Laravel can function as an Identity Provider (IdP) for Single Sign-On (SSO) using industry-standard protocols like OAuth2/OpenID Connect or SAML 2.0. The most common approach utilizes Laravel Passport (for OAuth2/OIDC) or packages for SAML. Below is a step-by-step guide using Laravel Passport, which is ideal for most modern applications.
Install Laravel Passport
Run from your Laravel project root:
composer require laravel/passport
Run migrations to create necessary tables:
php artisan migrate
Install Passport:
php artisan passport:install
This will generate encryption keys and default clients.
Configure Passport in AuthServiceProvider
Edit app/Providers/AuthServiceProvider.php:
use Laravel\Passport\Passport;
public function boot(): void
{
$this->registerPolicies();
Passport::tokensCan([
'openid' => 'Basic OpenID scope',
'profile' => 'Profile scope',
'email' => 'Email scope',
]);
// (optionally)
Passport::setDefaultScope([
'openid',
'profile',
'email',
]);
}
Set Auth Guard to Use Passport
Edit config/auth.php and update the guards array:
php
'guards' => [
'web' => [
'driver' => 'session',
'provider' => 'users',
],
'api' => [
'driver' => 'passport',
'provider' => 'users',
],
],
In routes/api.php
remove auth sanctum
Route::middleware('auth:api')->get('/user', function (Request $request) {
$user = $request->user();
\Log::info('Traccar OIDC /api/user called', [
'token' => $request->bearerToken(),
'user' => $user
]);
if ($user) {
\Log::info('Traccar OIDC sub claim', ['sub' => $user->id]);
// Always use response()->json() for strict JSON object
return response()->json([
'sub' => strval($user->id), // make it a string as per OIDC spec
'name' => $user->name,
'email' => $user->email,
]);
} else {
\Log::error('Traccar OIDC: No user found for token!', [
'token' => $request->bearerToken()
]);
return response()->json([
'error' => 'No user found',
'sub' => null
], 401);
}
});
in routes/web.php configure
Route::get('/.well-known/openid-configuration', function () {
return response()->json([
"issuer" => "http://127.0.0.1:8000/",
"authorization_endpoint" => "http://127.0.0.1:8000/oauth/authorize",
"token_endpoint" => "http://127.0.0.1:8000/oauth/token",
"userinfo_endpoint" => "http://127.0.0.1:8000/api/user",
"jwks_uri" => "http://127.0.0.1:8000/.well-known/jwks.json",
"response_types_supported" => ["code", "token"],
"subject_types_supported" => ["public"],
"id_token_signing_alg_values_supported" => ["RS256"],
"scopes_supported" => ["openid", "profile", "email"],
"token_endpoint_auth_methods_supported" => ["client_secret_post"],
"grant_types_supported" => ["authorization_code", "refresh_token"]
]);
});
Route::get('/.well-known/jwks.json', function () {
return response()->json([
"keys" => []
]);
});
Configure Personal Access Client (Optional for OIDC)
If your Service Provider (SP, i.e., other app) will use OAuth/OIDC, create a client for it:
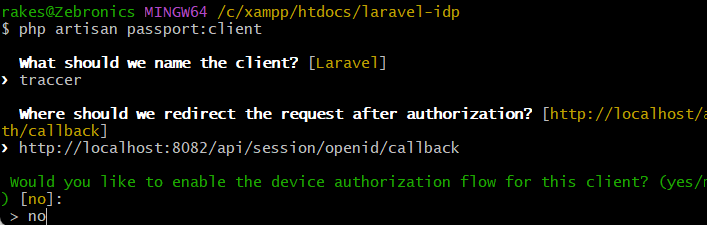
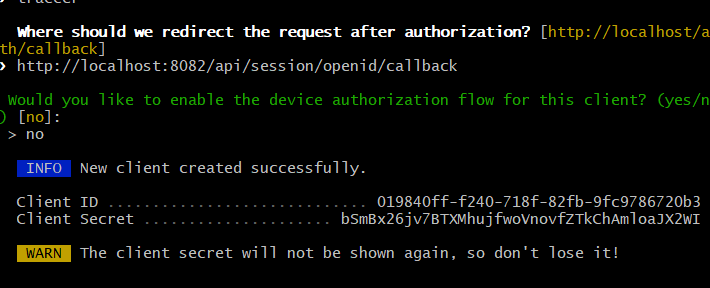
php artisan passport:client
Choose "authorization code" grant option for web apps, and note Client ID and Secret.
after running above command u have to type
Would you like to create the "personal access" grant client? (yes/no) [yes] ==type no
then type
Name: Traccar (application name)
Redirect URI: https://YOUR_TRACCAR_SERVER/api/session/openid/callback (replace with your actual Traccar URL)
http://localhost:8082/api/session/openid/callback
============================================================
composer create-project laravel/laravel laravel-idp
cd laravel-idp
C:\xampp\php\php.ini
;extension=sodium
extension=sodium
in env==specify database then phpartisan optimize
composer require laravel/passport:^13.0 --with-all-dependencies
php artisan passport:install
Would you like to create the "personal access" grant client? (yes/no) [yes] ==type no
php artisan passport:client
Name: Traccar GPS SP
Redirect URI: https://YOUR_TRACCAR_SERVER/api/session/openid/callback (replace with your actual Traccar URL)
http://localhost:8082/api/session/openid/callback
=====================================================

Top comments (0)