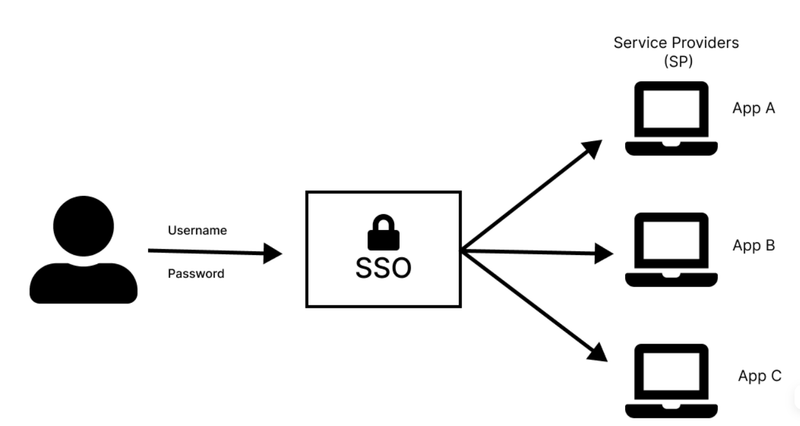
What is SSO
Step-by-Step SSO Workflow
Common SSO Protocols
Key Benefits of SSO
Summary
Architecture of SSO
real time example of SSO Implementation
Architecture Flow
What is SSO
Single Sign-On (SSO) is an authentication method that enables users to log in once with a single set of credentials (username and password) and gain access to multiple applications or systems without having to log in again for each one. It streamlines user management, enhances security, and improves user experience in organizations where users need to access several applications.
developer-guide-implementing-sso
EXAMPLE
Step-by-Step SSO Workflow
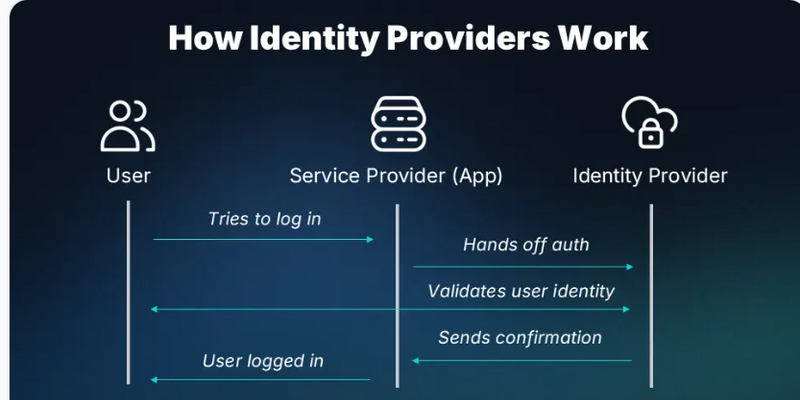
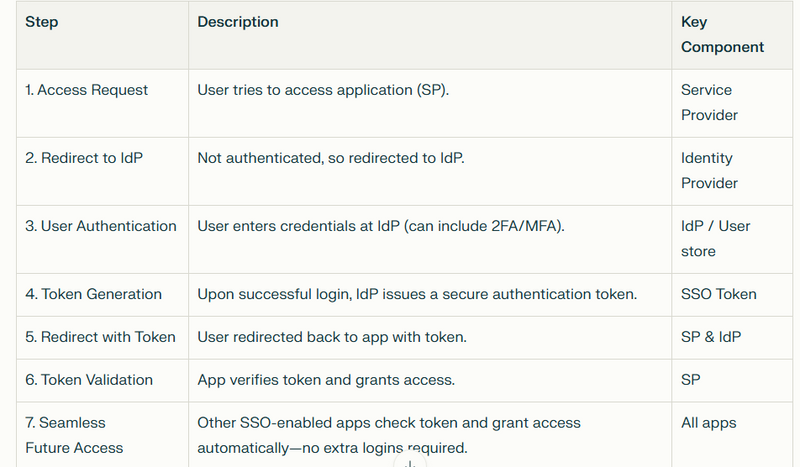
User Attempts to Access a Secure Application
The user tries to open an application (called a "Service Provider" or SP).
The application checks if the user is already authenticated in the current session.
Redirect to Identity Provider (IdP)
If the user is not authenticated, the application redirects the user's browser to a central SSO authentication server, called the Identity Provider (IdP).
The redirect usually includes information about the original app the user tried to access.
User Authenticates with the IdP
The IdP displays a login page, prompts the user for credentials (like username and password), and may ask for additional authentication such as Two-Factor Authentication (2FA) if enabled.
The user's credentials are checked against a user database (like LDAP, Active Directory, etc.).
Token Generation Upon Successful Authentication
Once authenticated, the IdP creates a security token (SSO token), digitally signed or encrypted for security.
This token contains identity information (username, email, etc.) and proof of authentication.
Redirect Back to the Service Provider
The user is redirected (often automatically) back to the original application (SP), along with the SSO token.
Token Validation by the Application
The SP validates the SSO token, checks its authenticity, and verifies that it has not been tampered with.
If valid, the application grants the user access. Typically, the user's session is established at this point.
Seamless Access to Other Connected Applications
Any additional SSO-integrated applications the user tries to access will follow the same redirection process.
Since the user is already authenticated, these other apps will immediately accept the SSO token and grant access without repeated logins.
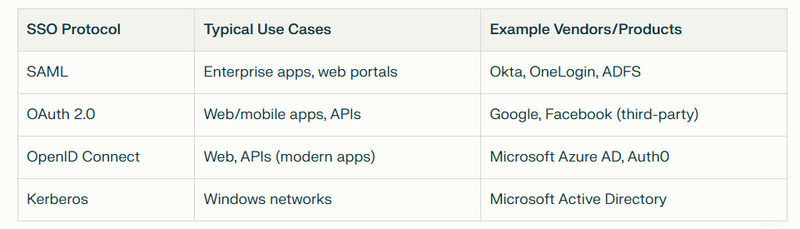
Common SSO Protocols
SAML(Security Assertion Markup Language): Widely used in enterprise environments for browser-based SSO.
OAuth 2.0: Popular for web/mobile app SSO and API access.
OpenID Connect (OIDC): Identity layer on top of OAuth 2.0, used for authentication and basic profile info.
Kerberos: Used in Windows environments and some enterprise networks.
Key Benefits of SSO
Enhanced User Experience: No need to remember multiple passwords or log in repeatedly.
Improved Security: Centralized credential management and auditing.
Reduced IT Overhead: Fewer password reset requests and easier user provisioning.
Summary
SSO allows one-time authentication for access to many applications.
It relies on a trust relationship between service providers (apps) and a central identity provider (IdP).
Tokens are central to SSO—they securely share proof of authentication between sites.
SSO enhances the convenience, security, and manageability of user access.
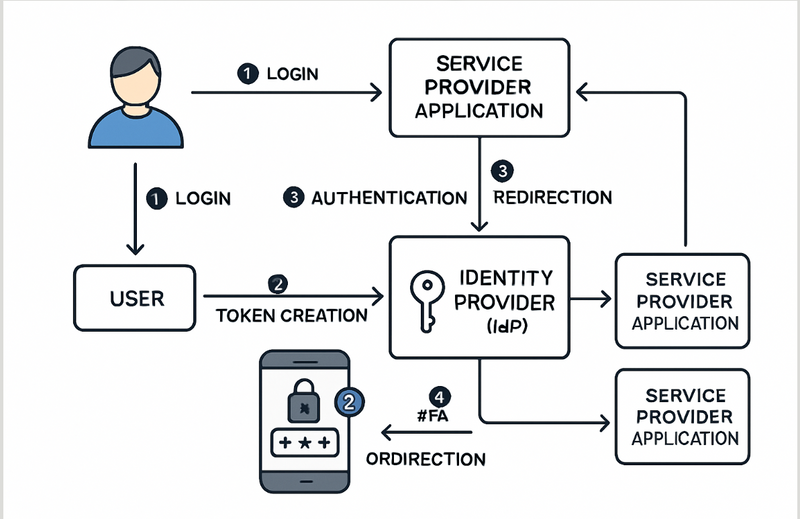
Architecture of SSO
Step-by-Step Breakdown
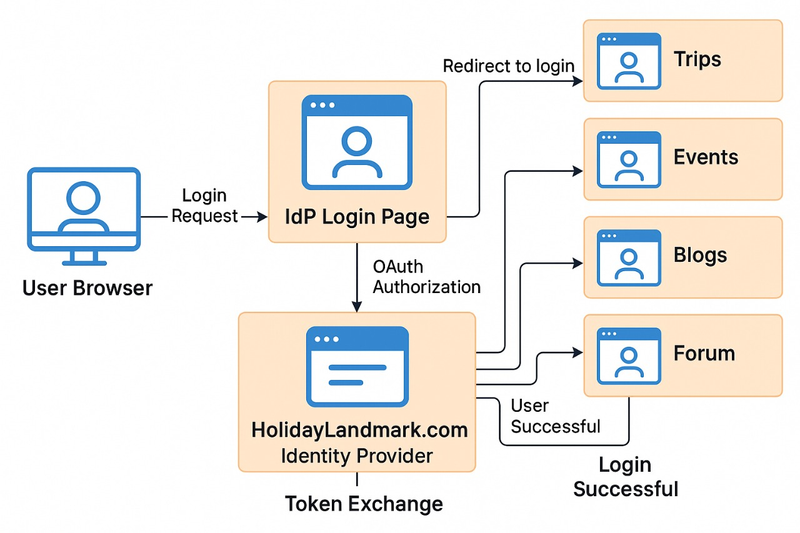
User Initiates Access
The user tries to open a secure application (known as a Service Provider, or SP).
The browser sends an access request to the application.
Service Provider Checks Authentication
The application checks if the user is already authenticated within the current session.
If not, the application redirects the user’s browser to the Identity Provider (IdP).
Redirection to Identity Provider (IdP)
The browser is automatically redirected to an IdP.
The request includes context, such as the original application’s identity and the resource URL.
User Authenticates with IdP
The IdP presents a login prompt.
The user enters their credentials (username, password, and potentially a second factor).
The IdP validates these credentials against a central user directory (like Active Directory or LDAP).
Identity Provider Generates Security Token
Once credentials are verified, the IdP creates a digitally-signed security token.
This token contains the user’s identity and proof of authentication.
Redirection Back to Service Provider
The IdP redirects the browser back to the Service Provider.
The security token is passed in this redirection, typically through the browser.
Service Provider Validates Token
The Service Provider receives the token and verifies its authenticity and integrity.
If the token is valid and matches expected parameters, the user is considered authenticated.
User Access is Granted
The application grants access to the user.
The user now has a session with the application.
Seamless Access to Additional Applications
If the user accesses another SSO-enabled application:
The process repeats steps 2–7.
However, since the user is already authenticated with the IdP, no new login is required.
The user gains immediate access.
real time example of SSO Implementation
Google Account Across Google Services
Description: When a user logs into their Google Account, they gain seamless access to services like Gmail, Google Drive, YouTube, Google Photos, and Google Maps without repeated logins.
Benefit: Streamlines user experience and cuts down on password-related support issues.
Facebook Login for Third-Party Applications
Description: Many websites and mobile apps allow users to sign in using Facebook credentials. Once authenticated by Facebook, users access these third-party platforms without creating separate accounts.
Benefit: Simplifies onboarding for end-users and leverages Facebook’s secure authentication infrastructure.
Microsoft 365 Integration in Enterprises
Description: Organizations utilize Microsoft 365 SSO so employees can access Outlook, Teams, SharePoint, and other Microsoft services with a single corporate login.
Benefit: Reduces password fatigue, centralizes user management, and increases productivity.
Salesforce and Other Enterprise Apps
Description: Employees at companies using Salesforce can log in once and are instantly authenticated for connected apps such as Slack, Workday, Oracle, or custom HR and finance applications.
Benefit: Offers secure, streamlined access to essential business platforms.
Healthcare Systems (Hospital Networks)
Description: Medical staff log in once to a hospital’s identity portal, then seamlessly access patient records, medical imaging, billing, scheduling, and laboratory results across different clinical systems.
Benefit: Ensures compliance (e.g., HIPAA), saves time, and reduces the risk of password-related breaches
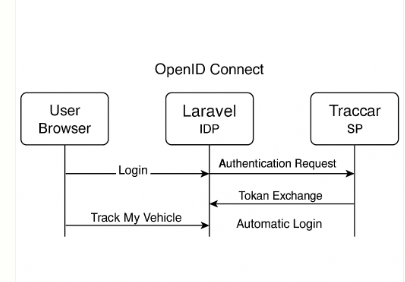
ARHITECTURE FLOW
Below is an architecture diagram (described step-by-step) for your SSO integration where Traccar (Service Provider – SP) uses Laravel as the Identity Provider (IDP). When a user logs in via Laravel and clicks “Track My Vehicle”, they’re automatically logged in to Traccar without re-entering credentials.
Architecture & SSO Flow
Components:
Laravel (IDP): Authenticates user, issues tokens.
Traccar (SP): Accepts authentication via OpenID Connect (OIDC).
User Browser: Initiates login and “Track My Vehicle” action.
User Login and SSO Initiation
User logs in to the Laravel dashboard (https://motoshare.jp).
On the dashboard, there is a button/link:
<a href="https://traccar.motoshare.in/login">Track My Vehicle</a>
Clicking it directs the browser to Traccar’s /login page (https://traccar.motoshare.in/login), which starts the OpenID Connect login process.
OIDC Authentication (Traccar as SP)
Traccar’s config tells it to use OpenID Connect SSO (see your XML):
openid.force=true: Always require OpenID login.
Traccar is registered with these properties:
clientId, clientSecret
issuerUrl, authUrl, tokenUrl, userInfoUrl
Traccar immediately redirects to Laravel’s authUrl (https://motoshare.jp/oauth/authorize) for authentication.
Laravel (IDP) Authenticates & Issues Token
Since user is already logged in to Laravel, the IDP issues an authorization code (or JWT access/ID tokens if Implicit/Hybrid flow).
The browser is redirected back to Traccar’s callback endpoint, with:
Authorization code (or token) in query
Traccar Exchanges Code for User Data
Traccar calls Laravel’s tokenUrl to exchange code for access/id tokens.
Next, Traccar calls userInfoUrl with the access token to get user profile details (name, email, etc.).
Traccar Automatically Logs User In
Traccar creates/updates a user session based on profile information received.
User is redirected and logged in to Traccar dashboard (https://traccar.motoshare.in), mapped to the same authenticated identity as in Laravel.

Top comments (0)