The role of full chain
explanation of Certificate Hierarchy in SSL/TLS
Error:Exception: HandshakeException: Handshake error in client (OS Error:
CERTIFICATE_VERIFY_FAILED: unable to get local issuer
The role of full chain
full chain SSL certificate is required to ensure that browsers, servers, and other clients can trust the certificate provided by your website or application. Here’s a detailed explanation of why the full chain is needed:
Certificate Hierarchy in SSL/TLS
SSL/TLS certificates operate in a chain of trust, consisting of:
Root Certificate: Issued by a trusted Certificate Authority (CA). These are pre-installed in browsers, operating systems, and devices.
Intermediate Certificates: Issued by the Root CA and used to issue end-user SSL certificates. They serve as a link between the Root and the end-user certificate.
End-User Certificate: The certificate for your specific domain.
The browser or client must validate this chain of trust to confirm the legitimacy of the SSL certificate presented by the server.
The Role of the Full Chain
When a server presents only the end-user certificate during the SSL handshake, the client cannot verify its authenticity unless it also has access to the intermediate and root certificates. This is why the full chain (end-user certificate + intermediate certificates) is required.
The full chain certificate ensures:
The end-user certificate is linked to an intermediate certificate.
The intermediate certificate is linked to a trusted root certificate in the client’s trust store.
Without the full chain, the client may fail to establish trust and throw errors like "Untrusted Certificate" or "Invalid Certificate Authority."
-
Key Reasons for Requiring the Full Chain
Trust Validation: Ensures the client can trace the certificate’s trust back to a trusted root CA.Compatibility: Not all clients or browsers fetch intermediate certificates automatically. Providing the full chain ensures compatibility across diverse platforms and devices.Security: Strengthens the trust model by properly linking all components in the chain.Avoiding Errors: Prevents "certificate not trusted" errors due to missing intermediate certificates. - Example of a Full Chain A full chain SSL certificate bundle typically includes:
Your domain’s SSL certificate (end-user certificate).
One or more intermediate certificates that connect the domain certificate to the root CA certificate.
Optionally, the root certificate (though it's usually not included because clients already trust root certificates from known CAs).
When configured correctly, the server delivers this chain during the handshake, ensuring the client can verify the certificate.
- Conclusion A full chain SSL certificate is required because it enables the client to establish a complete and trusted chain of trust back to the root CA. Omitting intermediate certificates breaks this chain, causing trust issues and errors during SSL connections.
Explanation of Certificate Hierarchy in SSL/TLS
To understand Root Certificate, Intermediate Certificates, and End-User Certificate, let’s break them down with examples and their roles in the SSL/TLS Certificate Chain of Trust.
-
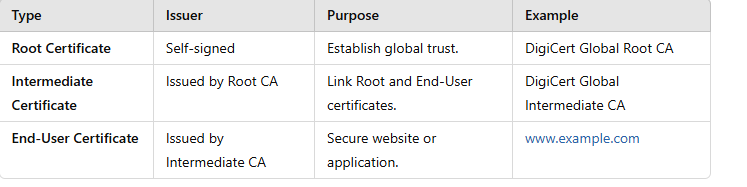
Root Certificate
Definition: The Root Certificate is the top-most certificate in the chain of trust. It is issued and signed by a trusted Certificate Authority (CA). These root certificates are pre-installed in operating systems, browsers, and devices.Key Features:
- Self-signed: The CA signs its own root certificate.
- Rarely used directly to issue end-user certificates.
- Must be kept secure by the CA because compromising it could break trust for all certificates issued under it . Example:
A root certificate issued by DigiCert might look like this:
DigiCert Global Root CA
Issued by: DigiCert Global Root CA
Validity: 2013-11-10 to 2038-01-15
How it works:
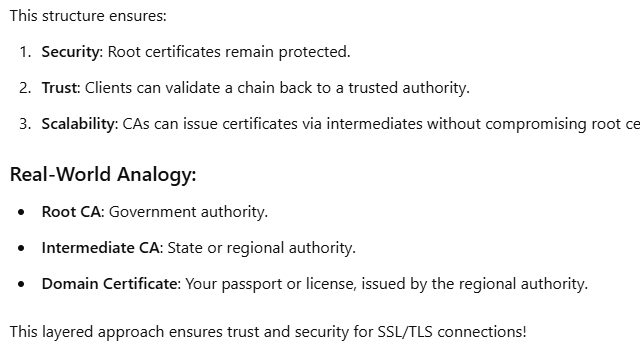
Root certificates are distributed to client systems and browsers as part of their trusted certificate store. If a certificate can be traced back to a root in this store, it is trusted.
-
Intermediate Certificates
Definition: Intermediate certificates link the Root Certificate to the End-User Certificate. They are issued by the Root CA or another Intermediate CA and act as a middle layer of trust.Key Features: Reduce the risk of exposing the Root Certificate. Allow the CA to revoke specific intermediates without affecting the Root Certificate. There can be one or more intermediate certificates in the chain. Example:
Intermediate certificates issued under DigiCert might look like this:
DigiCert Global Intermediate CA
Issued by: DigiCert Global Root CA
Validity: 2013-11-10 to 2038-01-15
How it works:
During the SSL handshake, the server provides the intermediate certificate(s) to help the client complete the chain of trust.
-
End-User Certificate
Definition: This is the certificate issued for a specific domain or entity, such as your website. It is the certificate that your server presents to clients during the SSL handshake.Key Features: Signed by an intermediate certificate, not directly by the root. Contains information like the domain name, public key, and validity period. Example:
An end-user certificate for example.com:
Common Name: www.example.com
Issued by: DigiCert Global Intermediate CA
Validity: 2024-01-01 to 2025-01-01
How it works:
This certificate proves your website's identity to visitors. It is used in the encryption and decryption process during an HTTPS connection.
SSL Chain of Trust Example
Imagine the following scenario:
Root Certificate:
DigiCert Global Root CA
Self-signed and pre-installed in browsers/OS
.
Intermediate Certificate:
DigiCert Global Intermediate CA
Signed by DigiCert Global Root CA.
End-User Certificate:
Domain: www.example.com
Signed by DigiCert Global Intermediate CA.
Chain of Trust:
When a client connects to www.example.com, the following steps occur:
- The server presents the End-User Certificate for www.example.com.
- The client checks the Intermediate Certificate (provided by the server) to verify it was issued by the Root Certificate.
- The client validates the Root Certificate (already in the trust store) and completes the chain of trust .
Exception: HandshakeException: Handshake error in client (OS Error:
I/flutter (12714): CERTIFICATE_VERIFY_FAILED: unable to get local issuer
Solution : apply full chain on ssl certificate

Top comments (0)