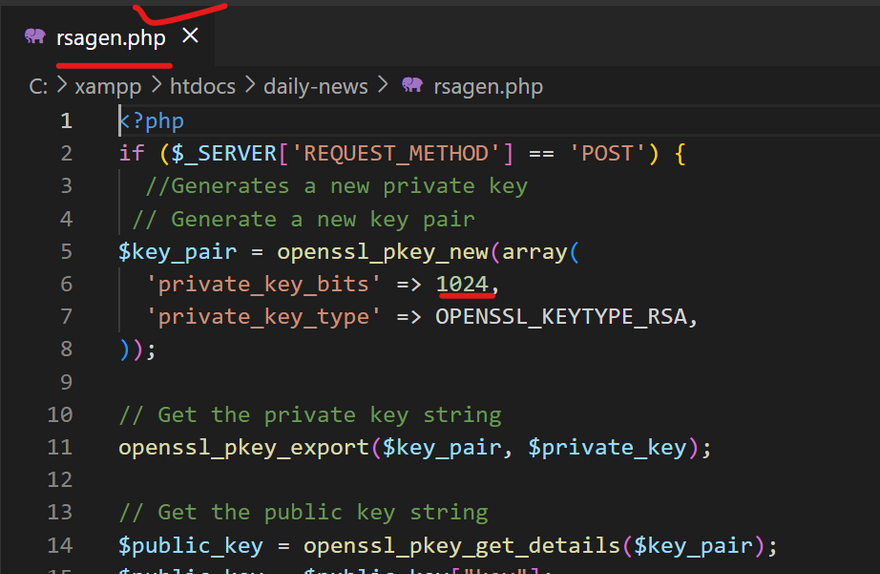
while generating publi and private key mention 1024 bit instead of 2048
My guess is that you are decrypting with the wrong private key or your ciphertext is corrupted.
In RSA, padding is used to extend the length of the message being encrypted to be the same size as the modulus (so 1*024 bit RSA pads messages to 1024 bits*). PKCS1 type 2 is (I believe) another name for PKCS#1 v1.5 which adds the padding 0x00 || 0x02 || (random bytes) || 0x00 to the start of the message. When decrypting the first check that is done is that the start of the message is 0x00 0x02. Then all bytes up to and including the second 0x00 are stripped off, yielding the original message. If the start is not 0x00 0x02 or there is no second 0x00 byte then there is a padding error.
Issues 2
error:0909006C:PEM routines:get_name:no start line
error:0908F066:PEM routines:get_header_and_data:bad end line)
**Solution**
**generate new public and private key and perform encryption and decryption using that keys**
**verify public and private key format see begin line and end line**
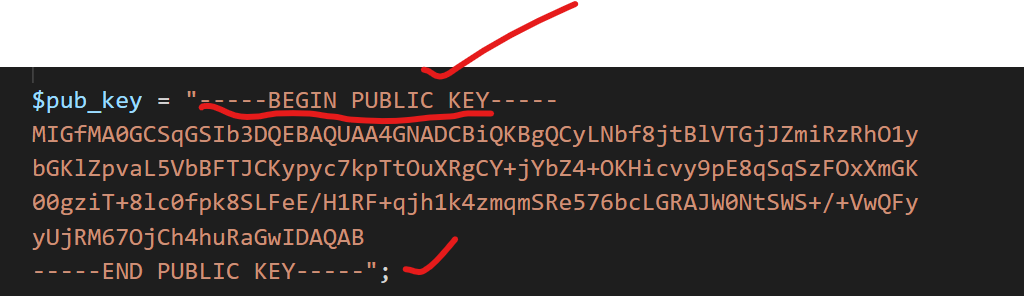
What this typically means is that the PEM file is missing the indicator that the key portion has begun.
PEM files are structured like this:
Intitial Data to be processed
-----Begin <Type>-----
Key Information
-----End <Type>-----
Issues 3
openssl_pkey_export and "cannot get key from parameter 1"
Solution
refer here
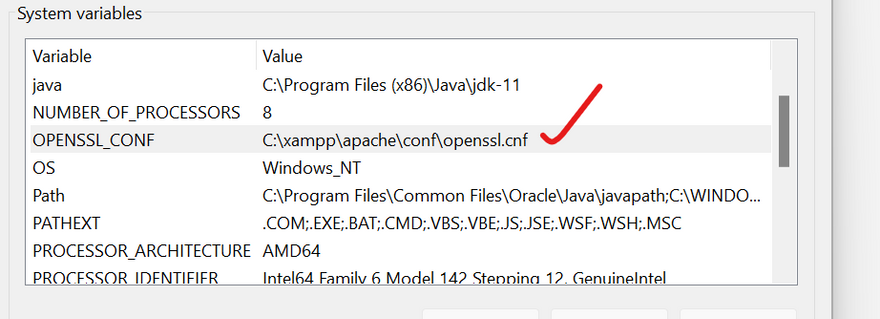
verify environment variable
Issues 4
openssl_private_decrypt(): key parameter is not a valid private key
solution:do not use static public and private key generate using upload or textfield using software as they generate pem extension
Incorrect private key: openssl_private_decrypt requires the private key that corresponds to the public key used to encrypt the data. If you are using a different key to decrypt the data, the decryption will fail. Double-check that you are using the correct private key.
Corrupted data: If the encrypted data is corrupted or modified in some way, the decryption will not work. Ensure that the data is not corrupted or tampered with.
Incorrect padding: openssl_private_decrypt requires the same padding scheme used during encryption. If the wrong padding scheme is used, the decryption will not work. Make sure that the padding scheme used during encryption matches the padding scheme used during decryption.
Insufficient buffer size: The output buffer size used in openssl_private_decrypt must be large enough to hold the decrypted data. If the buffer size is too small, the function will not be able to write all the decrypted data to the buffer, resulting in an incomplete or failed decryption.
Library version: openssl_private_decrypt behavior can vary depending on the version of OpenSSL library used. Make sure you are using the correct version of OpenSSL library that matches the version of the code.
If you suspect that the data you are decrypting using the OpenSSL openssl_private_decrypt function is corrupted, there are several things you can do to verify and potentially fix the issue:
Check the length of the encrypted data: Make sure that the length of the encrypted data you are trying to decrypt is equal to the length of the key used to encrypt it. If the lengths are different, then the data may be corrupted.
Verify the encryption key: Make sure that the private key you are using to decrypt the data is the correct key. If you are using a different key or the wrong key, the decryption process will fail and the data may appear to be corrupted.
Check for padding errors: If the data was encrypted with padding, check to make sure that the padding is correct. If the padding is incorrect, it can cause the data to appear corrupted when you try to decrypt it.
Use error handling: Check for any error messages or return values from the openssl_private_decrypt function. If there is an error, the function will return false and you can use the openssl_error_string() function to get more information about the error.
Verify the data source: Check the source of the encrypted data to make sure that it has not been corrupted or tampered with in transit. This can happen if the data is transmitted over an insecure network or if the storage media used to store the data is unreliable.
Try a different decryption tool: If you have exhausted all other options, you can try using a different decryption tool to see if it can successfully decrypt the data. This can help determine whether the issue is with the data or with the openssl_private_decrypt function.
To verify and potentially fix corrupted data when using openssl_private_decrypt.
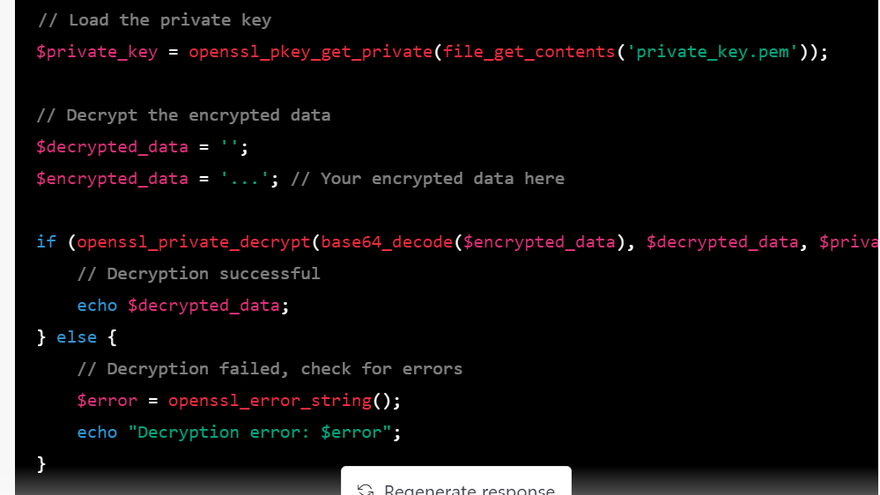
// Load the private key
$private_key = openssl_pkey_get_private(file_get_contents('private_key.pem'));
// Decrypt the encrypted data
$decrypted_data = '';
$encrypted_data = '...'; // Your encrypted data here
if (openssl_private_decrypt(base64_decode($encrypted_data), $decrypted_data, $private_key)) {
// Decryption successful
echo $decrypted_data;
} else {
// Decryption failed, check for errors
$error = openssl_error_string();
echo "Decryption error: $error";
}


Top comments (0)