list-of-setting-in-env-for-production-environment-for-secured-laravel-projects
laravel-security-restricting-uploads-of-php-files-to-your-laravel-public-directory
Securing a Laravel project involves implementing a number of best practices to protect the application from various types of attacks, such as SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more.
Keep your Laravel framework and dependencies up to date
Use encryption for sensitive data
Validate user input
Protect against SQL injection attacks
Protect against cross-site scripting (XSS) attacks
Protect against cross-site request forgery (CSRF) attacks
Use HTTPS for secure communication
Configure authentication and authorization
Use security-focused packages
Monitor logs and monitor application behavior
Perform regular security audits
Here is a detailed checklist to secure your Laravel project:
1.Keep your Laravel framework and dependencies up to date: Regularly updating the Laravel framework and dependencies helps you fix security vulnerabilities and improve performance.
2.Use encryption for sensitive data: Use Laravel’s encryption facilities, such as the bcrypt hashing algorithm, to securely store sensitive data, such as passwords, in the database.
3.Validate user input: Use Laravel’s built-in validation rules to validate user input and prevent malicious data from being entered into the application.
4.Protect against SQL injection attacks: Use Laravel’s query builder and ORM to build database queries, as they automatically escape user input and prevent SQL injection attacks.
5.Protect against cross-site scripting (XSS) attacks: Laravel provides several ways to protect against XSS attacks, such as using the e() function to escape output, using blade templates, and using the XSS middleware.
6.Protect against cross-site request forgery (CSRF) attacks: Laravel protects against CSRF attacks by automatically including a CSRF token in all non-GET requests, which must be verified on the server before processing the request.
7.Use HTTPS for secure communication: Use HTTPS for secure communication between the client and server to prevent eavesdropping and tampering with the data in transit.
8.Configure authentication and authorization: Use Laravel’s authentication and authorization features to control access to resources in the application and prevent unauthorized access.
9.Use security-focused packages: Use security-focused packages, such as the paragonie/security-advisories package, to monitor security vulnerabilities in your dependencies.
10.Monitor logs and monitor application behavior: Regularly monitor the application’s logs and behavior to detect any unusual activity that may indicate a security breach.
11.Perform regular security audits: Regularly perform security audits of your application to identify potential security vulnerabilities and fix them before they can be exploited.
Use encryption for sensitive data
In Laravel, you can use the Crypt facade to securely store sensitive data in the database. Here's an example of how to use it:
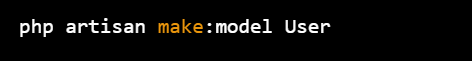
1.First, you need to create a model for your data. Let's say you want to store a user's password, you can create a model named User:
php artisan make:model User
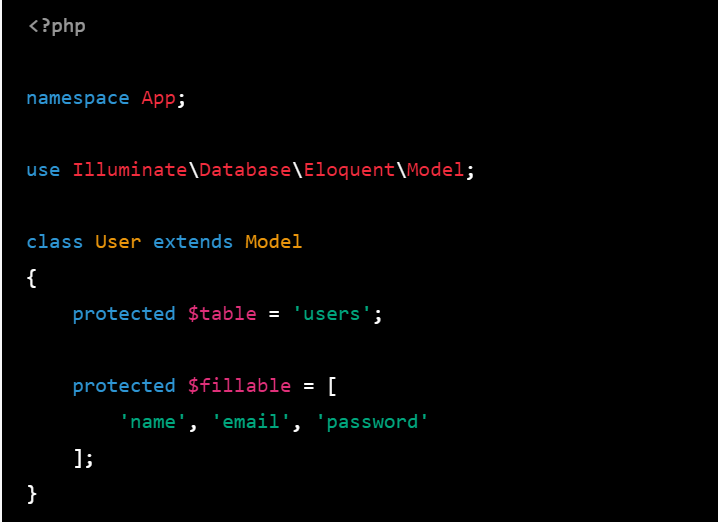
2.In the User model, you can define the table name and the columns that you want to store in the database:
<?php
namespace App;
use Illuminate\Database\Eloquent\Model;
class User extends Model
{
protected $table = 'users';
protected $fillable = [
'name', 'email', 'password'
];
}
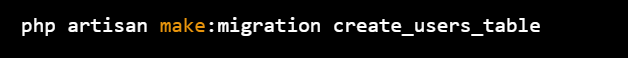
3.Next, you need to create a migration to create the users table in the database:
php artisan make:migration create_users_table
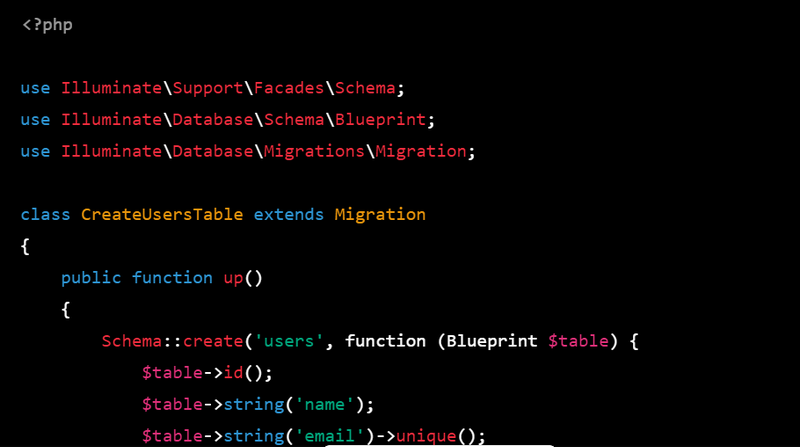
4.In the migration file, you can define the columns for the users table:
<?php
use Illuminate\Support\Facades\Schema;
use Illuminate\Database\Schema\Blueprint;
use Illuminate\Database\Migrations\Migration;
class CreateUsersTable extends Migration
{
public function up()
{
Schema::create('users', function (Blueprint $table) {
$table->id();
$table->string('name');
$table->string('email')->unique();
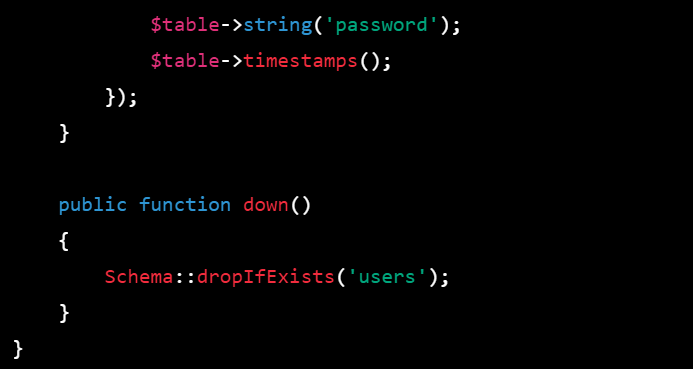
$table->string('password');
$table->timestamps();
});
}
public function down()
{
Schema::dropIfExists('users');
}
}
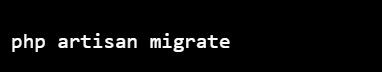
5.You can then run the migration to create the users table in the database:
php artisan migrate
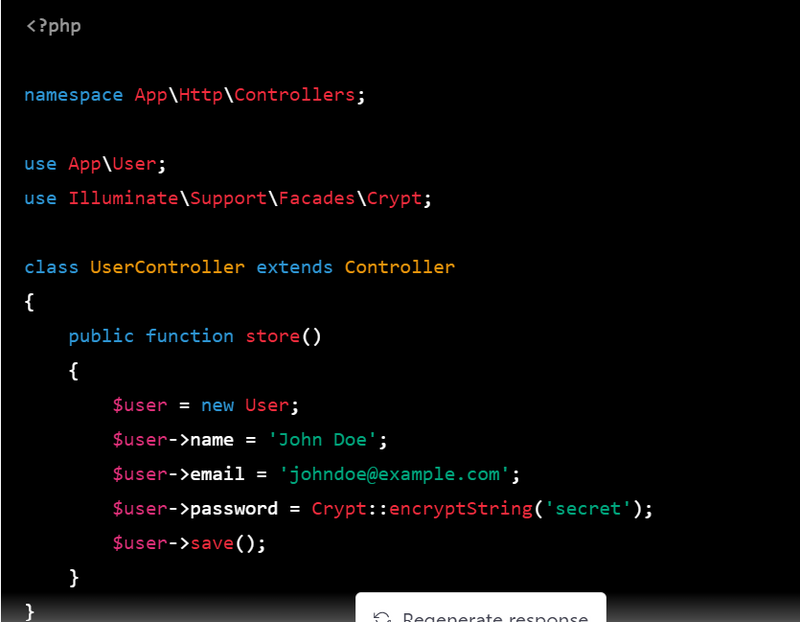
6.Now that the users table has been created, you can use the Crypt facade to encrypt the user's password before storing it in the database:
<?php
namespace App\Http\Controllers;
use App\User;
use Illuminate\Support\Facades\Crypt;
class UserController extends Controller
{
public function store()
{
$user = new User;
$user->name = 'John Doe';
$user->email = 'johndoe@example.com';
$user->password = Crypt::encryptString('secret');
$user->save();
}
}
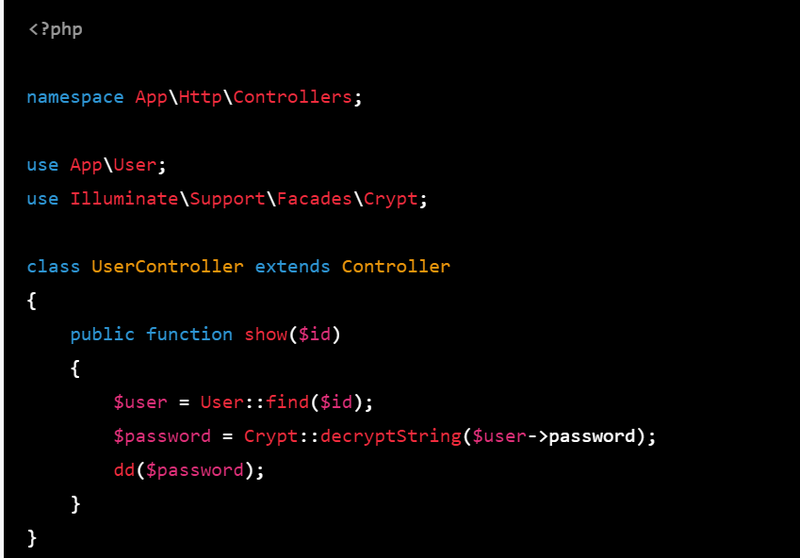
7.To retrieve the user's password from the database, you can use the Crypt facade's decryptString method:
<?php
namespace App\Http\Controllers;
use App\User;
use Illuminate\Support\Facades\Crypt;
class UserController extends Controller
{
public function show($id)
{
$user = User::find($id);
$password = Crypt::decryptString($user->password);
dd($password);
}
}
Note that Laravel's encryption facilities use AES-256 encryption, which is considered to be a secure encryption method.
Laravel provides several ways to securely store sensitive data in the database, one of which is through encryption. Here is an example of how to use Laravel's encryption facilities to store passwords in the database:
1.Set up a database connection: You'll need to have a database set up in Laravel and configure your .env file with the appropriate credentials.
2.Create a model: In Laravel, you can create a model to represent a table in your database. For example, you could create a User model to represent a users table.
php artisan make:model User
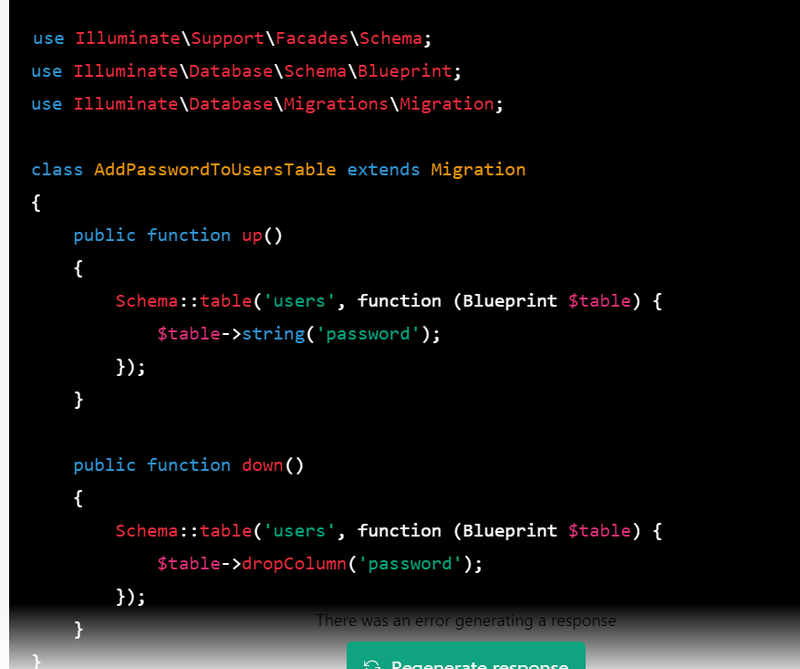
3.Create a migration: Next, create a migration to add the password field to the users table.
php artisan make:migration add_password_to_users_table --table=users
4.Define the password field in the migration: In the generated migration file, define the password field and set its type to string
use Illuminate\Support\Facades\Schema;
use Illuminate\Database\Schema\Blueprint;
use Illuminate\Database\Migrations\Migration;
class AddPasswordToUsersTable extends Migration
{
public function up()
{
Schema::table('users', function (Blueprint $table) {
$table->string('password');
});
}
public function down()
{
Schema::table('users', function (Blueprint $table) {
$table->dropColumn('password');
});
}
}
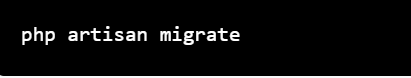
5.Run the migration: Run the migration to create the password field in the users table.
php artisan migrate
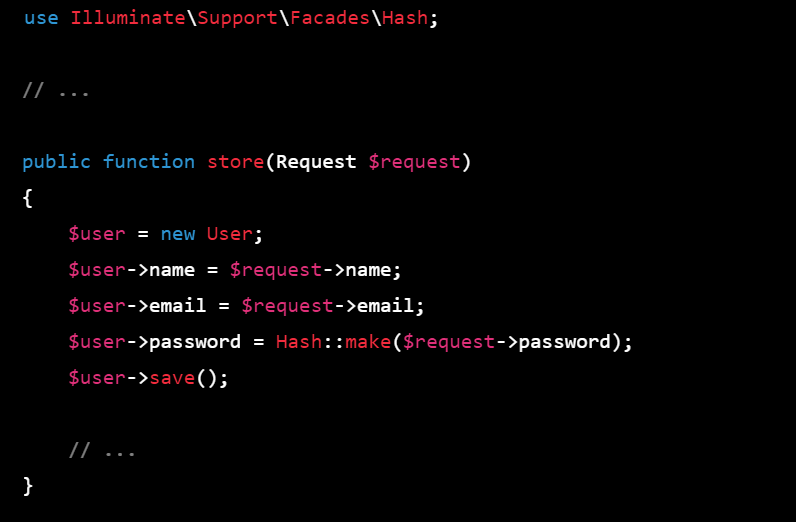
6.Encrypt the password before storing it: In your controller or model, use the bcrypt function to encrypt the password before storing it in the database.
use Illuminate\Support\Facades\Hash;
// ...
public function store(Request $request)
{
$user = new User;
$user->name = $request->name;
$user->email = $request->email;
$user->password = Hash::make($request->password);
$user->save();
// ...
}
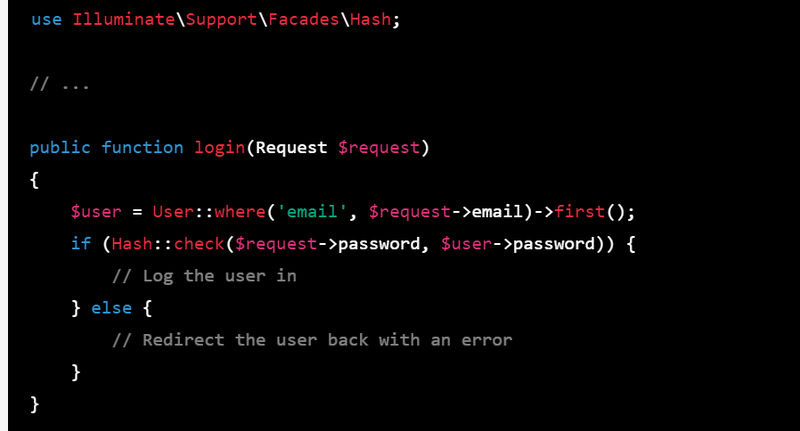
7.Verify the password on login: To verify the password on login, you can use the Hash facade's check method.
use Illuminate\Support\Facades\Hash;
// ...
public function login(Request $request)
{
$user = User::where('email', $request->email)->first();
if (Hash::check($request->password, $user->password)) {
// Log the user in
} else {
// Redirect the user back with an error
}
}
This is just an example of how to use Laravel's encryption facilities to store passwords in the database. You can adapt this example to store other types of sensitive data as well.
Validate user input
Validating user input is an important step in securing your Laravel project. By validating user input, you can ensure that the data being entered into your application is of the correct type and format, and meets your specified requirements.
Here's an example of how you can validate user input in Laravel:
1.Create a new controller using the following command:
php artisan make:controller UserController
2.In your UserController, you can create a new method for handling user input validation. For example:
public function store(Request $request)
{
$validatedData = $request->validate([
'email' => 'required|email',
'password' => 'required|min:8',
]);
// Save the validated data to the database or process it as needed
// ...
}
In the code above, the validate method of the $request object is used to validate the user input. The validate method takes an array of validation rules as its argument. In this example, we're validating that the email field is present, is an email address, and that the password field is present and at least 8 characters long.
3.In your routes file, you can define a new route to the store method of the UserController:
Route::post('/users', [UserController::class, 'store']);
4.If the validation fails, Laravel will automatically redirect the user back to the previous page and display the validation errors. You can customize the error messages by creating a new resources/lang/en/validation.php file and adding the following code:
return [
'required' => 'The :attribute field is required',
'email' => 'The :attribute must be a valid email address',
'min' => 'The :attribute must be at least :min characters',
];
In the code above, we've customized the error messages for the required, email, and min validation rules.
By following these steps, you can validate user input and secure your Laravel project.
Protect against SQL injection attacks
SQL injection is a type of security vulnerability that can occur in web applications when user-supplied data is used to dynamically construct a SQL query. This can allow attackers to execute arbitrary SQL commands on the database, potentially leading to data theft or destruction.
Here are some ways to protect against SQL injection attacks in a Laravel project:
1.Use Parameter Binding: Laravel provides a convenient way to bind parameters to your SQL statements using parameter binding. This ensures that user-supplied data is properly escaped and sanitized, preventing SQL injection attacks.
Example:
$users = DB::select('select * from users where name = :name', ['name' => $name]);
2.Escaping User Input: You can also use Laravel's $request object to escape user-supplied data. The $request object provides a validate method that can be used to validate user input and automatically escape any untrusted data.
$validatedData = $request->validate([
'title' => 'required|string|max:255',
'body' => 'required|string',
]);
3.Use Eloquent ORM: Laravel's Eloquent ORM provides a convenient way to interact with databases using an object-oriented syntax. Eloquent automatically escapes any user-supplied data, preventing SQL injection attacks.
$user = User::where('name', $name)->first();
4.Use Stored Procedures: Stored procedures are precompiled SQL statements that can be executed on a database server. When using stored procedures, user-supplied data is automatically escaped, preventing SQL injection attacks.
$users = DB::select('exec GetUsersByName ?', [$name]);
5.Whitelist Input Data: Another way to protect against SQL injection attacks is to only accept data that matches a predetermined set of acceptable values. This is often referred to as "whitelisting".
$validatedData = $request->validate([
'sort' => ['required', Rule::in(['asc', 'desc'])],
]);
By following these best practices, you can help protect your Laravel project against SQL injection attacks and keep your data secure.
Monitoring logs and application
Logging: Laravel provides a powerful logging system that allows you to log application events and errors. You can configure the log channel in the config/logging.php file. Here's an example:
'channels' => [
'stack' => [
'driver' => 'stack',
'channels' => ['single', 'slack'],
],
'single' => [
'driver' => 'single',
'path' => storage_path('logs/laravel.log'),
'level' => 'debug',
],
'slack' => [
'driver' => 'slack',
'url' => env('SLACK_WEBHOOK_URL'),
'username' => 'Laravel Bot',
'emoji' => ':boom:',
'level' => 'critical',
],
],
In the above example, the stack channel logs events to both the single and slack channels. The single channel logs events to a file, and the slack channel sends notifications to a Slack webhook.


Top comments (0)